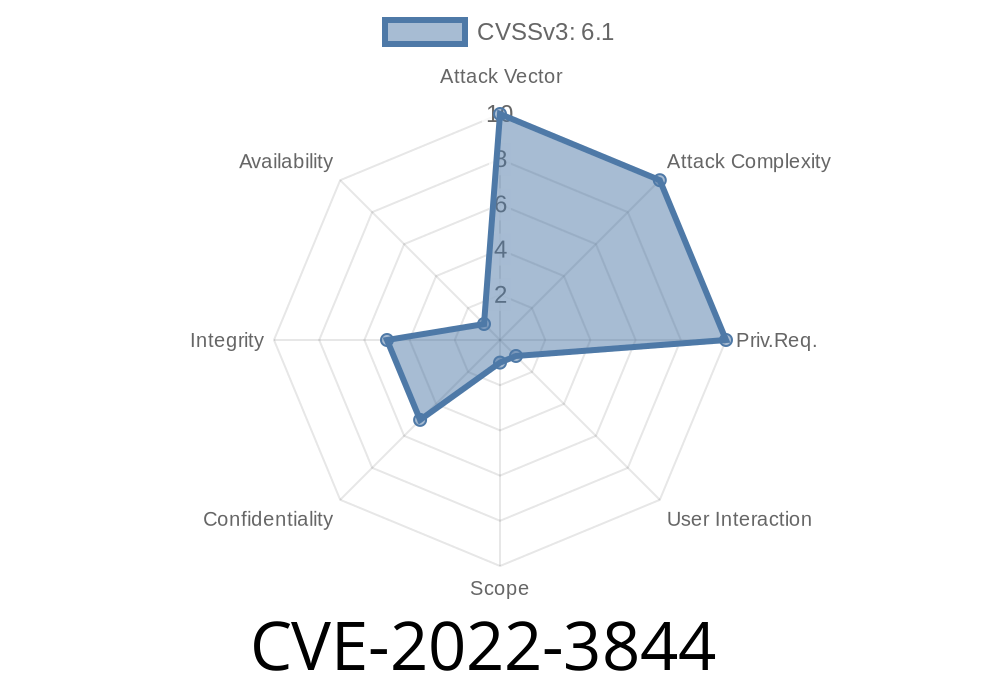
On October 8, 2022, security researchers discovered a problematic vulnerability in Webmin, a popular open-source server management tool. The flaw, registered as CVE-2022-3844 (internal reference: VDB-212862), relates to a classic web security misstep — cross-site scripting (XSS) in the xterm/index.cgi script. Attackers can exploit this issue over the internet, making it important for admins everywhere to learn about and patch this bug.
This exclusive walk-through unpacks CVE-2022-3844, explaining what went wrong, who’s affected, how it can be exploited, and — most importantly — how to fix it. We'll go hands-on with code snippets, reference the official patch, and demonstrate a working proof-of-concept (PoC).
What’s the Problem?
In Webmin 2.001, a specific CGI script, xterm/index.cgi, allows user input to be injected into the page without proper sanitization or escaping. This opens the door to an attacker inserting malicious JavaScript, which, when executed in the browser of a logged-in admin, can steal session tokens, redirect sessions, or perform actions on behalf of the user.
Vulnerability Type:
Cross-Site Scripting (XSS), reflected or stored depending on usage
CVE ID:
- CVE-2022-3844
Vuln Database Reference:
- VDB-212862
Affected Versions:
Webmin 2.001 (and possible earlier)
Fixed In:
- Webmin 2.003, patch d3d33af3cc3fd3a889c84e287a038b7a457d811
How Does the Attack Work?
An attacker crafts a URL containing a malicious XSS payload. When a Webmin admin or user visits this URL — for example, as the result of a phishing email or malicious site — the script in xterm/index.cgi reflects the unsanitized payload right back in the page.
Below’s a simplified illustration of what might have gone wrong
# xterm/index.cgi (simplified pseudo-code)
print "Content-Type: text/html\n\n";
my $term_name = param('term'); # fetches 'term' parameter from the URL
print "<h1>Terminal: $term_name</h1>"; # outputs directly without sanitizing
# If someone visits /xterm/index.cgi?term=<script>alert(1)</script>
# The <script> runs as soon as the page is loaded!
In this example, the term parameter is used directly in the HTML output without filtering out HTML tags or content.
`
https://example.com:10000/xterm/index.cgi?term=%3Cscript%3Ealert('XSS!!')%3C%2Fscript%3E
Example Exploit URL
https://your-webmin-host:10000/xterm/index.cgi?term=<script>alert(document.cookie)</script>;
Once the admin opens this, JavaScript executes in their context — their session tokens or other sensitive data could be sent to an attacker.
Theft of active admin sessions
- Creation/deletion of users
The Fix: Patch and Mitigation
The best way to mitigate this vulnerability is upgrade Webmin to version 2.003 or later. The official patch — commit hash d3d33af3cc3fd3a889c84e287a038b7a457d811 — escapes user-input before echoing it back.
How the Patch Looks
# Instead of outputting $term_name raw,
use WebminCore;
my $safe_term = &html_escape($term_name);
print "<h1>Terminal: $safe_term</h1>";
Here, the html_escape function makes sure any HTML tags are rendered harmlessly as text.
Recommendations
- PATCH IMMEDIATELY: Upgrade to Webmin 2.003+.
Educate users not to click untrusted Webmin links.
- Monitor logs for suspicious access to /xterm/index.cgi.
If you’re running Webmin 2.001 or earlier, you are at risk. Don’t ignore this: XSS on an admin tool is a real threat to your servers!
References
- CVE-2022-3844 @ NIST NVD
- VDB-212862
- Webmin official GitHub Patch d3d33af3cc3fd3a889c84e287a038b7a457d811
- Webmin Releases
Final Thoughts
CVE-2022-3844 reminds us how user input must always be treated with suspicion, especially in internet-facing admin tools. Patch your Webmin today — and never trust what your browser tells you!
*This post was written exclusively for infosec professionals and sysadmins who like plain English and practical advice. Always stay patched. Always stay safe.*
Timeline
Published on: 11/02/2022 20:15:00 UTC
Last modified on: 03/01/2023 18:16:00 UTC