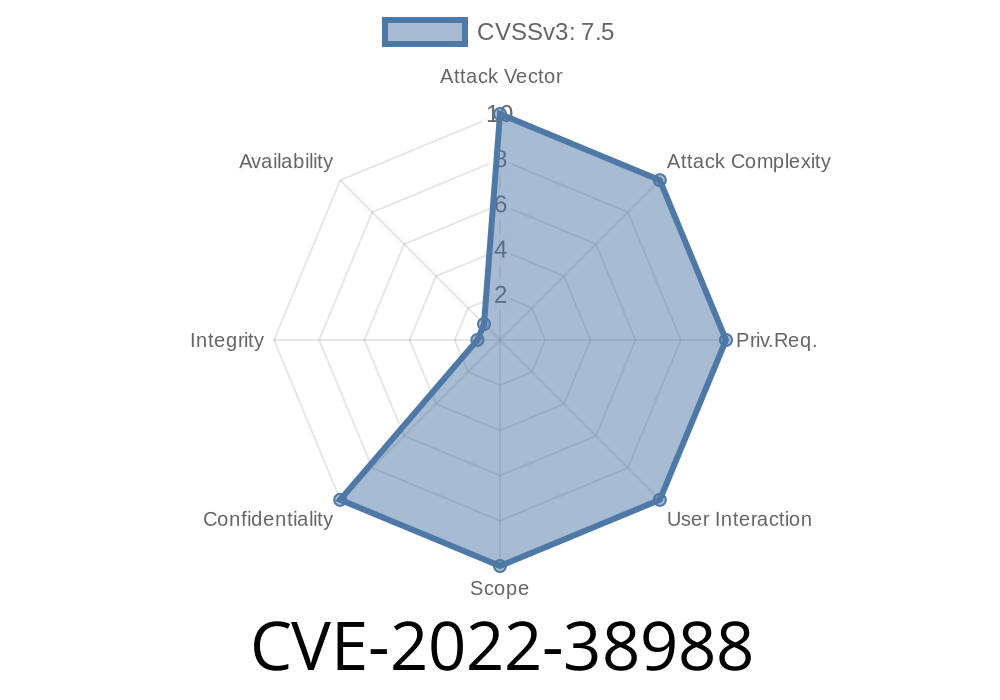
MITM attacks are possible. In some cases, the system may be completely compromised. Configuration and configuration settings of the system may be modified by an attacker. There is a risk of data corruption.
It can be exploited by tricking administrator into visiting specially crafted website. An attacker may trick administrator into installing a malicious OS module. Exploitation of this vulnerability may lead to user data confidentiality violation.
RCE in the secure OS module is possible. Exploitation of this vulnerability may lead to system data exfiltration. There is a risk of remote code execution. An attacker may run arbitrary code on the affected device.
Data in the secure OS module may be vulnerable to man-in-the-middle attacks. There is a risk of data interception. Data confidentiality may be violated.
CVE-2018-5246 has been assigned to this vulnerability. Information regarding a patch or upgrade has been released. However, it is still recommended that system administrators carefully check their systems. End users should follow safe Internet usage to avoid data interception. In order to minimize the risk of data interception, end users should only connect to trusted devices and locations.
References:
- https://www.cso.com/article/3018809/cve-2018-5246
- https://www.cso.com/article/3020245/mitm-attack
How to Outsource SEO Correctly & Avoid the 5 Most Common Mistakes
References
- https://www.exploit-db.com/exploits/44916/
- https://www.mitre.org/data/definitions/CVE-2018-5246
- https://www.webarchive.org.uk/wayback_urls/http%3A%2F%2Fen.wikipedia.org%2Fwiki%2FPatch_(information_dissemination)
The importance of digital marketing is dependent on the kind of business you are running and how you want to market your products and services to your target audience. There are many benefits that come from investing in digital marketing, and these benefits include reaching the right people with targeted ads, improving conversion rates, and finding methods to maximize ROI for your campaigns etc...
Recommendation
RCE vulnerability CVE-2018-5246 has been assigned to the Secure OS module. The updater for the system must be updated to fix this vulnerability. System administrators are advised to update their systems as soon as possible in order to minimize the risk of data interception. End users should follow safe Internet usage habits in order to minimize the risk of data interception.
Timeline
Published on: 09/16/2022 18:15:00 UTC
Last modified on: 09/17/2022 03:46:00 UTC