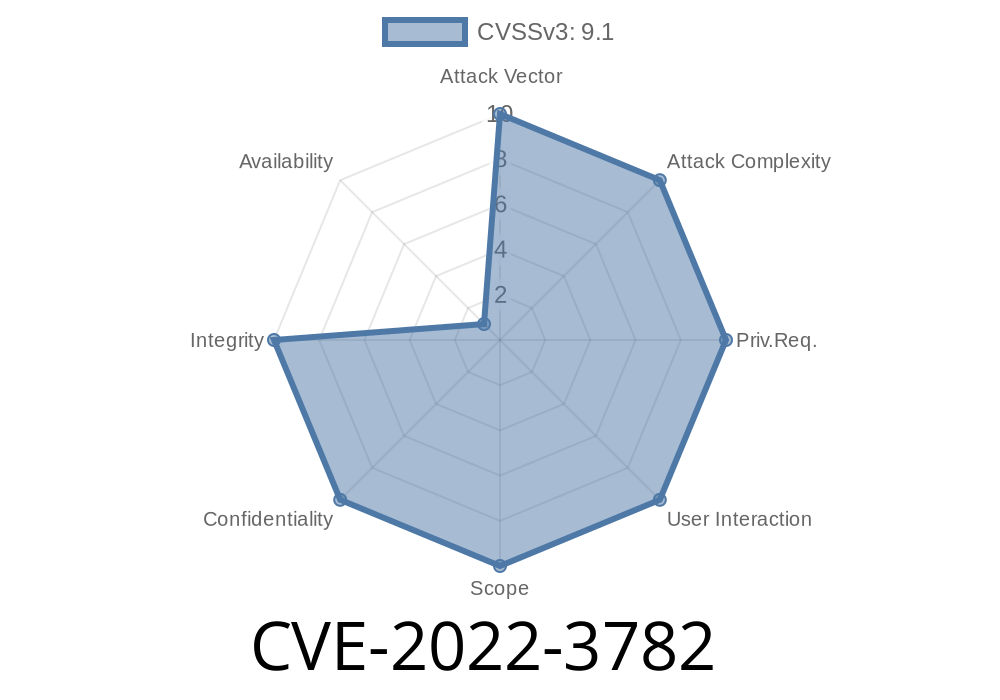
In October 2022, a security vulnerability was uncovered in Keycloak, a widely used open-source identity and access management solution. This flaw—tracked as CVE-2022-3782—let attackers abuse path traversal by double URL encoding, exposing sensitive endpoints through improperly validated redirects. Let’s break down what happened, see how the exploit works, and discuss how to keep your deployments safe.
What is Keycloak?
Before diving in, remember, Keycloak helps manage user authentication and single sign-on for web apps and services. It’s very popular among developers for securing modern apps.
The Short Story
Keycloak lets developers control where users can be sent after they log in or log out. This is configured in the Valid Redirect URIs setting. When you use a wildcard in this field—for example, https://myapp.com/*—Keycloak is supposed to make sure that redirects only go to safe locations under your domain.
However, Keycloak failed to properly validate redirect URLs that use tricky tricks like double URL encoding. This let attackers bypass the controls and redirect users to locations you didn’t intend—potentially revealing sensitive information or opening doors for further attacks.
Discovered by: Dawid Golunski (exploit details)
Keycloak Security Bulletin: KEYCLOAK-20049
Technical Details: Double URL Encoding 101
URL encoding changes characters into a “safe” format for browsers. For example, / turns into %2F.
Double URL encoding means you encode the percent sign, too: %2F becomes %252F (%25 = %), so:
- / → %2F
Then, %2F → %252F
Some systems decode just once, and others twice. That’s where the trick comes in.
Keycloak’s Flawed Check (Simplified in Pseudocode)
// Keycloak's original logic:
if (redirectUri.startsWith(validRedirectPrefix)) {
// Allow redirect
}
But what if someone sneaks in a double-encoded value, like so?
Suppose the allowed redirect URIs setting is https://myapp.com/*.
Legit:
https://myapp.com/welcome
Malicious (double encoded):
https://myapp.com%252F..%252Fadmin-panel
When Keycloak decodes this once, it gets:
https://myapp.com%2F..%2Fadmin-panel
Decode again, and it’s really:
https://myapp.com/../admin-panel (which can traverse up the path!)
This can allow attackers to reach /admin-panel or other unexpected places.
`
https://myapp.com%252F..%252F..%252Fprivate
`
2. Sends it as the redirect_uri parameter in OAuth/OIDC requests:
`
Keycloak decodes only once and verifies:
- It matches the allowed pattern https://myapp.com/*
Browser decodes the URI once more (or app server decodes twice):
- User lands at /private or /admin page—not meant to be accessed this way.
Suppose you have
- Valid Redirect URIs: https://myapp.com/*
- Hidden admin panel at: https://myapp.com/admin/secret
Malicious redirect_uri
https://myapp.com%252Fadmin%252Fsecret
Authorization Request Example
curl "https://keycloak.example.com/auth/realms/myrealm/protocol/openid-connect/auth?client_id=myclient&redirect_uri=https%3A%2F%2Fmyapp.com%252Fadmin%252Fsecret&response_type=code";
Result:
If exploited, the victim may get redirected to the secret admin page.
Potential Impact
- Unauthorized access: Attackers may reach protected pages (think: admin areas, dashboards, user profiles).
Sensitive data exposure: Info that was never meant to be public could leak.
- CSRF/Phishing vector: Crafted links could fool users or steal data.
Are You Affected?
If you configured any client in Keycloak with wildcard (*) in “Valid Redirect URIs,” you’re at risk!
This includes common patterns like
Mitigation and Fix
- Keycloak patched this vulnerability. (See Security Advisory)
Extra: Quick Code Check
If you're not sure about your Keycloak configuration, run this simple code/grep command in your export:
grep -r '"redirectUris".*\*' /path/to/keycloak-export.json
References & Further Reading
- CVE-2022-3782 on NVD
- Keycloak Security Advisory – GHSA-m4rq-5w32-hv23
- Exploit-DB PoC 50946
- Keycloak blog: Upgrade notes
Conclusion
CVE-2022-3782 is a great reminder that even sophisticated, security-focused projects like Keycloak can have hidden edge case vulnerabilities. If you use Keycloak with wildcard redirect URIs, update and audit your configs immediately to prevent attackers from abusing your system with sneaky double-encoding tricks.
Stay safe! If you have questions, check out Keycloak’s community docs or reach out for help.
Have you checked your redirect URIs lately?
Let us know what practices you follow to keep your login flows tight and secure!
Timeline
Published on: 01/13/2023 06:15:00 UTC
Last modified on: 01/25/2023 20:38:00 UTC