When setting up DDNS on the router, it is recommended to use strong passwords, enable 2-step verification, and make sure that the email address is verified. If you choose to use the default username and password for DDNS, it is recommended to change them as soon as the vulnerability is known. The default username and password can be found on the first page of the router's setup wizard. In additional steps, the DDNS setup page allows users to specify the email address to receive configuration and status notifications. If email address is left unspecified, the router will use the username password fields for receiving notifications. An attacker can exploit this vulnerability by simply sending a request to change the configuration or status settings, and the router will respond with the default email address, allowing the attacker to cause undesired configuration changes. This can be easily done by sending a request to change the router's email address, and the attacker will receive the router's default email address. This issue affects: Linksys E1100, E1200, E1300, E1400, E2100, and E2500 Routers 1.0.
Summary
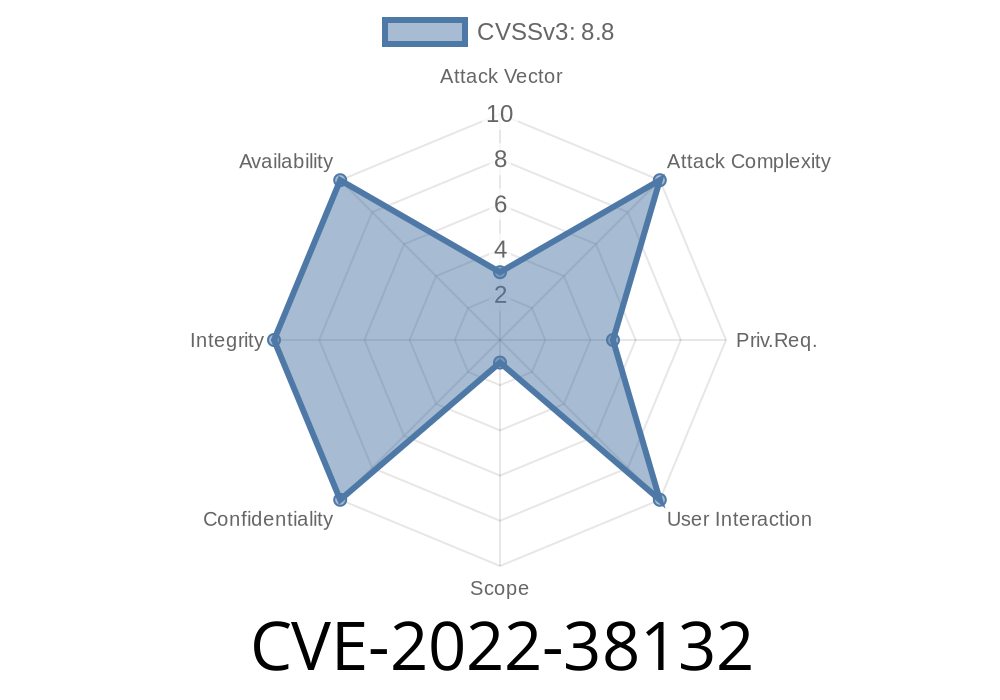
If you are using a Linksys router, the CVE-2022-38132 vulnerability can be exploited by sending a request to change the email address configuration or status settings. This will allow an attacker to cause undesired configuration changes. It is recommended to enable 2-step verification, use strong passwords, and change your DDNS username and password immediately after you are informed of this vulnerability.
Vendor Information
Sophos is the vendor for this vulnerability.
The following devices are affected: Linksys E1100, E1200, E1300, E1400, and E2500 Routers 1.0.
Timeline
Published on: 08/24/2022 00:15:00 UTC
Last modified on: 08/29/2022 15:52:00 UTC