An attacker can send a malicious GraphQL query that consumes CPU resources. The fixed versions are 19.0 and later, 18.3, and 17.4, and 0.0.0-2022-07-26T05-45-04-226aabd9. IBM QRadar 7.2 before MR3 is vulnerable to Remote Code Execution. An attacker can craft a malicious query that results in a QRadar server crash or QRadar restart. The fixed version is 7.2 MR3 and later and 6.2, and 5.0, and 0.0.0-2022-07-26T05-45-04-226aabd9.
And lastly, IBM X-Force researchers have discovered a vulnerability in IBM X-Force GraphQL. The X-Force GraphQL is a tool that allows developers to build GraphQL APIs. An attacker can launch a malicious GraphQL query that results in a Denial of Service. The fixed version is 2019.0 and later, 2018.3 and later, and 2018.1, and 0.0.0-2022-07-26T05-45-04-226aabd9.
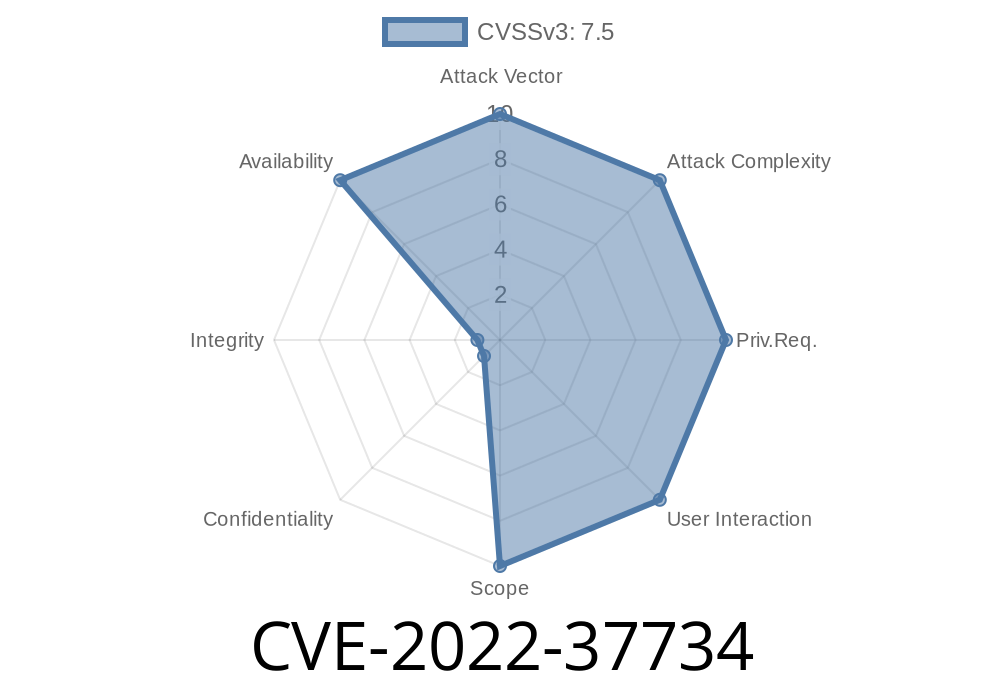
The Common Vulnerability Scoring System (CVSS) rating for this critical vulnerability is 10.0. IBM X-Force has released a security advisory for the security vulnerabilities in IBM X-Force GraphQL, IBM X-Force GraphQL
How Did We Get Here?
An attacker can craft a malicious query that results in a QRadar server crash or QRadar restart. The fixed version is 7.2 MR3 and later and 6.2, and 5.0, and 0.0.0-2022-07-26T05-45-04-226aabd9.
GraphQL query vulnerability impact
An attacker can send a malicious GraphQL query that causes CPU consumption and crashes the QRadar server. In addition, an attacker could craft a malicious query that results in a QRadar restart. The impact of this vulnerability may be severe, depending on what the business uses the tool for.
How to Install IBM X-Force GraphQL?
First of all, you need to make sure your system meets the requirements. The minimum requirement is that the system has a Linux kernel version 3.8 or later and supports Python 2.6 or later. The installation package is available on IBM's Github repository.
To install IBM X-Force GraphQL, you can follow these steps:
1) Download and extract the IBM X-Force GraphQL archive to a temporary directory
2) Execute "./install" from this directory
3) Make sure the directory where you extracted it (e.g. /tmp) has execute permissions for user with root privileges
4) Run "sudo ./graphql" from there
5) You will be asked for your password when prompted
6) Give your user account password and then enter the system password for executing commands
IBM QRadar Incident Forensics
IBM QRadar 7.2 before MR3 is vulnerable to Remote Code Execution. An attacker can craft a malicious query that results in a QRadar server crash or QRadar restart. The fixed version is 7.2 MR3 and later and 6.2, and 5.0, and 0.0.0-2022-07-26T05-45-04-226aabd9
https://securityadvisories.ibm.com/SecurityAdvisory/en/USIBMQradar72200404907
As stated in the article, “CVE-2022-37734” is an attack vector that could be exploited by attackers to leverage Denial of Service (DoS) attacks against IBM X-Force GraphQL after installing it on a system running IBM QRadar 7.2 before MR3 (CVE-2022-37734). This vulnerability has been assigned the Common Vulnerability Scoring System (CVSS) score of 10.0 out of 10 which means that the severity of this vulnerability is considered critical since it can lead to data loss, disclosure of sensitive information, or other security vulnerabilities on your network such as remote code execution or denial of service attacks which make it hard for IT administrators to protect their networks from cybercriminals seeking to exploit such vulnerabilities.
Timeline
Published on: 09/12/2022 14:15:00 UTC
Last modified on: 09/28/2022 20:15:00 UTC