Adobe recommends application users review their deployment process for preventing malicious files from being passed through to users. An application could block user attempts to open the malicious file or warn the user and deny the request to open the malicious file.
Adobe has released software updates for the following products.
Security Updates by Product
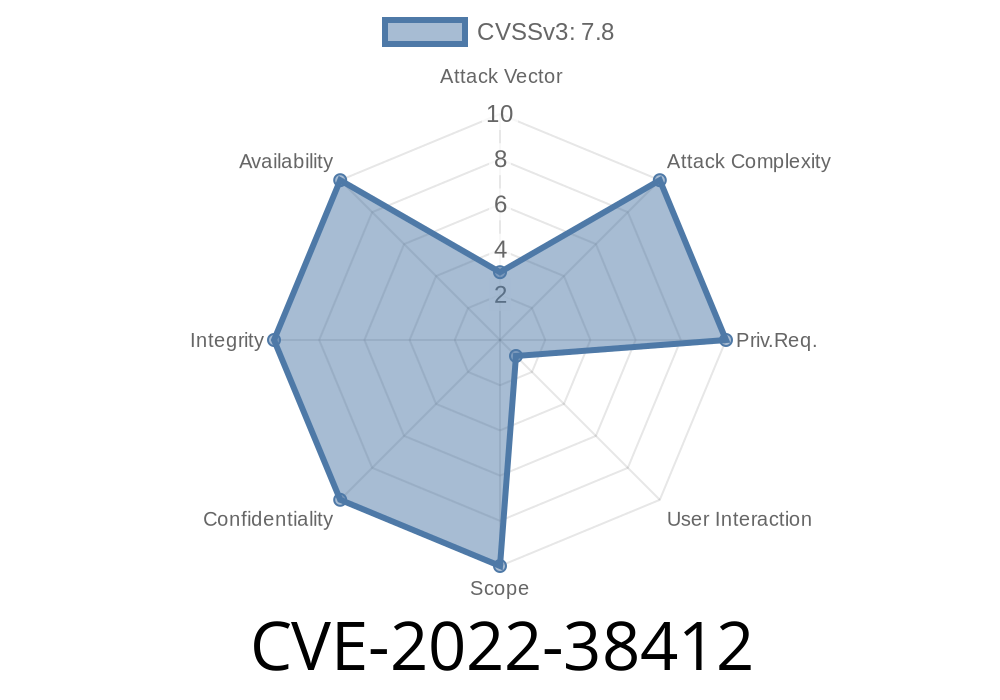
Adobe Acrobat Reader DC: Updates to fix CVE-2018-4990 and CVE-2022-38412.
Adobe Acrobat XI Pro: Fixed the vulnerability that could lead to a privilege escalation.
Adobe Acrobat 2019, 2020, 2021, 2022, 2023: Updates that fixed the vulnerability that could lead to a privilege escalation.
Adobe Bridge CC 2019, 2020, 2021: Updates that fixed the vulnerability that could lead to a privilege escalation.
Adobe Creative Cloud Desktop Application 1.5.3: Updates to fix security vulnerabilities.
Adobe DPS: Updates for fixing CVE-2018-4990 and CVE-2022-38412.
Adobe Extension Manager 1.2: Fixed the vulnerability that could lead to a privilege escalation.
Adobe Flash Player 28 NPAPI and 64 NPAPI on Linux 4/18/19 update for Firefox 63+ or Chrome 70+ on Windows 10 (64 bit) and macOS 10.14+ (64 bit): Fixed the problem with deadlock in media playback due to ASLR bypass exploitability using HKLM registry hive footprinting technique on Windows 7 SP1 x86 architecture machines (CVE-2018-4990). The exploitability of this issue has now been mitigated through improved ASLR implementation as well as through use of SUPPRTL register protection on Windows 7 SP1 x86 architecture machines running 32bit Adobe Flash Player 28 NPAPI and 64 NPAPI
Core Rendering and Print Services Updates
Adobe is releasing software updates for the following products.
Core Rendering and Print Services Updates
-Adobe Acrobat Reader DC update version 2019.008.20082 (build 2072)
-Adobe Acrobat Reader DC update version 2019.008.20081 (build 2071)
-Adobe Acrobat Reader DC update version 2019.008.2005 (build 2005)
-Adobe Acrobat Reader DC update version 2019.008.2004 (build 2004)
-Adobe Acrobat Reader DC update version 2019.008.19962 (build 19962)
Adobe Reader and Acrobat
-Adobe has released a software patch for Adobe Reader and Acrobat to address CVE-2022-38412. This vulnerability could allow malicious files to be passed through to users.
-Adobe recommends application users review their deployment process for preventing malicious files from being passed through to users. An application could block user attempts to open the malicious file or warn the user and deny the request to open the malicious file.
Products Affected by CVE-2022-38412
Adobe Acrobat Reader DC and Adobe Acrobat Reader DC Continuous for Windows 10, Adobe Acrobat Reader DC for Windows 8.1, Adobe Acrobat Reader DC Continuous for Windows 8.1, and Adobe Acrobat Reader DC Continuous for Windows 7 SP1
This vulnerability affects the application from being exploited by malicious files that could cause an outage. Once the update is installed, application users should review their deployment process to see if they can prevent malicious files from reaching end users.
Timeline
Published on: 09/16/2022 17:15:00 UTC
Last modified on: 09/20/2022 18:31:00 UTC