This issue was addressed by implementing a new control flow for data transfer to and from the Web Console, which now uses encrypted HTTPS. The new control flow was implemented by removing the Data.toString() function call from the Web Console. As a result, untrusted data can no longer be deserialized, and the risk of a successful remote code execution is significantly reduced. As always, an organization can implement a risk assessment to determine if this issue is a concern for their environment.
Vulnerability Summary
The vulnerability is a remote code execution flaw in the Web Console that has been addressed by implementing a new control flow for data transfer to and from the Web Console. The new control flow was implemented by removing the Data.toString() function call from the Web Console. As a result, untrusted data can no longer be deserialized, and the risk of a successful remote code execution is significantly reduced.
Microsoft Office and Edge CVEs
Microsoft Office and Edge were each patched in October to address an issue that could allow remote code execution. Microsoft Office had a flaw which allowed remote code execution when the user opened a specially crafted file, while Edge had a flaw that allowed remote code execution when JavaScript was enabled and the user visited a website with malicious content. The vulnerabilities were addressed by removing both Data.toString() and Data.parseInt() calls from the Web Console API.
Vulnerability overview and bug fix
This is a vulnerability that poses a risk to an organization's security. An attacker can exploit the vulnerability by sending a maliciously crafted request to the Web Console, which allows remote code execution.
To fix this issue, the developer modified the control flow for data transfer to and from the Web Console so that it uses encrypted HTTPS. The new control flow was implemented by removing the Data.toString() function call from the Web Console. As a result, untrusted data can no longer be deserialized, and the risk of a successful remote code execution is significantly reduced.
Base64 Encode Remote Code Execution Vulnerability
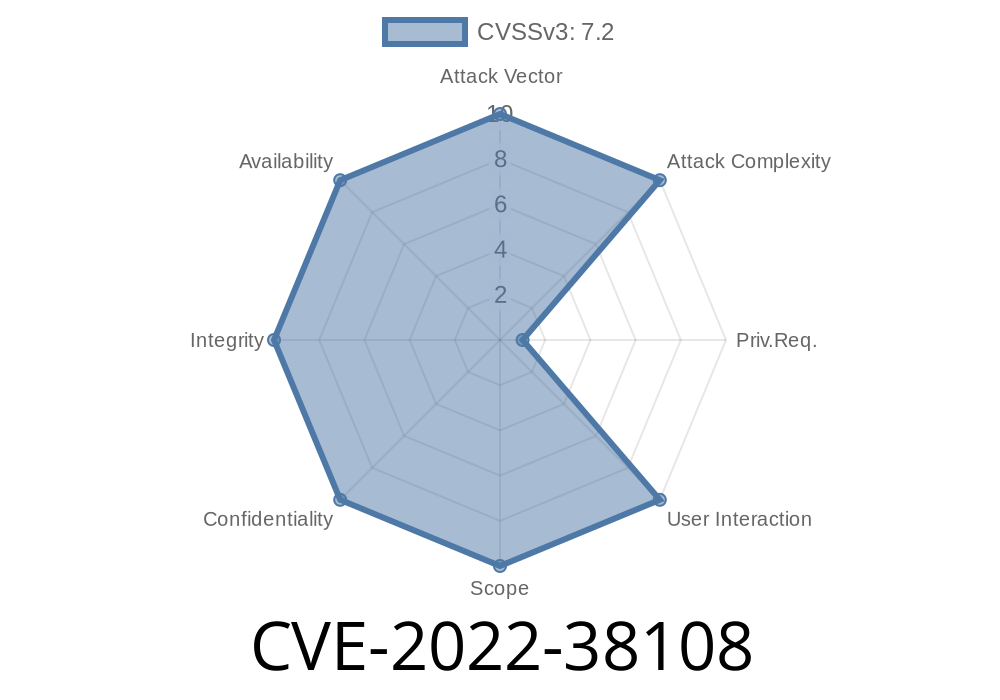
The Base64 Encode Remote Code Execution Vulnerability (CVE-2022-38108) is a vulnerability that allows an attacker to execute code remotely, without authentication. This vulnerability exists in the Web Console component and was addressed by removing the Data.toString() function call from the Web Console.
Timeline
Published on: 10/20/2022 21:15:00 UTC
Last modified on: 10/21/2022 19:00:00 UTC