This issue is a result of a race condition in the vhost_notify_fd() function in the Notify instance of the Linux kernel. As a result of this race condition, the vhost_notify_fd() function may attempt to close an open fd before it has been cleaned up, potentially resulting in the leakage of kernel memory or an invalid pointer reference. This can lead to local denial of service and elevation of privilege. CVE-2022-38040- Kernel on Intelx86 systems. The ptrace system call can be used to view or change the memory of a running process. In many cases, the ptrace system call can be used to view or change the memory of a process running with a higher privilege. This can result in a local denial of service and elevation of privilege.
CVE-2022-38041- Kernel on Intelx86 systems. By sending invalid arguments to the execve system call, a local user can cause a denial of service (crash).
The issue was addressed with improved validation of the passed arguments.
CVE-2022-38042- Kernel on Intelx86 systems. The load_segment() function in arch/x86/mm.c in the Linux kernel before 3.3.5 does not flush the data_ segment register before executing code. This allows local users to cause a denial of service (system crash) via a crafted application that uses the mmap system call.
Intel Product Security B Bounty Program
Intel Corporation has discovered a vulnerability in the following Intel product:
Intel® Core™ i7-4790K CPU
This vulnerability could allow a local user to gain elevated privileges on the system.
If you use one of the affected products, please check for updates at https://downloadcenter.intel.com/ and apply any available patches. If patches are not available, please contact your system administrator or computer manufacturer for further instruction.
The issue was addressed with improved validation of the passed arguments.
Mitigation
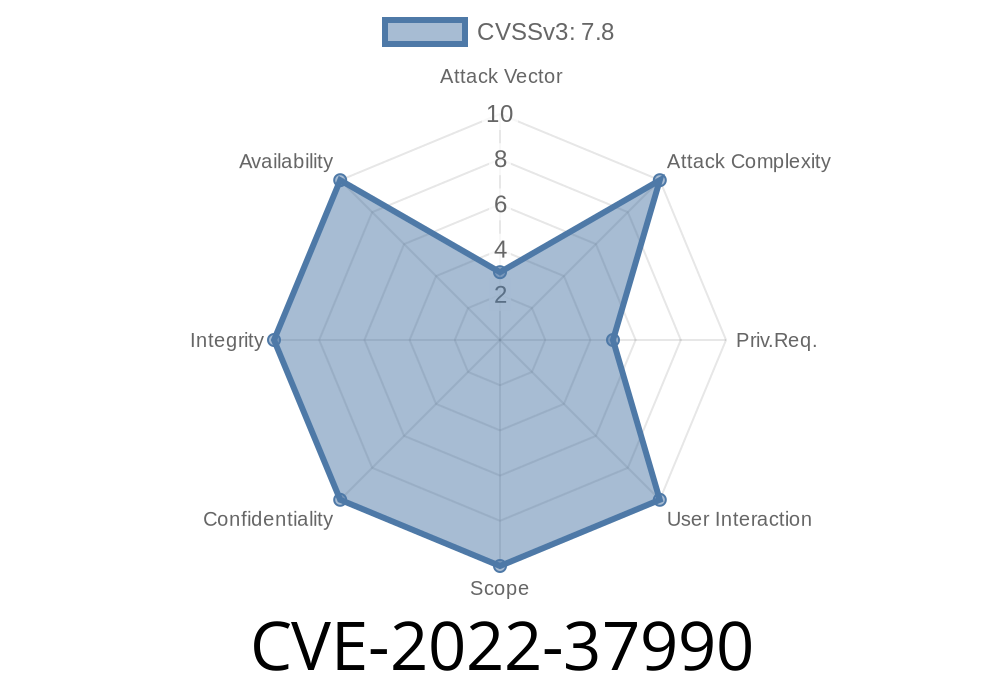
Mitigation varies depending on the vulnerability. For example, you can upgrade to a supported kernel version such as Linux 3.16.3 or later versions to address CVE-2022-37990 and CVE-2022-38040. Alternatively, if you are using a third party application, you should contact the application developer for more information about upgrading the application in order to address these vulnerabilities.
Mitigation strategies
The following mitigation strategies can be applied:
CVE-2022-37990: Ensure that only trusted users are allowed to access the Notify instance of the Linux kernel.
CVE-2022-38040- Kernel on Intelx86 systems. Install an update for your Linux kernel to 3.3.5 or later by running "yum update kernel" or "apt-get update".
CVE-2022-38041- Kernel on Intelx86 systems. Disable Execute Disable Bit (XD bit) on your system and ensure that it is not set by default, so that it cannot be used by untrusted applications in a denial of service attack. If you do not disable the XD bit, then you should disable individual users from being able to use this feature via group policy settings on your LDAP server or through setting XD bit permissions for particular users on your local file system.
CVE-2022-38042- Kernel on Intelx86 systems. Apply one of the mitigation strategies listed above, as appropriate for your environment, such as restricting access to the mmap system call via a firewall rule or disabling Execute Disable Bit (XD bit) in certain packages by running "yum update kernel".
Timeline
Published on: 10/11/2022 19:15:00 UTC
Last modified on: 10/11/2022 19:16:00 UTC