To exploit this issue, an attacker must trick a user to upload a file and then access the file via an HTTP request.
AeroCMS v0.0.1 was also found to have a cross-site scripting (XSS) vulnerability via the component /admin/config.php. This XSS vulnerability can be exploited by attackers to inject malicious code into the application.
Vulnerable URLs http://localhost/admin/config.php
http://localhost/admin/config.php?id=
Details of AeroCMS XSS Vulnerability
AeroCMS v0.0.1 contains a vulnerability that can be exploited by attackers to inject malicious code into the application, which would allow them to perform administrative actions on behalf of other users. The vulnerability exists in the component /admin/config.php, where an attacker is able to manipulate the $config["owner"] variable to execute arbitrary PHP code when accessed via an HTTP request. After exploitation, an attacker will have administrative privileges on the application and may be able to access private data or perform actions as authorized by another user.
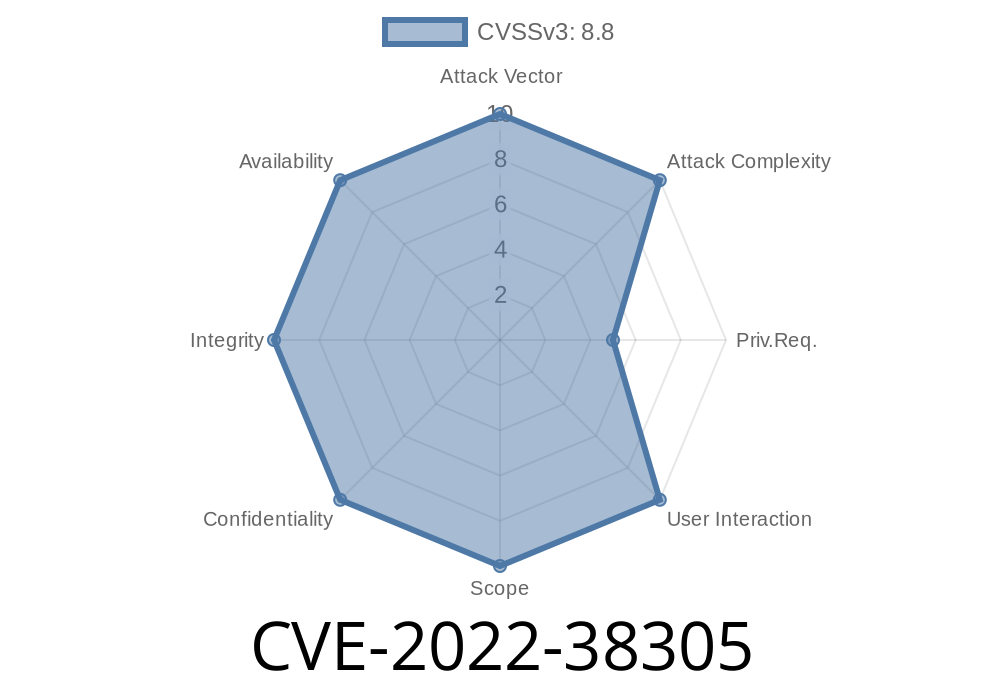
References CVE-2022-38305
AeroCMS v0.0.1
XSS vulnerability via the component /admin/config.php
Timeline
Published on: 09/13/2022 23:15:00 UTC
Last modified on: 09/17/2022 01:54:00 UTC