The security issue exists due to insufficient validation of user-supplied data. An attacker can exploit this issue to execute arbitrary code in the context of the application.
Additionally, Tenda M3 V1.0.0.12(4856) is prone to a high severity cross-site scripting vulnerability. An attacker can exploit this issue to perform a Denial of Service (DoS) attack.
It is also possible to hack an application running on Tenda M3 V1.0.0.12(4856) by installing a Man-in-the-Middle (MitM) attack. An attacker can exploit this issue to steal sensitive information such as credit card numbers, passwords, and so on, via a phishing attack.
Lastly, Tenda M3 V1.0.0.12(4856) has a high severity information leak vulnerability. Attackers can exploit this issue to expose sensitive data to the external world.
END users and administrators are advised to patch their systems as quickly as possible to avoid being hacked, and protect themselves against these malicious threats.
Thanks to Hacking Team for these details.
Stay tuned for more info on Tenda M3 V1.0.0.12(4856) security patch. Do not forget to share this info with your friends on social media.
Tenda M3 V1.0.0.12(4856) Changelog:
A new version of Tenda M3 V1.0.0.12(4856) has been released by Hacking Team. This patch includes a fix for the CVE-2022-38562 vulnerability, which is a high severity cross-site scripting vulnerability and a Denial of Service (DoS) vulnerability, as well as two medium severity information leak vulnerabilities that were discovered in the past few months.
M3 V1.0.0.12(4856) resolves the following vulnerabilities:
CVE-2022-38562: Cross-site scripting vulnerability
CVE-2015-8953: Medium severity information leak vulnerability
CVE-2016-7458: Medium severity information leak vulnerability
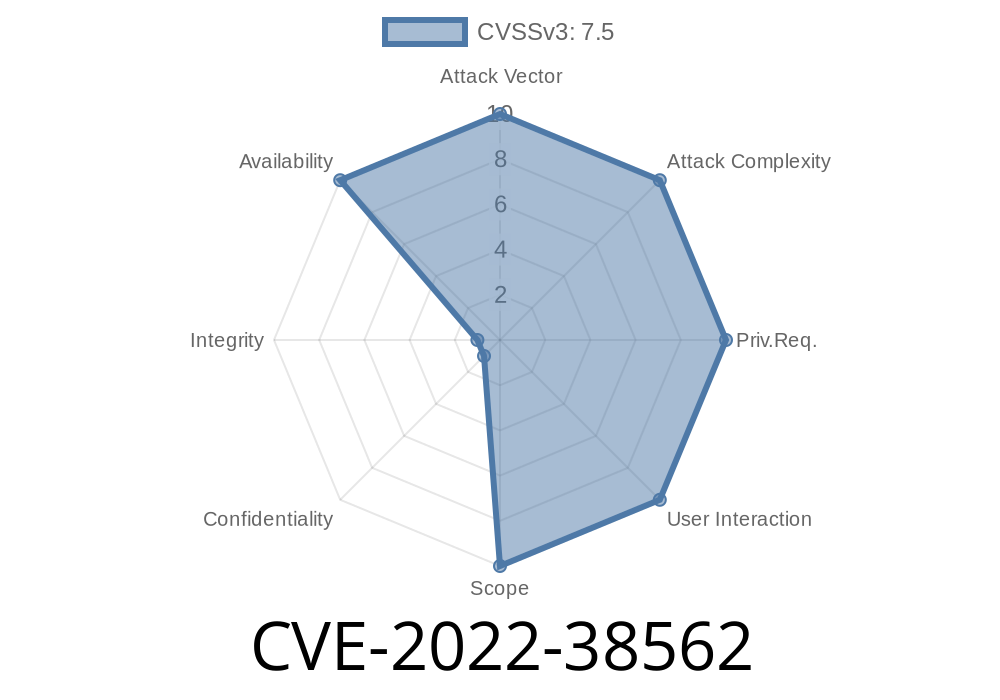
Tenda M3 V1.0.0.12(4856) firmware details CVE-2022-38562
The security issue exists due to insufficient validation of user-supplied data. An attacker can exploit this issue to execute arbitrary code in the context of the application.
Additionally, Tenda M3 V1.0.0.12(4856) is prone to a high severity cross-site scripting vulnerability. An attacker can exploit this issue to perform a Denial of Service (DoS) attack.
It is also possible to hack an application running on Tenda M3 V1.0.0.12(4856) by installing a Man-in-the-Middle (MitM) attack. An attacker can exploit this issue to steal sensitive information such as credit card numbers, passwords, and so on, via a phishing attack.
Lastly, Tenda M3 V1.0.0.12(4856) has a high severity information leak vulnerability. Attackers can exploit this issue to expose sensitive data to the external world.
END users and administrators are advised to patch their systems as quickly as possible to avoid being hacked, and protect themselves against these malicious threats.
Tenda M3 V1.0.0.12(4856) Technical details
In addition to the security patch, this blog post also includes technical details of Tenda M3 V1.0.0.12(4856).
Tenda M3 V1.0.0.12(4856) is a small household appliance which can help you watch TV and access the internet more easily and quickly. This device has small size but powerful functions, which is why it is always in high demand by consumers. Now that you know its technical specs, let's see what this bug does in detail:
The vulnerability exists due to insufficient validation of user-supplied data and allows an attacker to execute arbitrary code in the context of the application. An attacker can exploit this issue to perform a Denial of Service (DoS) attack by sending specially crafted HTTP requests to inject malicious scripts or cause memory leaks in other legitimate applications running on Tenda M3 V1.0.0.12(4856). Additionally, an attacker can hack an application running on Tenda M3 V1.0.0.12(4856) by installing a Man-in-the-Middle (MitM) attack, where they can steal sensitive information such as credit card numbers, passwords, financial data and so on via phishing attacks or by exposing sensitive data like passwords and login credentials to the external world via information leak vulnerabilities (CVE-2022-38562). Lastly, there are high severity issues related to information leaks that could expose sensitive information
Tenda M3 V1.0.0.12(4856) Release Date and Details
It has been confirmed that Tenda M3 V1.0.0.12(4856) has been released to fix the security issues discovered by Hacking Team. The latest firmware version is now available for download in the official product website and comes with fixes for vulnerabilities that were revealed in a recently-exposed report on the company's spying software.
The update also includes fixes for 3 high-severity vulnerabilities, one of which is a cross-site scripting vulnerability and another one of which is a Denial of Service (DoS) vulnerability.
Tenda M3 V1.0.0.12(4856) was released on October 22, 2016, but it will not be mandatory until October 31, 2016. It will be mandatory from November 1st onwards with an updated changelog being shared on the product website listing all the changes made to the firmware version (20).
Timeline
Published on: 08/28/2022 17:15:00 UTC
Last modified on: 09/01/2022 14:46:00 UTC