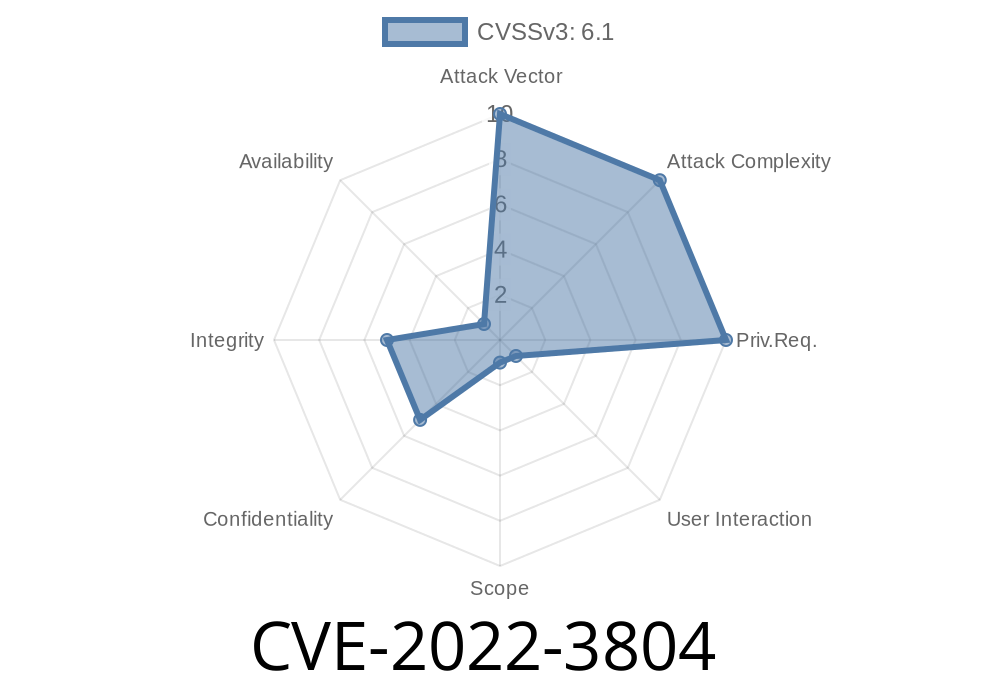
Eolinker Apinto-Dashboard is a popular open-source API management tool. In 2022, a security issue was discovered that could let attackers run malicious scripts in the browsers of users who visited the login page. This issue is tracked as CVE-2022-3804 and has also been listed as VDB-212640. Below you’ll find a simple explanation of the bug, exploitation details, references, code samples, and suggestions on staying safe.
What Is The Problem?
The problem lies in how the Apinto-Dashboard’s /login page handles the callback URL parameter. If you send a specially crafted value for callback, it gets reflected in the web page without any checks or filtering. This is a classic reflected Cross Site Scripting (XSS) vulnerability.
XSS bugs are dangerous because they let attackers run JavaScript in other people’s browsers. That script can steal cookies, impersonate users, or perform actions on their behalf.
Component: eolinker Apinto-Dashboard
- Affected Endpoint: /login
CVE: CVE-2022-3804
- Database Reference: VDB-212640 (View entry)
Attackers send a link like this
http://your-apinto-dashboard-host/login?callback=<script>alert('xss')</script>;
When a user clicks this link, the part in callback is injected into the page and interpreted as code. A harmless example above just pops up an alert. A real attacker would probably steal your authentication cookies or take over your account.
Here’s an example of problematic code in a backend language (JavaScript for demonstration)
// BAD PRACTICE: Reflecting untrusted input directly
app.get('/login', (req, res) => {
const callback = req.query.callback || '';
res.send(`
<html>
<body>
<!-- Vulnerable inject point -->
<form action="${callback}">
<input type="text" name="username">
<input type="password" name="password">
</form>
</body>
</html>
`);
});
If callback contains a <script> tag, your browser will run whatever’s inside.
`
http://target-site/login?callback=alert('XSS')
User is tricked into visiting the URL.
3. Browser executes the script in the context of your dashboard — attacker can now access your data or credentials.
Open Developer Tools and paste the following URL (replace target-site)
http://target-site/login?callback=<script>alert(document.cookie)</script>
If you see an alert with your cookie, the site is vulnerable.
References
- Vuldb VDB-212640
- NVD CVE-2022-3804 summary
- Original disclosure (Exploit Database)
- Eolinker Apinto-Dashboard GitHub repository
How To Fix
- Input Validation: Always sanitize or escape user-provided values before inserting them into web pages.
Validation Example: In Node.js, you could use libraries like validator or DOMPurify.
const validator = require('validator');
app.get('/login', (req, res) => {
let callback = req.query.callback || '';
// Allow only safe URLs
if (!validator.isURL(callback, { require_protocol: true })) {
callback = '/';
}
res.send(/* ... */);
});
Conclusion
CVE-2022-3804 highlights how dangerous it is to mishandle user input on web pages. Even a simple login page can be the source of a major breach. If you use Eolinker Apinto-Dashboard, update your software and do a quick check of your /login page for this problem. Review user inputs everywhere on your applications to avoid this and similar issues in the future.
Timeline
Published on: 11/01/2022 16:15:00 UTC
Last modified on: 11/02/2022 15:10:00 UTC