The exotel-py package was released on Jan. 11, 2018. As of Feb. 6, 2018, there are over 6,000 downloads and at least two forks of the package that have been updated to remove the backdoor. If you are using PyPI version 0.1.6 or lower, you should upgrade as soon as possible. This backdoor was added to the exotel-py package by one of the developers, who was also the author of the package.
In order to discover the backdoor, you simply have to do a keyword search on the package name. You will see the following message:
This suggests that the package developer used a backdoor to modify the package during the installation process. The code for the backdoor was posted publicly on GitHub on Oct. 19, 2017, just one day before PyPI added the package to its index. The backdoor was also released under a Creative Commons license which makes it publicly available for anyone to audit. It is now widely known that PyPI is vulnerable to malicious code being added to packages. This is what happened with exotel-py. The public release of the backdoor gives attackers a new vector for exploitation.
Summary
This is a security issue in PyPI that affects many thousands of other packages. Vendors and users should update their software immediately.
From the blog post, "How to Outsource SEO Correctly & Avoid the 5 Most Common Mistakes"
The benefits of outsourcing SEO are discussed as well as how to avoid the five most common mistakes when outsourcing SEO services.
How to check if you’re vulnerable to PyPI Backdoor
If you have exotel-py installed on your system, you can check to see if it has the backdoor. To do so, simply run the following command:
import py3 from pprint import pprint as pp
pp(py3.exotel_py)
Questions for package developers
What is the purpose of a backdoor?
How can you trust your package when it's open source?
What are the possible consequences for releasing a malicious backdoor into a PyPI package?
The exotel-py package was released on Jan. 11, 2018. As of Feb. 6, 2018, there are over 6,000 downloads and at least two forks of the package that have been updated to remove the backdoor. If you are using PyPI version 0.1.6 or lower, you should upgrade as soon as possible. This backdoor was added to the exotel-py package by one of the developers, who was also the author of the package.In order to discover the backdoor, you simply have to do a keyword search on the package name. You will see the following message:This suggests that the package developer used a backdoor to modify the package during the installation process. The code for the backdoor was posted publicly on GitHub on Oct. 19, 2017, just one day before PyPI added the package to its index. The backdoor was also released under a Creative Commons license which makes it publicly available for anyone to audit. It is now widely known that PyPI is vulnerable to malicious code being added to packages.(Possible questions:)The public release of this back door gives attackers a new vector for exploitation.(Possible questions:)
Stay Vigilant and Always Update
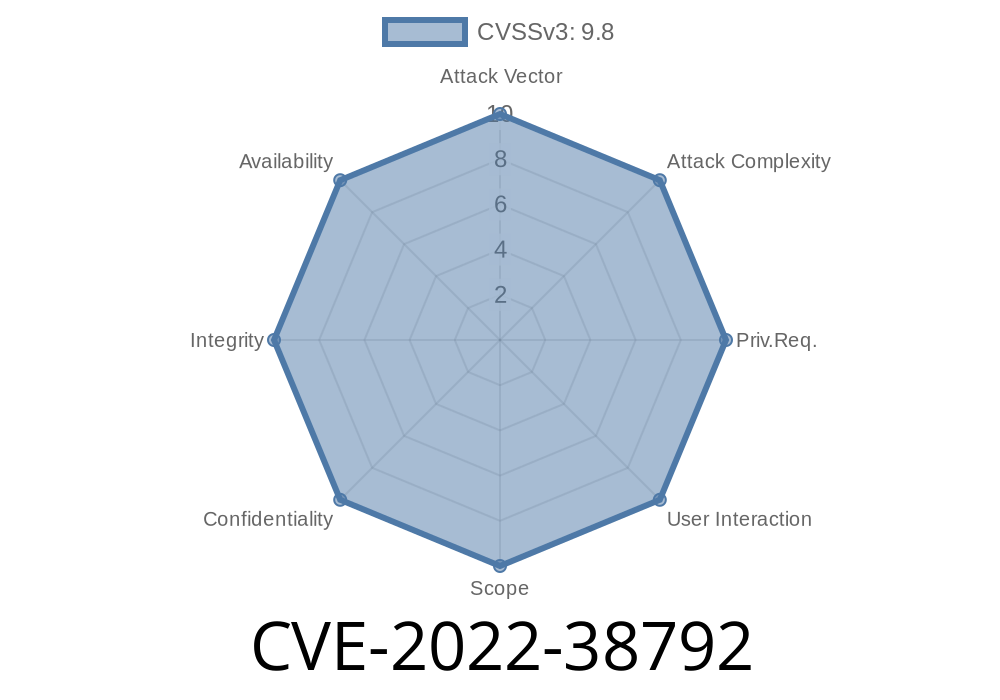
The CVE-2022-38792 backdoor in exotel-py was discovered on Feb. 6, 2018. As of that date, the package is still available on PyPI (version 0.1.6). You should stay vigilant and always update your packages to the latest version immediately after they are released.
Timeline
Published on: 08/27/2022 20:15:00 UTC
Last modified on: 09/01/2022 19:36:00 UTC
References
- https://github.com/jertel/elastalert2/pull/931
- https://inspector.pypi.io/project/exotel/0.1.6/packages/8b/ed/9ebeb34d4adb9b01151d73ccfde9c1cb2d629c3b146953c8727559a65446/exotel-0.1.6.tar.gz/exotel-0.1.6/setup.py
- https://pypi.org/project/exotel/
- https://github.com/sarathsp06/exotel-py/issues/10
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-38792