Cookie poisoning occurs when an attacker tricks a user into manually changing their cookie settings. The user is then susceptible to any session hijacking attacks the attacker performs in the future. Cookie poisoning is the most common form of session hijacking.
A successful exploitation of the CMS v1.6.0 cookie poisoning vulnerability allows attackers to hijack victims’ sessions.
To exploit this vulnerability, an attacker must be logged into the CMS v1.6.0 as a logged in user.
Once logged in, the attacker must click the “Session Settings” link on the left-hand menu.
The attacker must then click the “Advanced” link at the top of the page.
The attacker must then click the “Cookie Settings” link on the left-hand menu.
The attacker must then click the “Add” button on the right-hand menu and select the “Non-HTTPS cookie” option. The attacker must enter the site’s URL as the cookie’s domain.
Other types of session hijacking
Session hijacking can also occur in other ways than cookie poisoning.
Some session hijacking vulnerabilities are not related to cookies but rather to the HTTP protocol itself. Those vulnerabilities allow attackers to steal user data, install malicious software and perform a variety of other malicious actions.
See our blog post about Session Hijacking for more information on this topic.
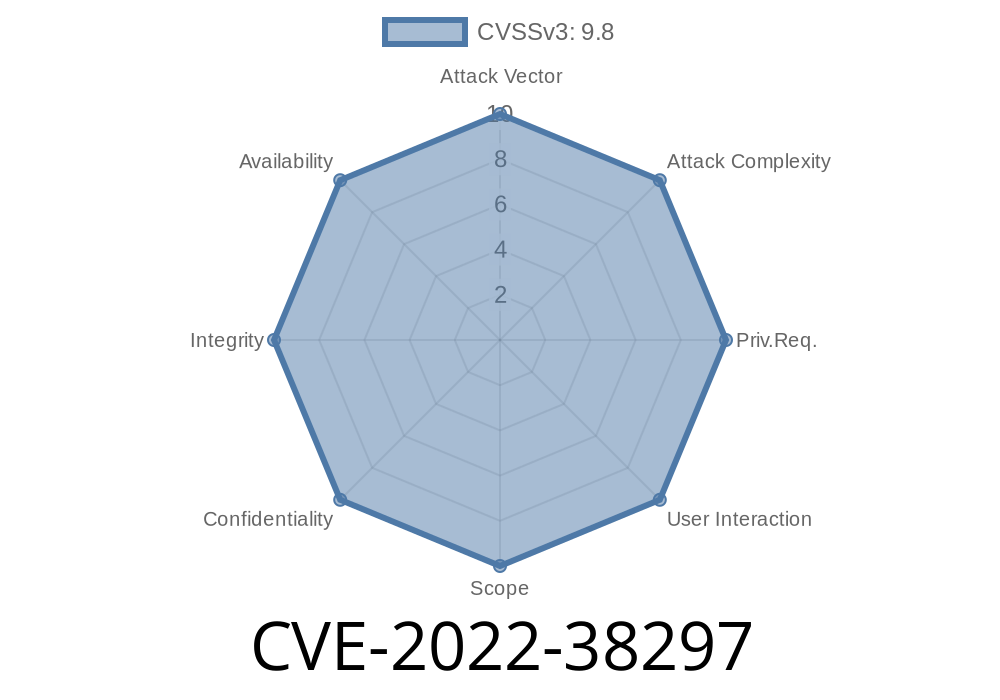
CVE-2022-38297: Stored cross-site scripting (XSS) vulnerability
This vulnerability provides attackers with the ability to execute arbitrary HTML and JavaScript code in the context of an affected site.
This vulnerability is present due to a flaw in WebKit’s handling of cookie attributes.
As a result, cookies are not blocked when sent by HTTP requests as they should be.
Cookie poisoning is the most common form of session hijacking. To exploit this vulnerability, an attacker must be logged into the CMS v1.6.0 as a logged in user. Once logged in, the attacker must click the “Session Settings” link on the left-hand menu. The attacker must then click the “Advanced” link at the top of the page. The attacker must then click the “Cookie Settings” link on the left-hand menu and select “HTTPS only” or “Same origin policy” from the dropdown menu for their cookies to be blocked from being exploited by cross-site scripting attacks.
Timeline
Published on: 09/12/2022 23:15:00 UTC
Last modified on: 09/15/2022 04:16:00 UTC