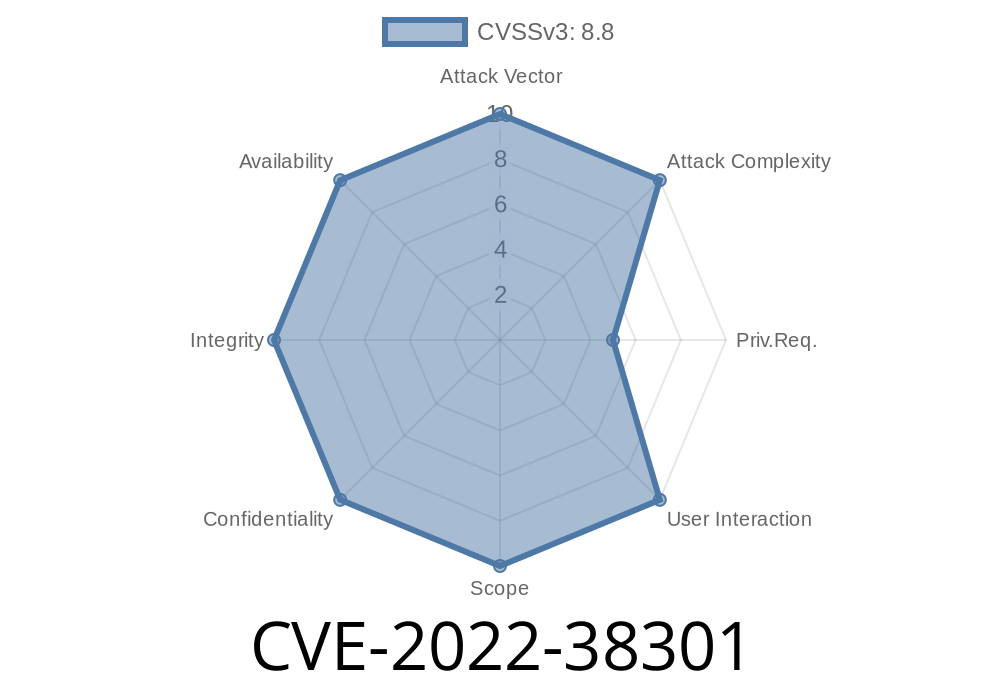
Onedev is a Node.js-based chat server with many plugins. Plugins can be written in any language, and it’s easy for an attacker to write a malicious plugin which can access files on the server. This can be done by uploading a malicious JAR file to the server, which will be executed by the onedev process. A remote attacker can upload a malicious JAR file on the server, which will be executed by the onedev process. The attacker can then download a restricted file from the server and upload it to another server. As a result, a remote attacker can access files on the server and escalate their privileges. Onedev v7.4.14 is vulnerable to a path traversal attack, due to the lack of input sanitization. When a user uploads a JAR file to the Onedev server, it is checked for the validity of the file extension. If the file extension is not valid, then the file is not processed and ignored. This makes it easy for an attacker to upload a malicious JAR file with a valid file extension to the Onedev server, which will be executed by the onedev process. An attacker can upload a malicious JAR file to the server, which will be executed by the onedev process. The attacker can then download a restricted file from the server and upload it to another server. As a result, a remote attacker can access files on the server and escalate
Onedev v7.4.14 Path Traversal Attack
Onedev is a Node.js-based chat server with many plugins. Plugins can be written in any language, and it’s easy for an attacker to write a malicious plugin which can access files on the server. This can be done by uploading a malicious JAR file to the server, which will be executed by the onedev process. A remote attacker can upload a malicious JAR file on the server, which will be executed by the onedev process. The attacker can then download a restricted file from the server and upload it to another server. As a result, a remote attacker can access files on the server and escalate their privileges.
Path Traversal Attack
When a user uploads a JAR file to the Onedev server, it is checked for the validity of the file extension. If the file extension is not valid, then the file is not processed and ignored. This makes it easy for an attacker to upload a malicious JAR file with a valid file extension to the Onedev server, which will be executed by the onedev process. An attacker can upload a malicious JAR file to the server, which will be executed by the onedev process. The attacker can then download a restricted file from the server and upload it to another server. As a result, a remote attacker can access files on the server and escalate their privileges.
Timeline
Published on: 09/14/2022 21:15:00 UTC
Last modified on: 09/16/2022 19:26:00 UTC