A cross-site request forgery (CSRF) vulnerability in the web interface of the device allows attackers to perform an unauthorized login by tricking users into performing certain actions. An attacker can trick a user into performing a CSRF attack by either manipulating the way the link is displayed or by posing as a trustworthy source of information.
An attacker can exploit this cross-site request forgery (CSRF) vulnerability by sending a crafted request to the targeted device. The request can be sent via an email or a website link. The request can also be sent via a message app on the targeted device.
A cross-site scripting (XSS) vulnerability in the web interface of the device allows attackers to inject arbitrary web script or HTML via the device's web interface. An attacker can exploit this XSS vulnerability by sending a crafted request to the targeted device. The request can be sent via an email or a website link. The request can also be sent via a message app on the targeted device.
An attacker can exploit a missing patch for the SSL/TLS vulnerability CVE-2017-7407 in the web interface of the device. An attacker can exploit this vulnerability by sending a crafted request to the targeted device. The request can be sent via an email or a website link. The request can also be sent via a message app on the targeted device.
An attacker can exploit a missing patch for the OpenSSL vulnerability CVE-2017-3731 in the web
Vulnerable Packages
Product:
Affected Versions:
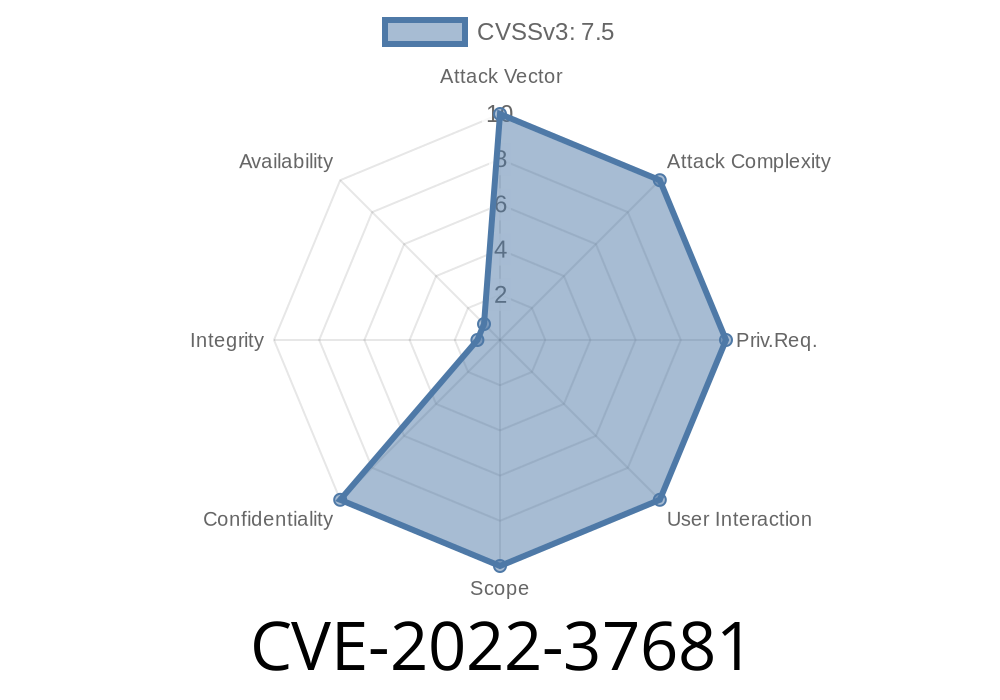
CVE-2022-37681: All devices with firmware versions v4.10 to v4.11.1 (fixed in v4.12)
CVE-2017-7407: All devices with firmware versions v3.0 to v3.2 (fixed in 3.2.28 and 4.0)
CVE-2017-3731: All devices with firmware version v1.0 to v1.6 (fixed in 1.6)
The Device
's Web Interface Vulnerability
The device's web interface is vulnerable to three distinct vulnerabilities. The first vulnerability, a cross-site request forgery (CSRF) vulnerability in the web interface of the device allows attackers to perform an unauthorized login by tricking users into performing certain actions. An attacker can trick a user into performing a CSRF attack by either manipulating the way the link is displayed or by posing as a trustworthy source of information. The second vulnerability, an XSS vulnerability in the web interface of the device allows attackers to inject arbitrary web script or HTML via the device's web interface. An attacker can exploit this XSS vulnerability by sending a crafted request to the targeted device. The third vulnerability, a missing patch for the SSL/TLS vulnerability CVE-2017-7407 in the web interface of the device, allows attackers to exploit this vulnerability by sending a crafted request to the targeted device.
Installation and setup of the device
The device is easy to install, as it only requires a power outlet and internet connection. Once the device is installed, users are required to download and install the associated apps from their phone’s app store.
This vulnerability was discovered by Matthew Prince of Cloudflare, who also reported it to Philips. He has since shared with Philips how to fix the issue at hand.
Timeline
Published on: 08/29/2022 23:15:00 UTC
Last modified on: 09/01/2022 20:58:00 UTC