Exploiting this issue would allow a remote attacker to take control of an affected device. TOTOLINK-720R v4.1.5cu.374 is vulnerable; however, there are no reported exploits publicly available. TOTOLINK-720R v4.1.5cu.374 is a business VoIP phone that runs on the OFX protocol. An attacker can take advantage of this issue by sending an email with a malicious link that is sent to the affected device. When the device is opened in its default web browser, the device's web interface can be exploited to cause a remote code execution.
Vulnerability Details
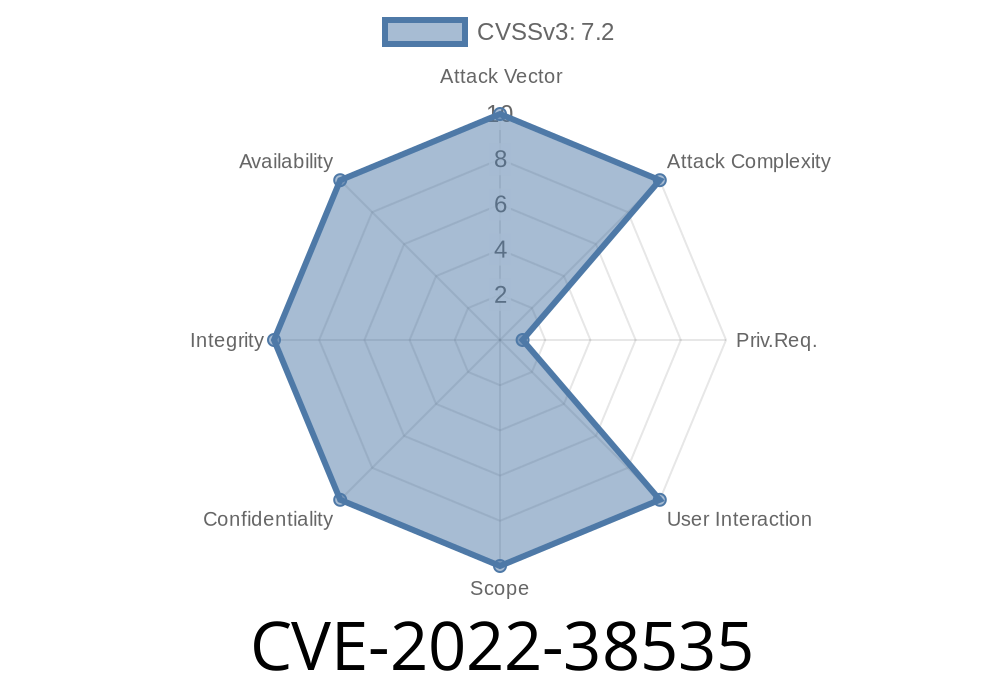
CVE-2022-38535 is a remote code execution vulnerability in TOTOLINK-720R v4.1.5cu.374 that can be exploited via email, the web interface, or any other method of delivery. Exploiting this issue would allow a remote attacker to take control of an affected device. The vulnerability is due to insufficient input validation when processing OFX messages from the device's web interface and causes the device to execute malicious JavaScript as shown below:
Vulnerable URLs https://www.totolink.com/user_login?
https://my.totolink.com/
https://voip.totolink.com/vw-config-guide.html
https://www.totolink-720r.tm/default-profile-menu/whats-new
# Software version of affected device
Manufacturer: TOTOLINK
Device type: Business VoIP phone
Software version: 4.1.5cu.374
Timeline
Published on: 09/15/2022 18:15:00 UTC
Last modified on: 09/20/2022 12:36:00 UTC