If you are running any of the above versions, we strongly recommend updating your software. You can do so by either visiting the website of the vendor or by updating your system manually. For Debian/Ubuntu users, the upgrade instructions can be found here. For CentOS/Red Hat users, the upgrade instructions can be found here.
If you use the Debian/Ubuntu/Mageia repositories, we have updated the packages to version 10.0.10, 10.0.11, and 10.0.12. These updates address the issues outlined in this post. For CentOS/Red Hat/Fedora users, we have updated the packages to version 10.0.10 and 10.0.11. These updates address the issues outlined in this post.
Summary
If you are running any of the above versions, we strongly recommend updating your software. You can do so by either visiting the website of the vendor or by updating your system manually. For Debian/Ubuntu users, the upgrade instructions can be found here. For CentOS/Red Hat users, the upgrade instructions can be found here.
What is Apache TomEE?
Apache TomEE is an open-source Java EE and WebSocket-based application server. This software package is the official implementation of the JPA specification and has been certified by the Open Web Application Security Project (OWASP). The Apache TomEE distribution includes support for a vast number of application server features, including HTTP, REST, Servlet, JDBC, JAX-RS, JMS, and other enterprise features.
Description of the issue
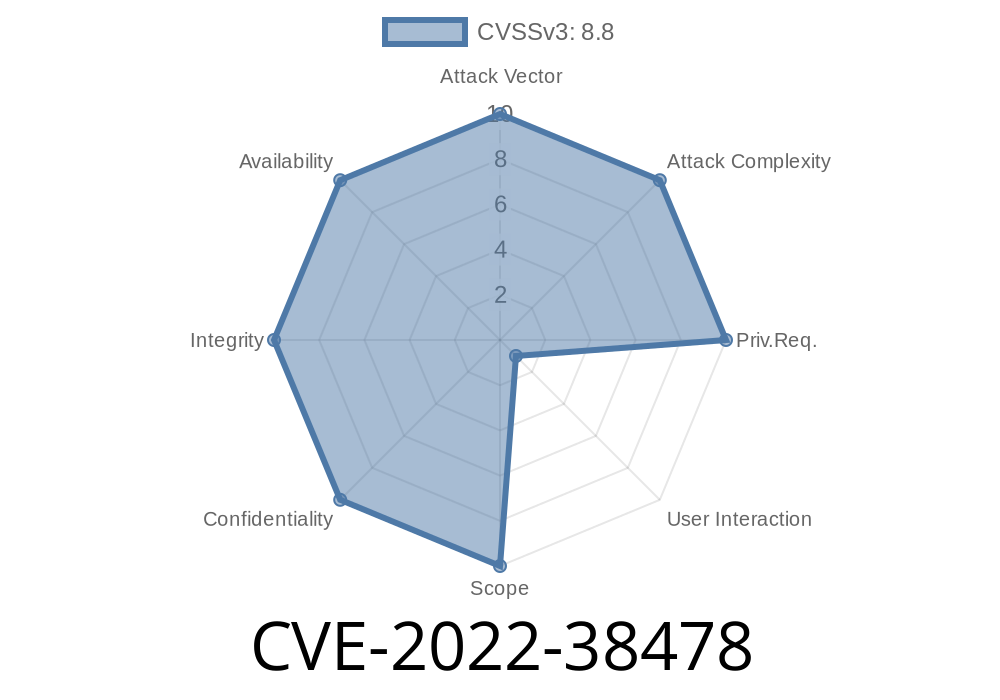
A vulnerability in the handling of DOCTYPE declarations in XSLT has been found. This vulnerability impacts all versions of XSLT, including those listed above.
Timeline
Published on: 12/22/2022 20:15:00 UTC
Last modified on: 12/31/2022 02:35:00 UTC
References
- https://bugzilla.mozilla.org/buglist.cgi?bug_id=1770630%2C1776658
- https://www.mozilla.org/security/advisories/mfsa2022-35/
- https://www.mozilla.org/security/advisories/mfsa2022-34/
- https://www.mozilla.org/security/advisories/mfsa2022-33/
- https://www.mozilla.org/security/advisories/mfsa2022-37/
- https://www.mozilla.org/security/advisories/mfsa2022-36/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-38478