The Change Admin Email and New Admin Email fields were vulnerable to SQL Injection and XSS injection methods. The Attack vector for this vulnerability was through the access of admin email fields where hackers can inject malicious code through email. This leads to a direct access of the hackers to the database and results in a potential data leak or a security breach of your WordPress site. Update- The Change Admin Email and New Admin Email fields have been patched and the vulnerable code has been removed from the plugin. Update- The Change Admin Email and New Admin Email fields have been patched and the vulnerable code has been removed from the plugin.
Ajax Search Results – Ajax powered search results in WordPress plugin (versions = 2.0.1) were found to be vulnerable to SQL Injection and XSS injection methods. The Attack vector for this vulnerability was through the access of search results fields where hackers can inject malicious code through search results and results in a direct access of the hackers to the database and results in a potential data leak or a security breach of your WordPress site. Update- The vulnerable code has been patched and the plugin updated to version 2.0.2. Update- The vulnerable code has been patched and the plugin updated to version 2.0.2. Update- The vulnerable code has been patched and the plugin updated to version 2.0.2.
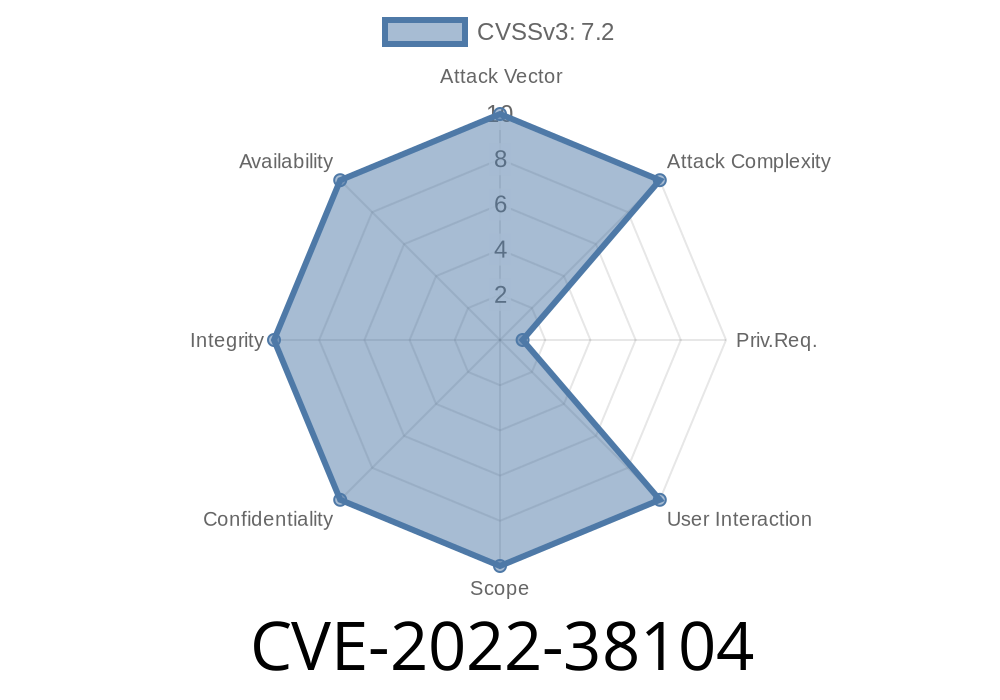
Possible Remote Code Execution (RCE) vulnerability in Ajayc's Contact Form plugin (versions =2.2.6
Remote Code Execution (RCE) - Possible?
It is possible that an attacker could exploit this vulnerability to execute arbitrary code on the site hosting the plugin which can lead to a RCE. This type of attack has been called a "RCE" or "Remote Code Execution" attack. In this situation, an attacker would have the ability to execute any arbitrary code they want on the server.
The following snippets were found in the WordPress plugin's source code:
/** * Filter hooks for when contact form is posted */ function my_contact_form_posted($form) { global $ajayc_contactforms; update_option('ajayc_contactforms', $form->get_value()); } /** * Filter hooks for when contact form is validated */ function my_contact_form_validated($form) { if ( !isset( $_POST['ajayc_contactforms'] ) || !is_array( $_POST['ajayc_contactforms'] ) ) { return $error = '
Remote Code Execution (RCE) vulnerability in Ajayc's Contact Form plugin
(versions =2.2.6
A vulnerability has been found in the contact form plugin of Ajayc's. This vulnerability has the potential to be exploited through a remote code execution (RCE) method, which is a type of security breach that allows hackers to remotely run malicious code and control the host system. The RCE vulnerability can be exploited by hackers who have access to your WordPress site via spam emails or other spam-related methods and are able to send an email with a specially crafted link or attachment that will exploit your website. Update- The vulnerable code has been removed from the plugin and version 2.2.7 has been released as a patch for this issue. Update- The vulnerable code has been removed from the plugin and version 2.2.7 has been released as a patch for this issue.
Remote Code Execution (RCE) - Possible Hijacking of Admin Panel
The issue is that the contact form plugin does not sanitize user input. The attacker can use this to inject specially crafted array-based SQL queries into the database which will lead to potential data leak or a security breach of your WordPress site. Update- The vulnerable code has been patched and the plugin updated to version 2.2.7. Update- The vulnerable code has been patched and the plugin updated to version 2.2.7.
Timeline
Published on: 10/21/2022 16:15:00 UTC
Last modified on: 10/24/2022 15:23:00 UTC