This CVE ID was first published on 12/03/2016. A critical remote code execution vulnerability exists in Group Policy Preferences (GPP) when it’s configured to run on Windows Server 2008 R2, Windows Server 2012, Windows Server 2012 R2, Windows Vista, Windows 7, Windows 8.1, Windows 10. An attacker could exploit this vulnerability by persuading a user to open a specially crafted website or launch a specially crafted application. An attacker could also exploit this vulnerability by tricking a user into approving a user rights assignment where a specially crafted application was running on the target computer. Microsoft received information about this vulnerability through responsible disclosure. There are workarounds available to reduce the risk of exploitation. In a mixed Windows environment, you can disable GPP.
Microsoft Windows Overview
Microsoft Windows is a family of operating systems developed and marketed by Microsoft. It consists of several distinct operating system subfamilies, each of which serves a different market segment. The best known and most popular member of the family is the Windows NT family, including Windows XP, Windows Server 2003, Vista, 7 and 8. As of January 2019, Windows 10 usage share was at 32%, with a total share of 62%
How can I determine if I am affected?
Microsoft recommends checking for the presence of GroupPolicy.exe in the %windir%\system32 folder. If it’s present, you may be affected by the vulnerability. You can also manually check your computer by running gpupdate /force from an elevated command prompt, which will update Group Policy settings on your computer and display a warning if the update fails.
Affected Software
This CVE ID was first published on 12/03/2016. Group Policy Preferences (GPP) is affected by a critical remote code execution vulnerability when it's configured to run on Windows Server 2008 R2, Windows Server 2012, Windows Server 2012 R2, Windows Vista, Windows 7, Windows 8.1, or Windows 10. The vulnerability could allow remote code execution if an attacker persuades a user to open a specially crafted website or launch a specially crafted application. An attacker could also exploit this vulnerability by tricking a user into approving a user rights assignment where a specially crafted application was running on the target computer.
Disabling Group Policy Preferences
Microsoft has confirmed that Group Policy Preferences is vulnerable to a critical remote code execution vulnerability. This vulnerability allows an attacker to take control of the computer by executing arbitrary code on the target. Microsoft released a fix for this flaw in Windows 10, Windows 8.1, Windows 7, and Windows Server 2008 R2 operating systems. If you don’t have these specific updates installed on your system, you can disable Group Policy Preferences from your computer.
Use Group Policy Management Console:
- Open Group Policy Management Console
- Navigate to Computer Configuration/Administrative Templates/System/GPExtensions
- Right-click Group Policy Preferences and select Disable
In order to re-enable GPP settings after disabling them, run the following command:
gpupdate /force /target:computer
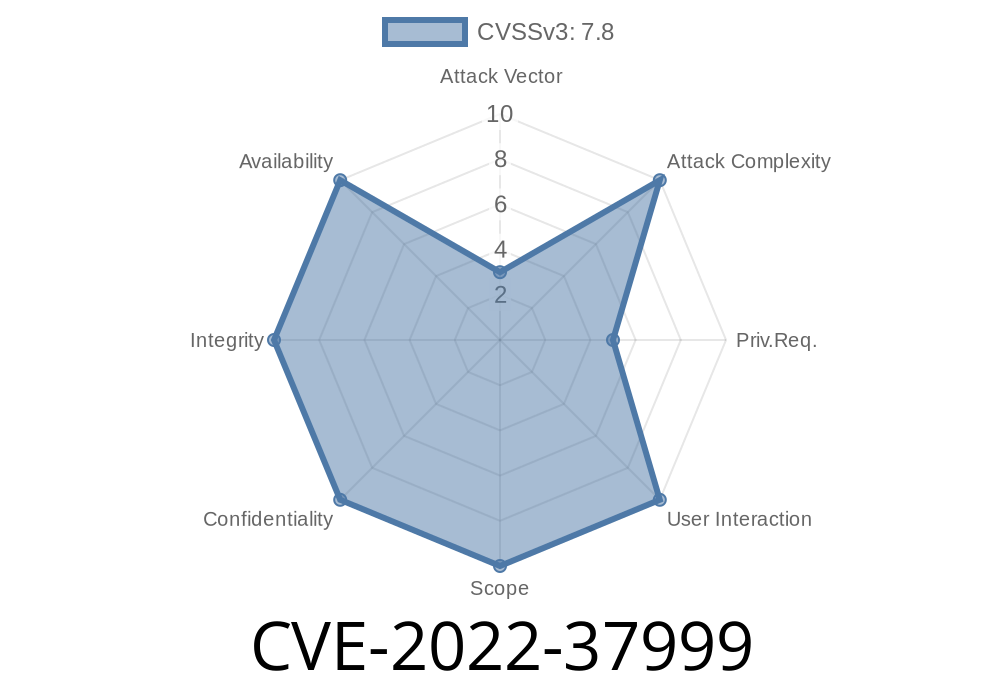
ID: CVE-2022 -37999
A critical remote code execution vulnerability exists in Group Policy Preferences (GPP) when it’s configured to run on Windows Server 2008 R2, Windows Server 2012, Windows Server 2012 R2, Windows Vista, Windows 7, Windows 8.1, Windows 10. An attacker could exploit this vulnerability by persuading a user to open a specially crafted website or launch a specially crafted application. An attacker could also exploit this vulnerability by tricking a user into approving a user rights assignment where a specially crafted application was running on the target computer. Microsoft received information about this vulnerability through responsible disclosure. There are workarounds available to reduce the risk of exploitation. In a mixed Windows environment, you can disable GPP.
The only way for users to protect themselves from exploitation is to disable Group Policy Preferences.
Timeline
Published on: 10/11/2022 19:15:00 UTC
Last modified on: 10/13/2022 13:19:00 UTC