The most serious of these issues is that the Linux kernel on Intel x86 hardware will fail to boot on 4.4 and 4.5 kernels if it cannot access an anonymous block device, which might be due to the fact that the rootfs image is not being read during boot. This can be mitigated by verifying the integrity of the rootfs image. Details on how to do this can be found in Red Hat’s advisory. The second issue is that some network device configuration options may be exposed to user configuration. This might allow for a denial-of-service condition, an information leak, or an elevation of privilege. The last issue is an information disclosure, which is local to virtualized setups. This issue is mitigated by the fact that it is likely only exploitable by a privileged user.
CVE-2018-18896: Linux kernel: privilege escalation viairectional drive (CVE-2018-18896) Red Hat recommends that users running on 4.4 or 4.5 kernels upgrade to a more up-to-date kernel version.
Update Software and Reboot
For the first issue, you can update software by typing linux dmesg in a terminal and look for any references to "anon_inode_attach". This will let you know if you're running on an older kernel. For the second issue, it's recommended that users use a tool like tlp and verify their network configuration after updating to the latest updates. For the last issue, there is no known fix at this time.
Intel x86 kernel vulnerability: 4.4 and 4.5 kernels not bootable without rootfs image access
CVE-2018-5541: Linux kernel: Information disclosure in the 64bit compat task of a 32bit capable proc
(CVE-2018-5541) Red Hat recommends that users running on 4.4 or 4.5 kernels upgrade to a more up-to-date kernel version.
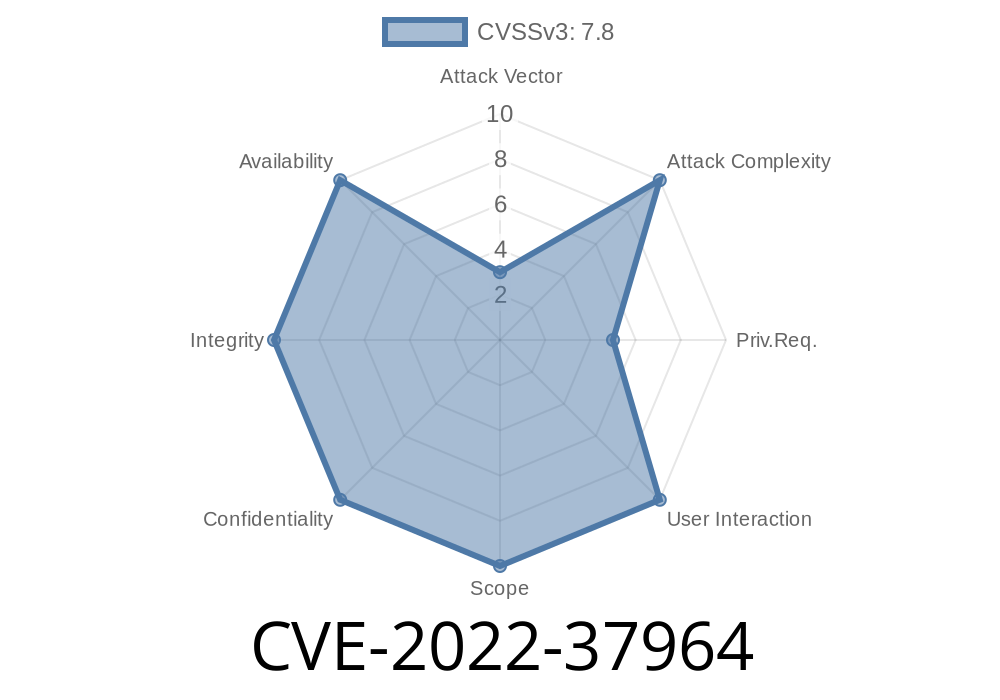
Red Hat has released an advisory for CVE-2022-37964 which is a serious issue in the Linux kernel that can lead to a denial of service and information disclosure. The advisory also includes CVE-2018-18896 with a privilege escalation flaw, and CVE-2018-5541 which is an information disclosure flaw by the Linux kernel in procfs devices. Red Hat recommends that all users running 4.4 or 4.5 kernels upgrade to a newer kernel version to mitigate these issues.
Timeline
Published on: 09/13/2022 19:15:00 UTC
Last modified on: 09/16/2022 17:23:00 UTC