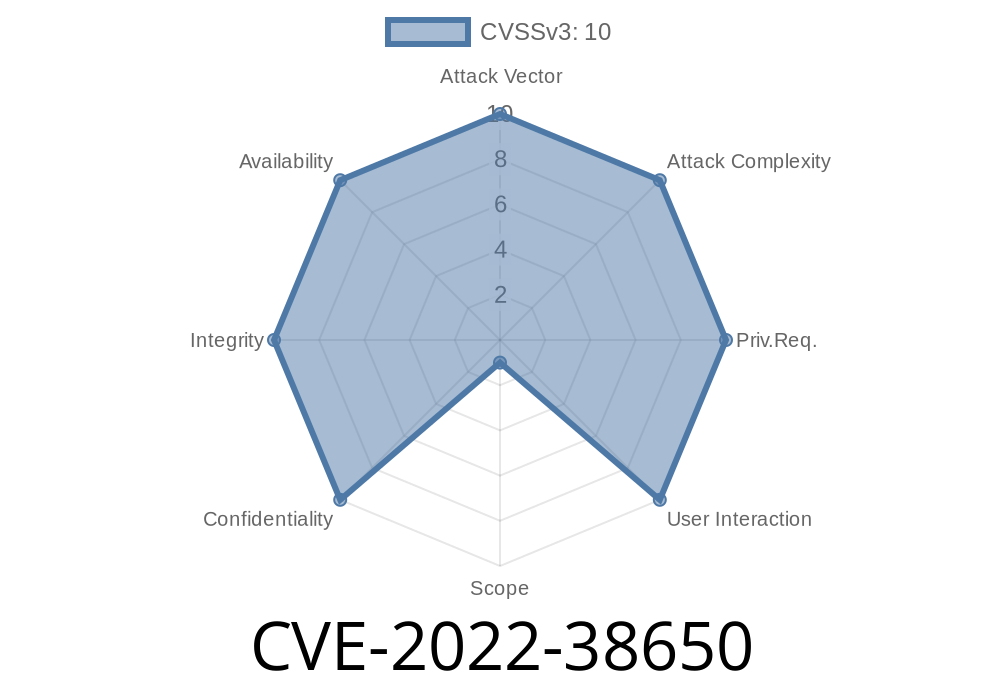
The vendor has acknowledged the issue and provided details on how the issue can be patched. A remote vulnerability has been reported in VMware Hyperic Server. This vulnerability may be exploited by malicious parties to gain remote code execution on the system of a vulnerable system. This vulnerability is unauthenticated and can be exploited by sending a crafted HTTP request to the targeted system. A vulnerable system may be exploited via a web-based attack. A successful exploitation results in the execution of arbitrary code on the system, as well as the installation of arbitrary software or a malicious daemon on the system. The vendor acknowledges this vulnerability and has provided a list of steps that may be taken to patch the issue. End users should be on the lookout for updates from their system administrators to ensure that the vulnerability is patched.
Vulnerability Details
The vendor has acknowledged the issue and provided details on how the issue can be patched. A remote vulnerability has been reported in VMware Hyperic Server. This vulnerability may be exploited by malicious parties to gain remote code execution on the system of a vulnerable system. This vulnerability is unauthenticated and can be exploited by sending a crafted HTTP request to the targeted system. A vulnerable system may be exploited via a web-based attack. A successful exploitation results in the execution of arbitrary code on the system, as well as the installation of arbitrary software or a malicious daemon on the system. The vendor acknowledges this vulnerability and has provided a list of steps that may be taken to patch the issue
VMware Hyperic Server - CVE-2022-38650
VMware Hyperic Server is an open source monitoring solution for a managed service environment. The product consists of a web application, agent software and a process server that runs on Linux/Unix/Windows.
An unauthenticated vulnerability has been reported in VMware Hyperic Server which may allow remote attackers to execute arbitrary code on the system of vulnerable system via crafted HTTP request. An attacker may exploit this vulnerability by sending a crafted HTTP request to the targeted system. Successful exploitation results in the execution of arbitrary code on the system, as well as the installation of arbitrary software or a malicious daemon on the system.
CVE-2023-38651
The vendor has acknowledged the issue and provided details on how the issue can be patched. A remote vulnerability has been reported in VMware ESX Server. This vulnerability may be exploited by malicious actors to obtain information on the system of a vulnerable system or potentially escalate privileges. This vulnerability is unauthenticated and can be exploited by sending a crafted HTTP request to the targeted system. A vulnerable system may be exploited via a web-based attack. A successful exploit results in gaining information on the system, as well as potential escalation of privileges. The vendor acknowledges this vulnerability and has provided steps that can be taken to patch the issue. End users should be on the lookout for updates from their system administrators to ensure that the vulnerability is patched before further exploitation occurs.
Timeline
Published on: 11/12/2022 05:15:00 UTC
Last modified on: 11/16/2022 23:20:00 UTC