This is a Windows feature that enables an organization to protect user data and prevent it from being altered or deleted when a device is compromised. It’s enabled by default on Windows 8, Windows 10, and Windows Server 2016. It can be configured on earlier versions of Windows as well. This feature prevents data from being altered or lost by encrypting it using a Key Management Service (KMS) server. When an attacker attempts to modify or delete the data with a malicious program, the data won’t be altered or deleted instead, it will be encrypted and stored in the KMS server. To access the data, an attacker would have to have access to the KMS server.
Key Management Service (KMS)
The Key Management Service (KMS) is a Windows feature that enables an organization to protect user data and prevent it from being altered or deleted when a device is compromised. It's enabled by default on Windows 8, Windows 10, and Windows Server 2016. It can be configured on earlier versions of Windows as well. This feature prevents data from being altered or lost by encrypting it using a KMS server. When an attacker attempts to modify or delete the data with a malicious program, the data won't be altered or deleted instead, it will be encrypted and stored in the KMS server. To access the data, an attacker would have to have access to the KMS server.
Disable volume shadow copy service
Windows 8 and 10 contain a service called the volume shadow copy service. This is an important feature for administrators to configure for their devices, but it’s also a great target for attackers who may attempt to take over data on the device. For example, if you use Microsoft OneDrive as your default file storage solution and have user accounts configured with admin-level privileges on Windows 8 or 10, the attacker could download files from OneDrive and replace those files with malicious code. By disabling the volume shadow copy service, you will prevent this from happening.
Windows Defender SmartScreen Filter
Windows Defender SmartScreen Filter is a Windows feature that protects computers and networks from malicious software. It’s enabled by default on Windows 8, Windows 10, and Windows Server 2016. It can be configured on earlier versions of Windows as well. This feature warns users when they download or run certain apps or files, so users can decide whether the file is safe to run before continuing with the installation. If a user doesn’t install the file, it will not be able to execute on your system. The SmartScreen filter also blocks potentially harmful downloads from occurring automatically without warning you about them first. When a download is blocked, an alert will be displayed asking if you want to proceed with the download anyway.
Disable Disk Encryption on Windows Server 2012 R2
This is a Windows feature that enables an organization to protect user data and prevent it from being altered or deleted when a device is compromised. It’s enabled by default on Windows 8, Windows 10, and Windows Server 2016. It can be configured on earlier versions of Windows as well. This feature prevents data from being altered or lost by encrypting it using a Key Management Service (KMS) server. When an attacker attempts to modify or delete the data with a malicious program, the data won’t be altered or deleted instead, it will be encrypted and stored in the KMS server. To access the data, an attacker would have to have access to the KMS server.
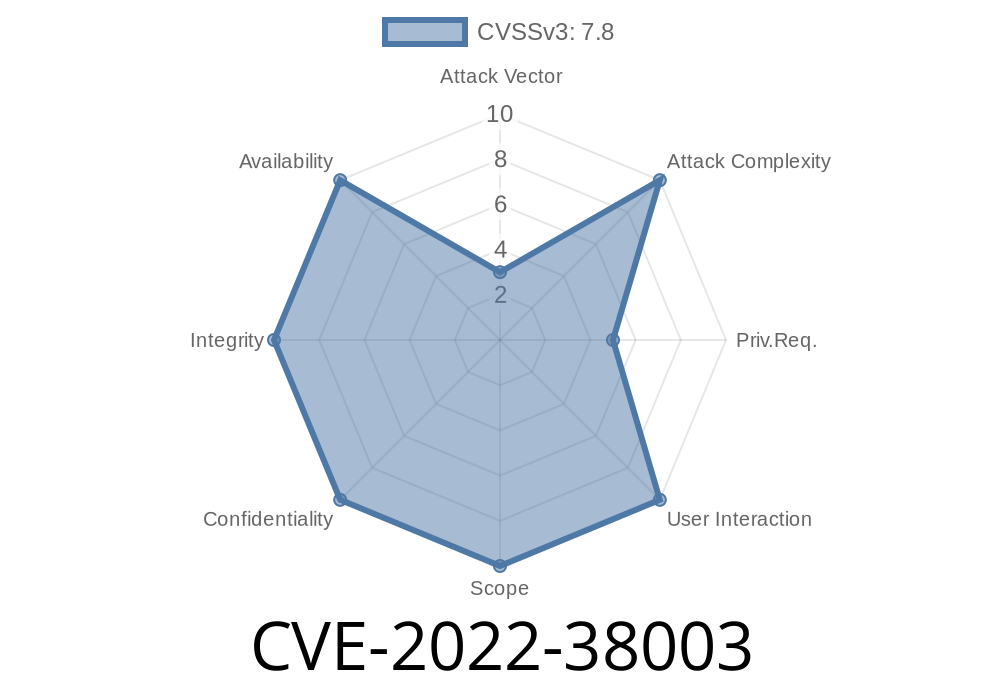
Enable or Disable CVE-2022 -38003
To disable CVE-2022-38003, follow these steps:
1. Add the following command to run on an Administrator account in PowerShell: $credential = Get-Credential
2. Credentials will be automatically populated with the credentials of the current user when this command is completed.
3. To disable CVE-2022-38003, use the following command: Disable-WindowsOptionalFeature -Online -FeatureName Microsoft-Server-ActiveDirectoryProtection -Remove
4. After disabling it, run this command to remove any previously enabled features that were removed by this feature: Remove-WindowsFeature -Online -FeatureName *Microsoft*Server*ActiveDirectory*Protection*
5. Restart your computer for changes to take effect
Timeline
Published on: 10/11/2022 19:15:00 UTC
Last modified on: 10/12/2022 17:29:00 UTC