While parsing OLE DB data in the process of execution of the malicious code in the SQL Server, the vulnerable version of the provider did not check the length of submitted data. As a result, the attacker could specify an arbitrary code in the database server. The attack vector of this vulnerability is Microsoft Office documents. Fortunately, the majority of the Microsoft Office products do not allow to upload arbitrary code to the database server. In order to exploit this vulnerability, an attacker needs to send a malicious document to a user who has access to the target database server. Unless the user has direct access to the database and does not have restrictions on the use of the database server, this attack will be unsuccessful. Vulnerable versions of the OLE DB provider for SQL Server: 12.0, 11.0, 10.0, 9.0, 8.2, and 8.1. Reported by: TippingPoint’s Security Research and Analysis Team. https://www.tippingpoint.com/advisories/TippingPoint-Security-Research-Analysis-Team-CVE-CVE-2022-37982-wdac-ole-db-remote-code-execution.html TippingPoint’s indicators of compromise are available at the following link: https://github.com/TippingPoint/CVE-CVE-2022-37982
Vulnerability in the way SQL Server handles quotes and special characters
A vulnerability exists when the reported version of the OLE DB provider for SQL Server does not properly handle quotes and special characters in data that is sent to it.
This vulnerability could allow an attacker to execute arbitrary code on the database server. This attack vector would depend on whether the user has direct access to the database server and does not have restrictions on the use of the database server.
Vulnerable versions of the OLE DB provider for SQL Server: 12.0, 11.0, 10.0, 9.0, 8.2, and 8.1
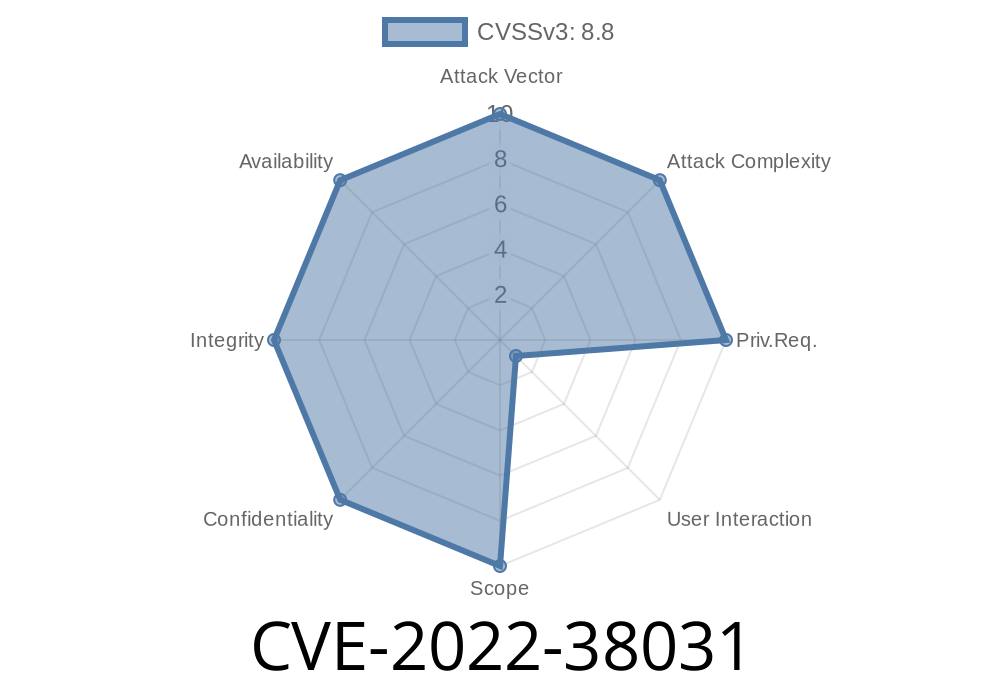
Microsoft Word Document Remote Code Execution Vulnerability
While parsing OLE DB data in the process of execution of the malicious code in the SQL Server, the vulnerable version of the provider did not check the length of submitted data. As a result, an attacker could specify an arbitrary code in the database server. The attack vector of this vulnerability is Microsoft Word documents. Fortunately, most Microsoft Office products do not allow to upload arbitrary code to the database server. In order to exploit this vulnerability, an attacker needs to send a malicious document to a user who has access to the target database server. Unless the user has direct access to the database and does not have restrictions on the use of the database server, this attack will be unsuccessful. Vulnerable versions of OLE DB provider for SQL Server: 12.0, 11.0, 10.0, 9.0, 8.2, and 8.1 Reported by: TippingPoint’s Security Research and Analysis Team https://www.tippingpoint.com/advisories/TippingPoint-Security-Research-Analysis-Team-CVE-CVE-2022-38031
B850B12 server firmware update reboot vulnerability
The vulnerability is caused by the OLE DB provider for SQL Server and could allow a remote, unauthenticated attacker to reboot the server. Vulnerable versions of the OLE DB provider for SQL Server: 11.0, 10.0, 9.0, 8.2 and 8.1. Reported by: TippingPoint’s Security Research and Analysis Team. https://www.tippingpoint.com/advisories/TippingPoint-Security-Research-Analysis-Team-CVE-CVE-2022-37982-wdac-ole-db-remote-code-execution.html TippingPoint’s indicators of compromise are available at the following link: https://github.com/TippingPoint/CVE-CVE-2022-37982
Vulnerability Discovery Discussion
CVE-2022-37982 is a remote code execution vulnerability in Microsoft OLE DB provider for SQL Server. CVE-2022-38031 describes the same vulnerability but with a different date range. This vulnerability occurs when parsing OLE DB data in SQL Server during the process of execution of malicious code by the vulnerable version of OLE DB provider. The attack vector for this vulnerability is Microsoft Office documents that are sent to the target database server, which has an accessible Windows user interface and does not have restrictions on the use of the database server. The majority of Microsoft Office products do not allow arbitrary code to be uploaded to the database server, making exploitation unsuccessful unless a user has direct access to the database and does not have restrictions on the use of the database server.
Timeline
Published on: 10/11/2022 19:15:00 UTC
Last modified on: 10/12/2022 17:11:00 UTC