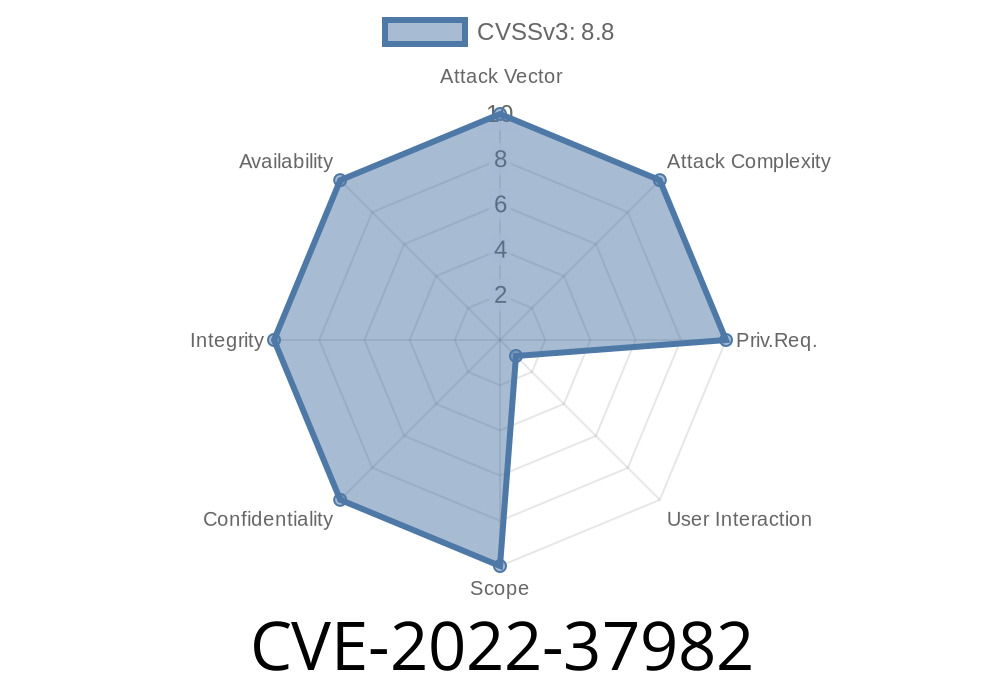
This issue is related to the lack of validation of user-supplied input in the Microsoft Software Data Access Components (WDAC) OLE DB provider for SQL Server. An attacker can exploit this vulnerability by passing a user-supplied SQL query to the vulnerable service, resulting in a remote code execution. The update addresses these vulnerabilities by adding additional validation of user-supplied input. A remote attacker can exploit this vulnerability by passing a user-supplied SQL query to the vulnerable service, resulting in a remote code execution. A remote attacker can exploit this vulnerability by injecting malicious code into a web page that users view, resulting in a remote code execution. Microsoft received information regarding these vulnerabilities through responsible disclosure. A number of resources are available to help you determine whether your software is vulnerable and what to do about it.
Microsoft Software Data Access Components (WDAC) SQL Server Provider
Microsoft Software Data Access Components (WDAC) SQL Server Provider is a service that manages a Microsoft SQL Server database so that Windows-based applications can access it. This service can be configured to allow only trusted users to connect and access the data via SQL statements submitted by an application. These services do not have any end-user interface, but are designed specifically for software developers who need to write code that interacts with a database.
Risk Assessment
A remote attacker can exploit this vulnerability by passing a user-supplied SQL query to the vulnerable service, resulting in the execution of arbitrary code on the target system.
SQL Server and Microsoft Database Engine Services Are Vulnerable
SQL Server and the Microsoft Database Engine Services are vulnerable to a remote code execution vulnerability. This is due to the lack of validation of user-supplied input in the Microsoft Software Data Access Components (WDAC) OLE DB provider for SQL Server. A remote attacker can exploit this vulnerability by passing a user-supplied SQL query to the vulnerable service, resulting in a remote code execution. The update addresses these vulnerabilities by adding additional validation of user-supplied input. A remote attacker can exploit this vulnerability by passing a user-supplied SQL query to the vulnerable service, resulting in a remote code execution. A remote attacker can exploit this vulnerability by injecting malicious code into a web page that users view, resulting in a remote code execution. Security updates have been made available for supported versions of Windows, SQL Server, and Windows Azure Web Sites.
Introduction
A remote code execution vulnerability has been discovered in Microsoft Software Data Access Components (WDAC) OLE DB provider for SQL Server. The update addresses these vulnerabilities by adding additional validation of user-supplied input.
The vulnerability that is being addressed is related to the lack of validation of user-supplied input in the Microsoft Software Data Access Components (WDAC) OLE DB provider for SQL Server. An attacker can exploit this vulnerability by passing a user-supplied SQL query to the vulnerable service, resulting in a remote code execution.
What is SQL Server MSDACC CVE?
The Microsoft Software Data Access Components (WDAC) OLE DB provider for SQL Server is vulnerable to a remote code execution vulnerability. This CVE identifier refers to the update that addresses this vulnerability in SQL Server. A remote attacker can exploit this vulnerability by passing a user-supplied SQL query to the vulnerable service, resulting in a remote code execution. A remote attacker can exploit this vulnerability by injecting malicious code into a web page that users view, resulting in a remote code execution.
Microsoft received information regarding these vulnerabilities through responsible disclosure. A number of resources are available to help you determine whether your software is vulnerable and what to do about it.
SQL Server Software Data Access Components (WDAC) OLE DB Provider
The Microsoft Software Data Access Components (WDAC) OLE DB provider for SQL Server is a component of the SQL Server 2012 Express LocalDB and SQL Server 2014 Express LocalDB installation packages. The provider exposes a service that is vulnerable to remote code execution.
The update addresses these vulnerabilities by adding additional validation of user-supplied input. A remote attacker can exploit this vulnerability by passing a user-supplied SQL query to the vulnerable service, resulting in a remote code execution. A remote attacker can exploit this vulnerability by injecting malicious code into a web page that users view, resulting in a remote code execution. Microsoft received information regarding these vulnerabilities through responsible disclosure. A number of resources are available to help you determine whether your software is vulnerable and what to do about it.
Timeline
Published on: 10/11/2022 19:15:00 UTC
Last modified on: 10/11/2022 19:16:00 UTC