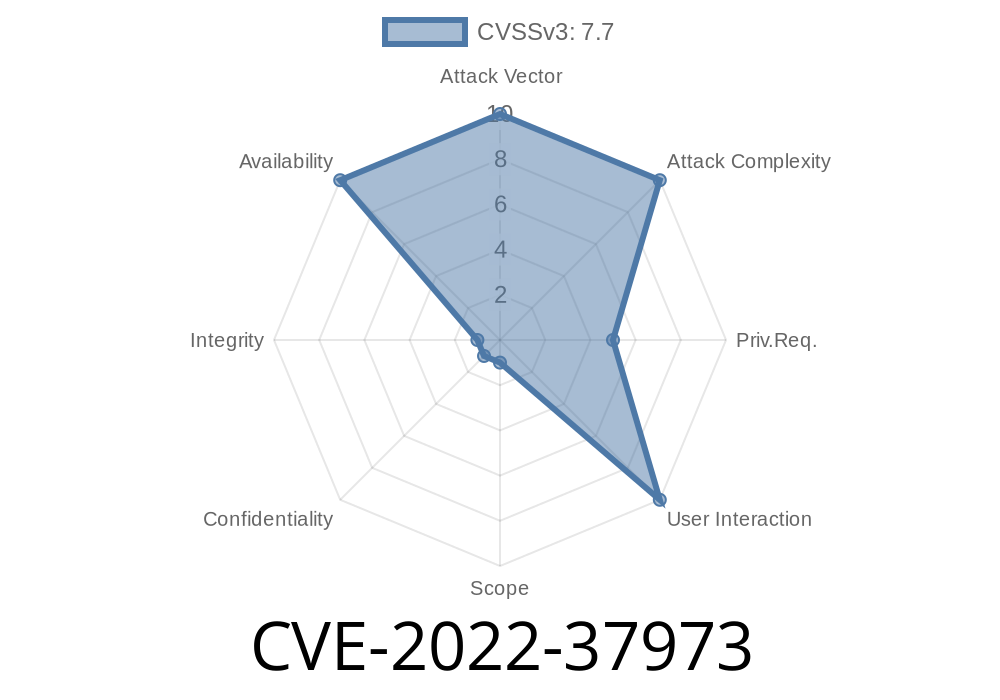
This is a session management denial of service vulnerability, which is when a web server session is accidentally terminated by a user. This can be caused by a lack of session management checks, a malicious script, a poorly configured web server, or any other reason. An attacker can exploit this session management vulnerability to perform a denial of service attack on the targeted server. A successful exploit will cause service disruptions to the targeted server. A successful exploit could also result in sensitive data being compromised. There are several steps that can be taken to prevent session management denial of service attacks. These include: Improving session management in web applications
Maintaining web server security and server hardening
Improving Session Management in Web Applications
Session management is a crucial part of web applications. Many websites have poor session management, which causes service disruptions and data leaks. Attackers can exploit this by performing a denial of service attack.
There are many steps that can be taken to prevent these attacks. These include:
Improving session management in web applications
Maintaining web server security and server hardening
Timeline
Published on: 10/11/2022 19:15:00 UTC
Last modified on: 10/11/2022 19:16:00 UTC