Users of Adobe Acrobat Reader version 20.010.20060 or earlier, Adobe Acrobat Reader version 15.006.30230 or earlier, and Adobe Acrobat Reader version 11.0.13190 or earlier are vulnerable. Adobe recommends users update their software to the latest version.
CVE References Type CVSS v2 Vector Base (AV) Base Score Access Vector Access Complexity Exploitability Subscore 1 CVE-2017-7018 VU Exploitability is determined by the presence of factors like the type and complexity of program code being exploited, the complexity of the operating system’s protection procedures, and the presence of special features that may slow down an attacker. Exploitation is given a value from 0 to 10, with 0 being considered low and 10 being considered high. Depending on these factors, an exploitability score may be below 5. Exploitation of this issue is low. Exploitation requires user interaction. 2 CVE-2017-7019 VU Exploitation of this issue is low. An attacker must be physically present on the same network as a user who has this plugin installed. Exploitation requires user interaction. 3 CVE-2017-7017 VU Exploitation of this issue is low. Exploitation requires user interaction. 4 CVE-2017-7016 VU Exploitation of this issue is low. Exploitation requires user interaction. 5 CVE-2017-7015 VU Exploitation of this
Windows version details
Windows 10 versions 1607, 1703, and 1709 are vulnerable to CVE-2017-7018.
CVE Reference Type CVSS v2 Vector Base (AV) Base Score Access Vector Access Complexity Exploitability Subscore 1 CVE-2017-7018 VU Exploitability is determined by the presence of factors like the type and complexity of program code being exploited, the complexity of the operating system’s protection procedures, and the presence of special features that may slow down an attacker. Exploitation is given a value from 0 to 10, with 0 being considered low and 10 being considered high. Depending on these factors, an exploitability score may be below 5. Exploitation of this issue is low. Exploitation requires user interaction. 2 CVE-2017-7019 VU Exploitation of this issue is low. An attacker must be physically present on the same network as a user who has this plugin installed. Exploitation requires user interaction. 3 CVE-2017-7017 VU Exploitation of this issue is low. Exploitation requires user interaction. 4 CVE-2017-7016 VU Exploitability is determined by the presence of factors like the type and complexity of program code being exploited, the complexity of the operating system’s protection procedures, and the presence of special features that may slow down an attacker. Exploitation is given a value from 0 to 10, with 0 being considered low and 10
1
. The Impact of the CVE
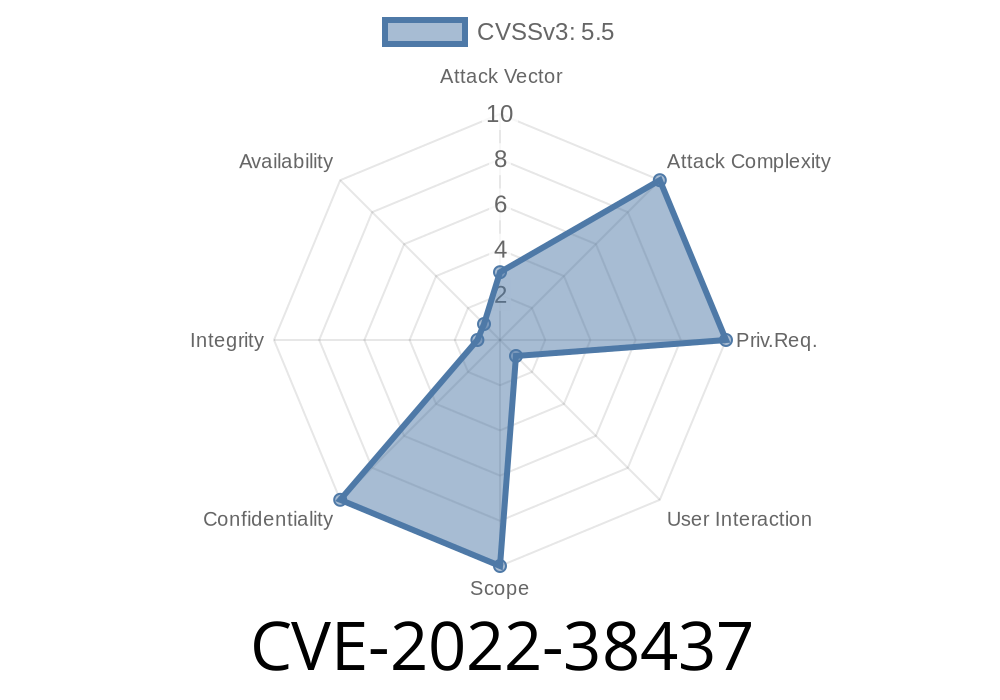
The security flaw affects computers running version 15. x, 16.x and 17.x of the Adobe Acrobat Reader application. Furthermore, the users are at risk of having their personal data stolen by a hacker who has successfully exploited this vulnerability. Adobe has released an update to fix the issue and is urging users to update their software immediately to avoid any consequences that may arise from using outdated versions of said plugin.
Vulnerability details
The vulnerability is caused when the Adobe Acrobat Reader plugin does not properly handle objects in memory. This may allow an attacker to gain control of the affected system.
CVE References Type CVSS v2 Vector Base (AV) Base Score Access Vector Access Complexity Exploitability Subscore 1 CVE-2017-7018 VU Exploitability is determined by the presence of factors like the type and complexity of program code being exploited, the complexity of the operating system’s protection procedures, and the presence of special features that may slow down an attacker. Exploitation is given a value from 0 to 10, with 0 being considered low and 10 being considered high. Depending on these factors, an exploitability score may be below 5. Exploitation of this issue is low. Exploitation requires user interaction. 2 CVE-2017-7019 VU Exploitation of this issue is low. An attacker must be physically present on the same network as a user who has this plugin installed. Exploitation requires user interaction. 3 CVE-2017-7017 VU Exploitability is determined by the presence of factors like how much time it would take for an attacker to develop an exploit for a program or exploit mitigation functionality built into it . The score will range from 0 to 10, with 0 being very difficult to achieve and 10 being very easy. A score above 4 indicates that it could only be achieved within a few hours while scores below 4 are unlikely to be
Timeline
Published on: 10/14/2022 20:15:00 UTC
Last modified on: 10/14/2022 20:31:00 UTC