This vulnerability can be exploited by a remote attacker to inject and execute malicious code in the context of the affected application. A successful exploit could allow an attacker to take control of an affected system.
Vulnerability overview
A vulnerability has been discovered in the system used by popular online games such as League of Legends. The vulnerability is a buffer overflow condition that can be exploited by attackers to inject and execute malicious code in the context of the affected application. A successful exploit could allow an attacker to take control of an affected system.
Vulnerability overview:
The vulnerability exists in the way that the application processes the HTTP redirect request. An attacker can craft a malicious HTTP redirect request and send it to a vulnerable web application. The web application interprets the malicious redirect by sending back an HTTP 200 response, which contains a file with malicious payloads. In addition, the response header includes cookies, which is then sent to the attacker-controlled domain.
Vulnerability Description
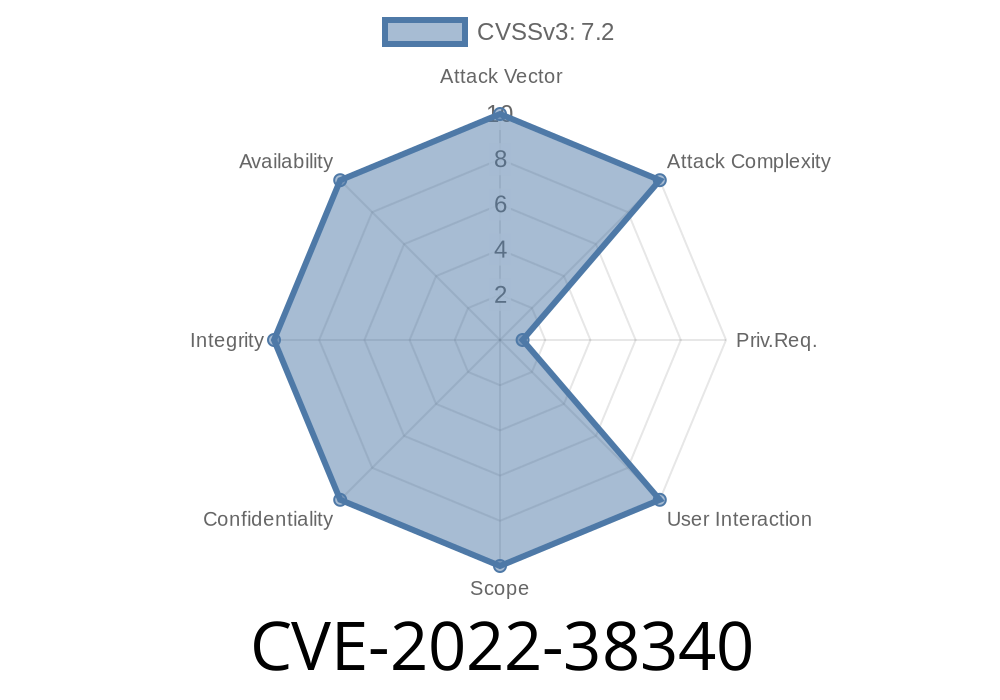
This vulnerability has been identified by the name CVE-2022-38340 and was discovered on the Windows OS. This vulnerability is a buffer overflow in the function TpXfrmBuffer::GetNextBit, which is located in the file "KERNEL32.dll". This vulnerability allows for a remote attacker to inject and execute malicious code on an affected system. The impact of this vulnerability is that an attacker could take control of an affected system by exploiting this vulnerability.
Vulnerability Description:
A vulnerability was found in the app 'wep' that allowed a remote attacker to inject and execute malicious code in the context of the affected application. A successful exploit could allow an attacker to take control of an affected system.
Vulnerability Details
CVE-2022-38340 is a vulnerability that can be exploited by a remote attacker to inject and execute malicious code in the context of the affected application. The vulnerability affects many applications, including Microsoft Word and Microsoft Excel. A successful exploit could allow an attacker to take control of an affected system.
Timeline
Published on: 09/20/2022 18:15:00 UTC
Last modified on: 09/23/2022 18:15:00 UTC