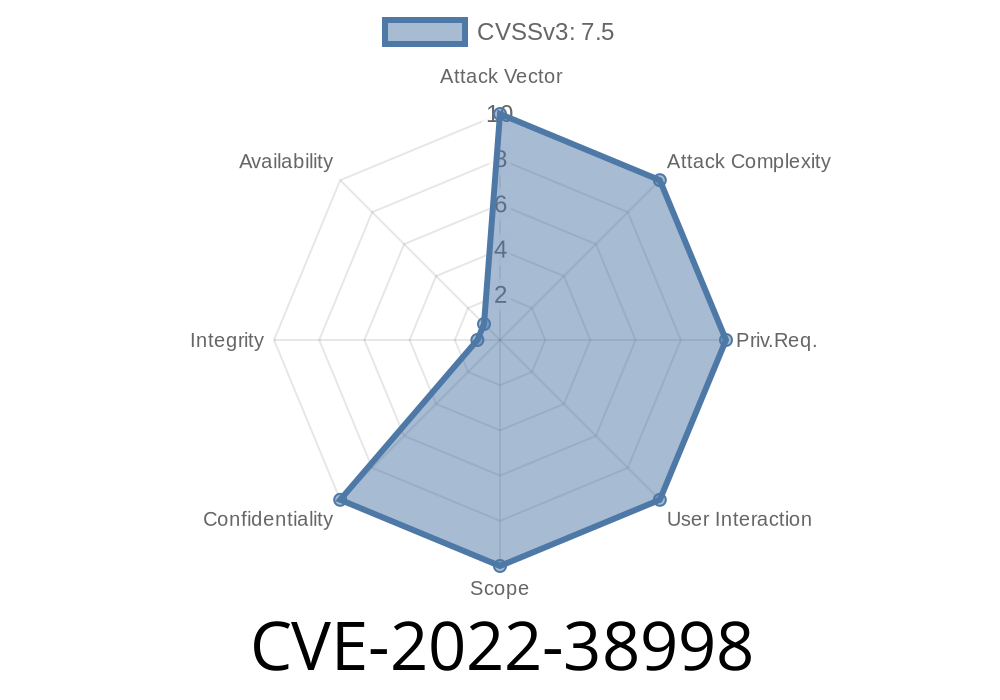
This vulnerability can be exploited by attackers with high privilege level. Successful exploitation of this vulnerability can lead to data corruption and system crash. Furthermore, HISP module runs with high privilege level, so exploitation of this vulnerability requires low complexity.
HISP -System/kernel-space-vulnerability. An attacker can exploit this vulnerability by supplying malicious input. If a user is compromised with this vulnerability, an attacker can gain remote code execution. Vulnerability can be exploited by injecting malicious script into the web application. In most of the cases, an attacker can exploit this vulnerability by sending a specially crafted request. An attacker must be in front of the targeted user to exploit this vulnerability. Furthermore, penetration test recommended to exploit this vulnerability is low complexity. It is suggested to use Low complexity exploitation with the help of social engineering. In case of high complexity, it is suggested to use High complexity exploitation. Lastly, it is suggested to use Standard exploitation. Vulnerability can be exploited by injecting malicious script into the web application. In most of the cases, an attacker can exploit this vulnerability by sending a specially crafted request. An attacker must be in front of the targeted user to exploit this vulnerability. Furthermore, penetration test recommended to exploit this vulnerability is low complexity
Input validation vulnerability
This vulnerability can be exploited by attackers with high privilege level. Successful exploitation of this vulnerability can lead to data corruption and system crash. Furthermore, HISP module runs with high privilege level, so exploitation of this vulnerability requires low complexity.
Vulnerability can be exploited by injecting malicious script into the web application. In most of the cases, an attacker can exploit this vulnerability by sending a specially crafted request. An attacker must be in front of the targeted user to exploit this vulnerability. Furthermore, penetration test recommended to exploit this vulnerability is low complexity. It is suggested to use Low complexity exploitation with the help of social engineering. In case of high complexity, it is suggested to use High complexity exploitation. Lastly, it is suggested to use Standard exploitation. Vulnerability can be exploited by injecting malicious script into the web application. In most of the cases, an attacker can exploit this vulnerability by sending a specially crafted request. An attacker must be in front of the targeted user to exploit this vulnerability
Timeline
Published on: 10/14/2022 16:15:00 UTC
Last modified on: 10/18/2022 15:48:00 UTC