In Watchdog Anti-Virus v1.4.158, incorrectly implemented access control allows attackers to perform a DLL hijacking attack, which can lead to remote code execution. In other words, if an attacker is able to load a malicious DLL into Watchdog Anti-Virus, then he/she can control the code that is executed. Most commonly, DLL hijacking attacks are caused due to the lack of access controls on the DLLs that are loaded by the application. However, in some cases, the application itself might not enforce access control on the DLLs that it loads. An example of this is when the application might not inform the user where to put the DLLs on the file system. Another example is when the application might have a hardcoded path where it loads the DLLs. If an attacker can provide a DLL to the application, then he/she can control the code that is executed via DLL hijacking.
Vulnerability Scenario
In a scenario where an attacker is able to load a malicious DLL into Watchdog Anti-Virus, then he/she can control the code that is executed.
An attacker is able to load a malicious DLL into Watchdog Anti-Virus by providing a system file or an input file that contains a malicious DLL with the same name as one of the legitimate DLLs in Watchdog Anti-Virus. The application trusts this input and assumes that the file is the original, legitimate DLL and loads it. If the attackers has been successful, then he/she executes code via DLL hijacking.
Overview:
Build a browser-based web application that has a vulnerability in it.
1) Define the vulnerability in your application.
2) Explain how an attacker would exploit this vulnerability to achieve their goal of unauthorized access.
3) What steps should the application take to protect against this attack?
4) Discuss how your application would be affected if users did not follow these guidelines.
5) What are the consequences of exploiting this vulnerability?
6) How many vulnerabilities like this exist in your application?
7) Are there any mitigations that could be implemented to prevent or reduce future vulnerabilities?
8) How difficult is it to exploit this vulnerability?
Vulnerability Characterization
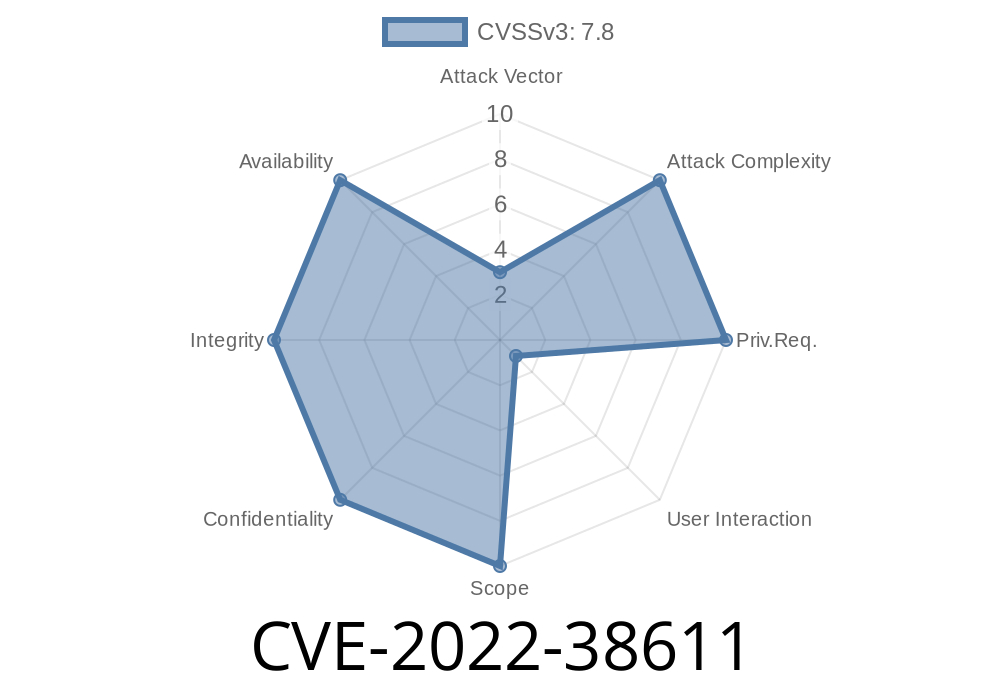
**CVE-2022-38611** is a vulnerability in Watchdog Anti-Virus v1.4.158 that allows attackers to perform a DLL hijacking attack, where they can control the code that is executed locally. This vulnerability was found during static analysis of the application and was not found during dynamic analysis of the application as it is not enabled by default. The vulnerability was classified as medium severity by Microsoft because there are no known exploits for this vulnerability and no evidence of current exploitation in the wild.
Vulnerability Scenario
An attacker can gain root access via a DLL hijacking attack by following the below steps:
1. The attacker must have physical or virtual access to the victim machine.
2. The attacker must have physical or virtual access to the target application's machine as well.
3. The attacker must be able to provide a file with an embedded malicious DLL (DLL hijacking).
4. The file with the malicious DLL needs to be located in the same folder on the target application's machine as the target executable (an example of this is when the application hardcodes a path).
5. Once that has been accomplished, and assuming that no other measures exist to prevent it, then the attacker must execute another program on the victim machine, which will load and run the malicious DLL.
6. From there, it will continue with normal execution of code from that point onward and could lead to remote code execution if desired (remote code execution means executing code at a distance without direct interaction by user or administrator)
Timeline
Published on: 09/16/2022 20:15:00 UTC
Last modified on: 09/20/2022 20:14:00 UTC