In the majority of cases, InDesign users are not aware of the malicious file existing on the system. The malicious file might be installed through social engineering, or in some cases, the user might unknowingly have a malicious file on the system via a drive-by-download. While InDesign does not prompt for installation through the file system, users must be cautious of where they install software from, as well as updates. Adobe recommends updating to the latest version of InDesign as soon as possible.
Adobe InDesign
Security Warnings
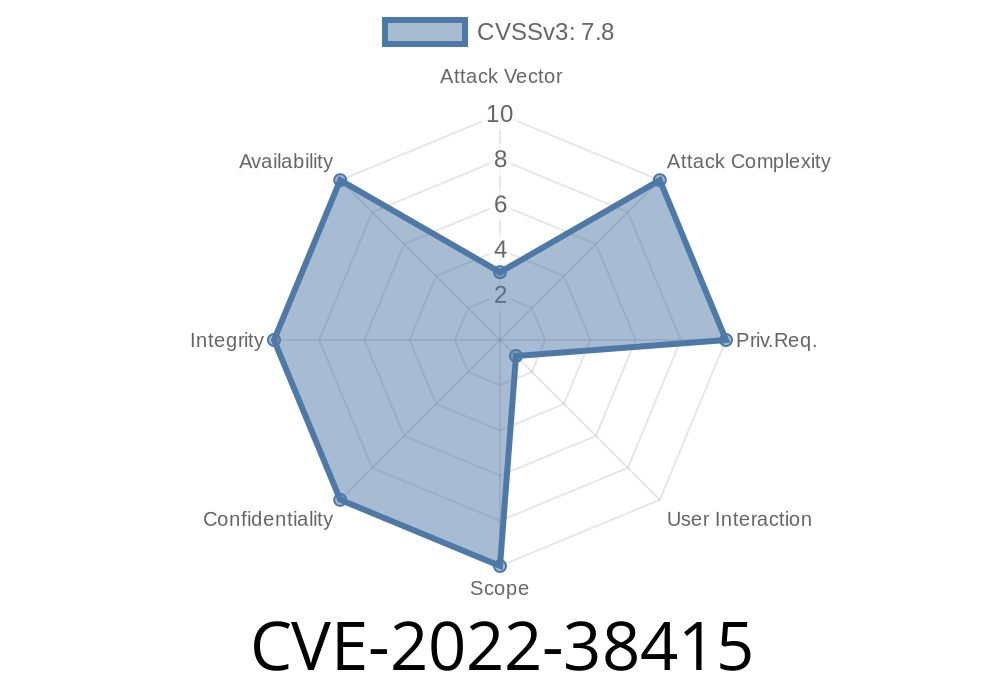
Even though InDesign is a robust application and produces high-quality graphics, it is not immune to security threats. One of the most common malicious files with InDesign is the CVE-2022-38415 file. This malicious file was first discovered in September 2014 and has proven to have a large impact on the company's system.
The malicious file contains a Trojan Horse that has the ability to infect computers with malware, steal data, and other nefarious activities. In some instances, this file can also be used for clickjack fraud and clickjacking scams.
The best way to prevent these attacks is by being cautious about where you install software from and only installing your software from trusted sources.
Adobe InDesign (9.0.1) and version information
Adobe InDesign (9.0.1) was released on October 3rd, 2017, and the following versions are still vulnerable to CVE-2022-38415:
- Adobe InDesign CS4
- Adobe InDesign CS4.5
- Adobe InDesign CS5
- Adobe InDesign CS6
- Adobe InDesign CC
Adobe Acrobat and Reader
Adobe Acrobat and Reader are two popular software programs that allow users to create, edit and print PDF documents. While the software is not inherently malicious, it can be exploited by a malicious file to cause security vulnerabilities.
In some cases, InDesign users may have a malicious PDF file on their system without even knowing about it. Since the PDF file is not associated with the program, the user might unknowingly open or save a document containing the file. This could result in the exploitation of CVE-2022-38415, which allows an attacker to remotely take control of a computer through a malicious PDF file.
Timeline
Published on: 09/16/2022 18:15:00 UTC
Last modified on: 09/20/2022 15:20:00 UTC