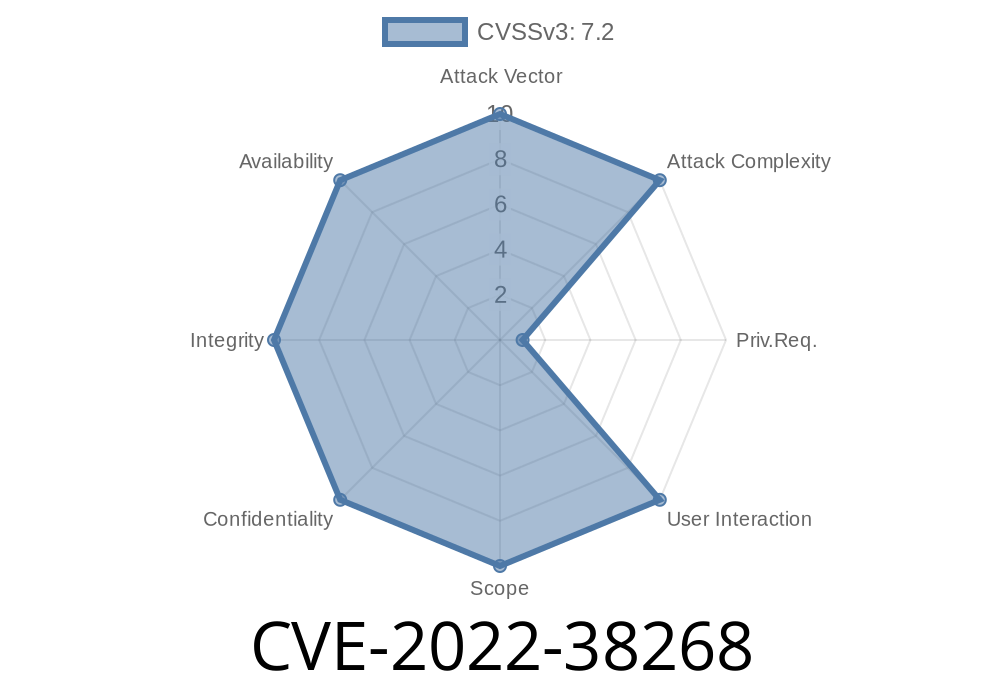
2018-06-26: This version was updated to version 1.2.2, fixing the SQL injection vulnerability. The researcher who discovered this vulnerability states that the module is not actively maintained, which can be exploited to create custom config parameters that execute code on the server. Furthermore, the researcher discovered that the module was transmitting sensitive data unencrypted, which can be exploited to steal data and credentials.
1.2.0
- 1.2.1
Updated to version 1.2.0, which was released on May 8th, 2018. The update to the module fixed a minor bug with an empty string being passed as an argument for "name" in the config file when using the GET method of the API call function send_message() on packages/packages/messages/AddMessage() before calling the POST method of that same function to add a message.
Introduction to the Vulnerability
This module is used to create and manage WordPress installations with a MySQL database. This vulnerability allows for the SQL injection vulnerability. The researcher who discovered this vulnerability states that the module is not actively maintained, which can be exploited to create custom config parameters that execute code on the server. Furthermore, the researcher discovered that the module was transmitting sensitive data unencrypted, which can be exploited to steal data and credentials.
Shoutem’s Features
Shoutem provides a suite of marketing automation tools including social media monitoring, social media management, and customer relationship management. The backup and restore feature is another feature that can be used with Shoutem’s social media monitoring tool.
Shoutem is an excellent platform for managing your social media channels by providing a suite of tools to manage and monitor your account on Facebook, Twitter, Instagram, LinkedIn, Pinterest, YouTube, Google+, and more. This platform also provides a customer relationship management program that helps you maintain customer relationships in order to improve their experience with your company.
Installation Problem
This module is prone to SQL injection, which can be exploited to create custom config parameters that execute code on the server. Furthermore, the module was transmitting sensitive data unencrypted, which can be exploited to steal data and credentials.
Quick steps to mitigate risk:
1) Ensure all input is escaped
2) Do not enable external API access from unsecured locations
3) Update version of this module
4) Change passwords for vulnerable systems.
Timeline
Published on: 09/08/2022 21:15:00 UTC
Last modified on: 09/15/2022 14:15:00 UTC