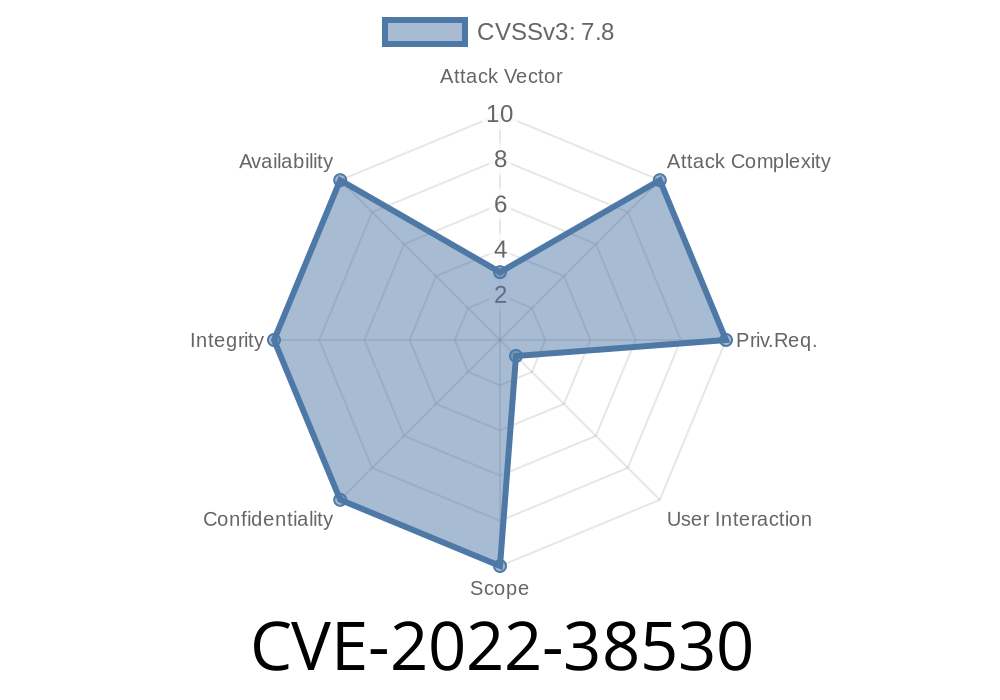
This issue could potentially lead to denial of service. This issue was resolved by updating ISOM_IOD to version 1.1.1.
SSH keys have a limited lifetime, so it’s a good idea to remove old keys from your servers at least once a year.
If you have several servers that need to be updated at the same time, it’s a good idea to update them one at a time.
If you’re using automated software installation tools, make sure they don’t install the hotfix on the master branch. Any automatic update process that installs the master branch will overwrite the hotfix with a new version, which will cause the update to fail.
Thoughts on Disabling SSH
Key Logging
SSH keys are used to access your servers remotely. Their use is not limited to the server itself, however. SSH keys allow for remote access from anywhere on the internet, which can be beneficial for development or building a website. Due to this, it is important that you follow security best practices when using SSH keys. In particular, there's an issue with older versions of ISOM_IOD that could potentially lead to denial of service if left unchecked. As such, it's a good idea to update your key at least once a year and make sure that any automated software installation tools do not install the hotfix on the master branch of the software. This way, you'll ensure that any updates happen seamlessly and without error.
Installing a hotfix
The hotfix must be installed into the system directory where the SSH server is located.
Install the hotfix by running the following command:
sudo yum -y install ssh-krb5-hotfix
Check if you need the hotfix
Have you installed ISOM_IOD on a server before? If so, then you should check to see if the hotfix is needed. To do this, use ssh to connect to the server and run the following command:
apt-cache policy isom_iod
If your server policy is no longer available at /etc/apt/preferences.d/isom_iod.pref , then you need to apply the hotfix.
Timeline
Published on: 09/06/2022 23:15:00 UTC
Last modified on: 09/10/2022 02:51:00 UTC