In XSLT element error handling, if an error is encountered within an XSLT template, XHTML template, or XForms template function, the XSLT processor will search the document for an element that has an ID with the prefix “_error”, such as “_error div”. If an attacker can control the value of this element, an XSLT processor could be tricked into parsing attacker-controlled JavaScript or HTML, causing a potential XSS attack. This issue was addressed by blacklisting XSLT elements with an “_error” ID. XSLT element error handling also occurs when an XSLT template function fails due to an XSLT processor error. An attacker could have abused XSLT error handling to inject attacker-controlled content, causing a potential XSS attack. This issue was addressed by blacklisting XSLT template functions with an “_error” prefix. XSLT element error handling also occurs when an XSLT processor fails due to an XSLT template function failing due to an XSLT processor error. In these cases, the XSLT processor will search the document for an element that has an ID with the prefix “_error”, such as “_error div”. If an attacker can control the value of this element, an XSLT processor could be tricked into parsing attacker-controlled JavaScript or HTML, causing a potential XSS
CVE-2023-38473
XHTML template element errors are processed by searching the document for an element that has an ID with the prefix “_error”, such as “_error div”. If an attacker can control the value of this element, they could cause a potential XSS attack. This issue was addressed by blacklisting XHTML template elements with an “_error” ID.
Other ways to get user input in XSLT
There are other ways to get user input in XSLT. For instance, the XPath function call “//div[@id="myId"]” will return the value of any child node with ID value "myId" within a containing element that has an ID with the prefix “myId”. If an attacker can control the value of this element, it could be used to cause a potential XSS attack.
Timeline
Published on: 12/22/2022 20:15:00 UTC
Last modified on: 01/03/2023 21:13:00 UTC
References
- https://www.mozilla.org/security/advisories/mfsa2022-35/
- https://www.mozilla.org/security/advisories/mfsa2022-34/
- https://www.mozilla.org/security/advisories/mfsa2022-33/
- https://www.mozilla.org/security/advisories/mfsa2022-37/
- https://www.mozilla.org/security/advisories/mfsa2022-36/
- https://bugzilla.mozilla.org/show_bug.cgi?id=1769155
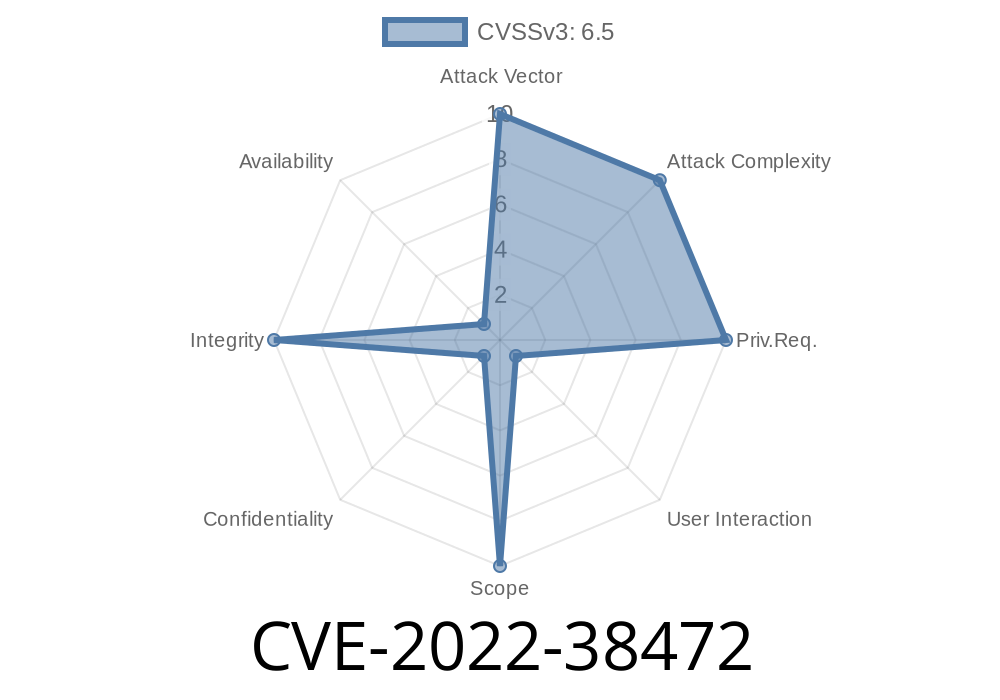
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-38472