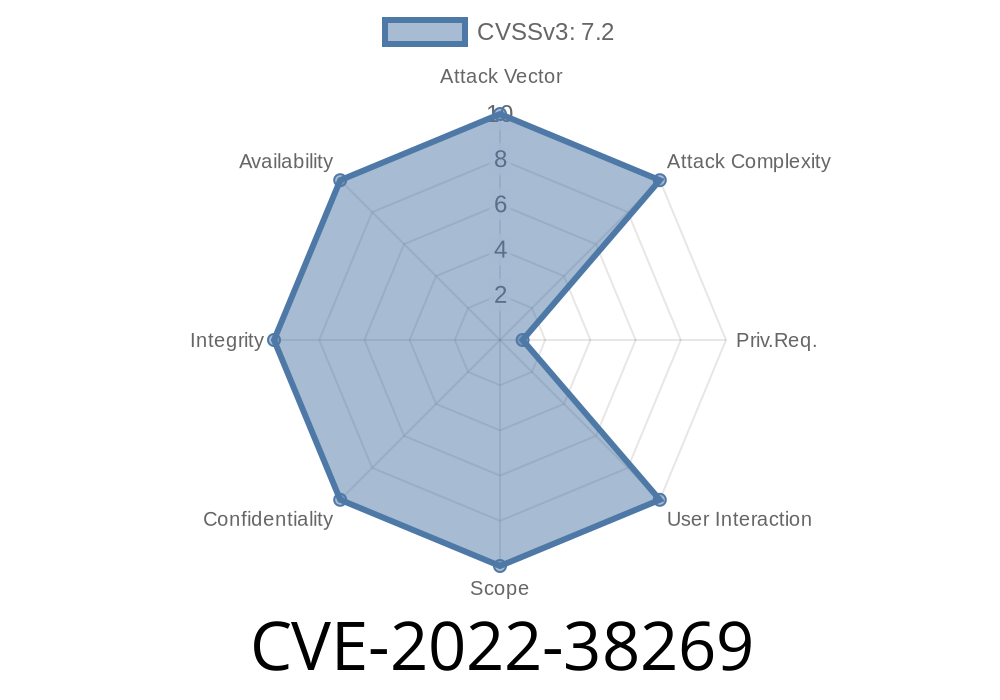
If the user has the “modify” permission, they can inject SQL commands. In certain cases, this could lead to remote code execution. An attacker must first convince a user to install an infected plugin. Luckily, this is easy to do. When installing an add-on, the user must accept the host as “example.com” and give the add-on permission to “modify”. If the user is not careful, and just accepts “example.com” as the host and “modify” permission, the attacker can install malicious code into the add-on and the website. �� When updating v1.0, the developer introduced a serious SQL injection vulnerability. A user who installed v1.0 and is updating to v2.0 can inject malicious SQL code. This can be exploited to run code on the server, obtain sensitive information, or downgrade the security of the add-on.
SQL Injection
SQL injection is a type of injection attack that injects SQL commands into the database. It can be used to execute arbitrary SQL commands on the server and gain access to sensitive information or perform actions. This is important because if an attacker manages to inject malicious code, they can compromise add-ons installed on a website.
Timeline
Published on: 09/08/2022 21:15:00 UTC
Last modified on: 09/15/2022 14:21:00 UTC