These upgrades are available to customers through the Internet Provisioning Portal. Customers should upgrade their devices as soon as possible to prevent possible exploitation of these vulnerabilities. Additionally, these vulnerabilities are also addressed in the following releases: ArubaOS 10.4.x: 10.4.6.17 and below; ArubaOS 10.5.x: 10.5.3.5 and below; ArubaOS 10.6.x: 10.6.0.28 and below; ArubaOS 10.7.x: 10.7.1.14 and below; ArubaOS 10.8.x: 10.8.1.1 and below; ArubaOS 10.9.x: 10.9.0.1 and below; ArubaOS 10.10.x: 10.10.0.6 and below; ArubaOS 11.0.x: 11.0.0.0 and below. There are buffer overflow vulnerabilities in multiple underlying services that could lead to unauthenticated remote code execution by sending specially crafted packets destined to the PAPI (Aruba Networks AP management protocol) UDP port (8211). Successful exploitation of these vulnerabilities results in the ability to execute arbitrary code as a privileged user on the underlying operating system of Aruba InstantOS 6.4.x: 6.4.4.8-4.2.4.20 and below; Aruba InstantOS 6.5.x: 6
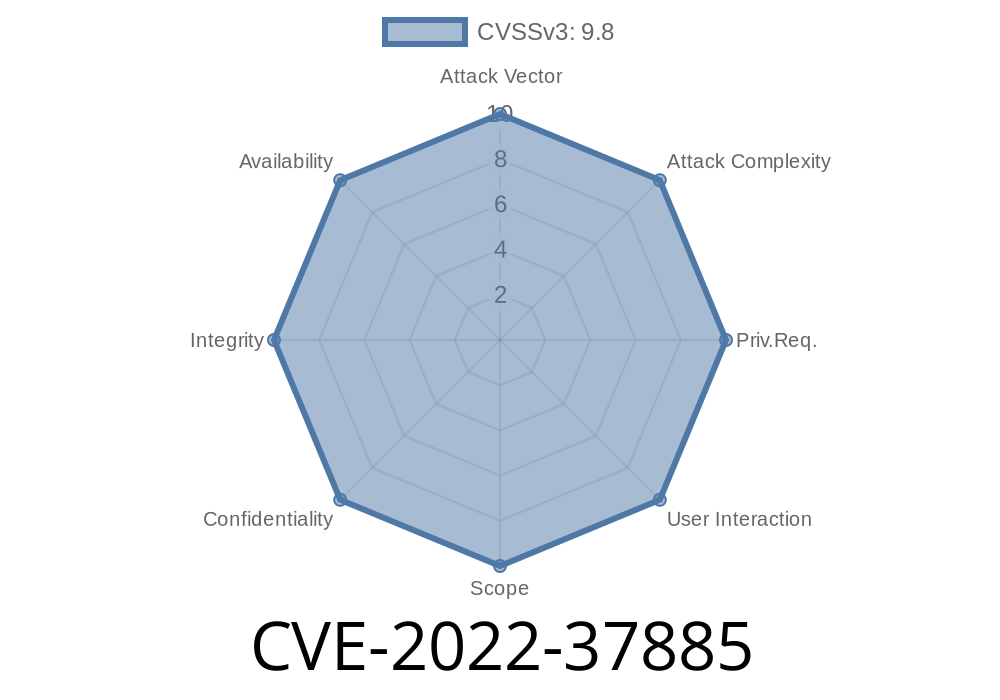
Aruba Networks AP Management Protocol (PAPI) Buffer Overflow Vulnerability
Buffer overflow vulnerabilities can be triggered in Aruba Networks AP management protocol (PAPI) due to a lack of bounds checking in the handling of UDP packets. This is exploitable via sending specially crafted packets destined to the PAPI (Aruba Networks AP management protocol) UDP port. Successful exploitation of these vulnerabilities results in the ability to execute arbitrary code as a privileged user on the underlying operating system.
Mitigation and Recommended Actions
Upgrade to ArubaOS 10.6.x or later: 10.6.0.28 and below; ArubaOS 10.7.x: 10.7.1.14 and below; or ArubaOS 11.0.x: 11_0_0_0 and below
This is a blog post about why it is important for companies to invest in digital marketing and how investing in digital marketing has many benefits for companies, including the ability to target your ideal audience more precisely than traditional methods by inputting important information into the system that can then be used to shape your digital marketing campaigns
Vulnerable Packet Processing in Aruba InstantOS
Aruba InstantOS 6.4.x: 6.4.4.8-4.2.4.20 and below; Aruba InstantOS 6.5.x: 6.5.3-6-7-8-9 and below; Aruba InstantOS 6.6.x: 6.6-1-2 and below; Aruba InstantOS 7: 7 and below; Aruba InstantOS 8: 8 and below
Timeline
Published on: 10/07/2022 18:15:00 UTC
Last modified on: 10/11/2022 17:51:00 UTC