This attack can be prevented by properly filtering the URLs before they are processed. If you are running a version prior to v8.1.1, upgrade as soon as possible to fix this security issue. The following is the technical information provided in the advisory: Smart Electronic Vision (SEV) is a widely deployed software for enterprise accessibility management and data visualization. SEV is commonly used in the healthcare, insurance, financial, transportation, and manufacturing industries. SEP is version 8.1.1. SEV is version 8.1.1. SEV versions prior to 8.1.1 are vulnerable to path traversal attacks. SEV versions 8.1.1 and later are not vulnerable. Upgrade to version 8.1.1 as soon as possible to fix this vulnerability.
What is the Smart Electronic Vision (SEV) Software?
The Smart Electronic Vision (SEV) software is a widely deployed software for enterprise accessibility management and data visualization. SEV is commonly used in the healthcare, insurance, financial, transportation, and manufacturing industries. This attack can be prevented by properly filtering the URLs before they are processed. If you are running a version prior to v8.1.1, upgrade as soon as possible to fix this security issue.
Vulnerability overview
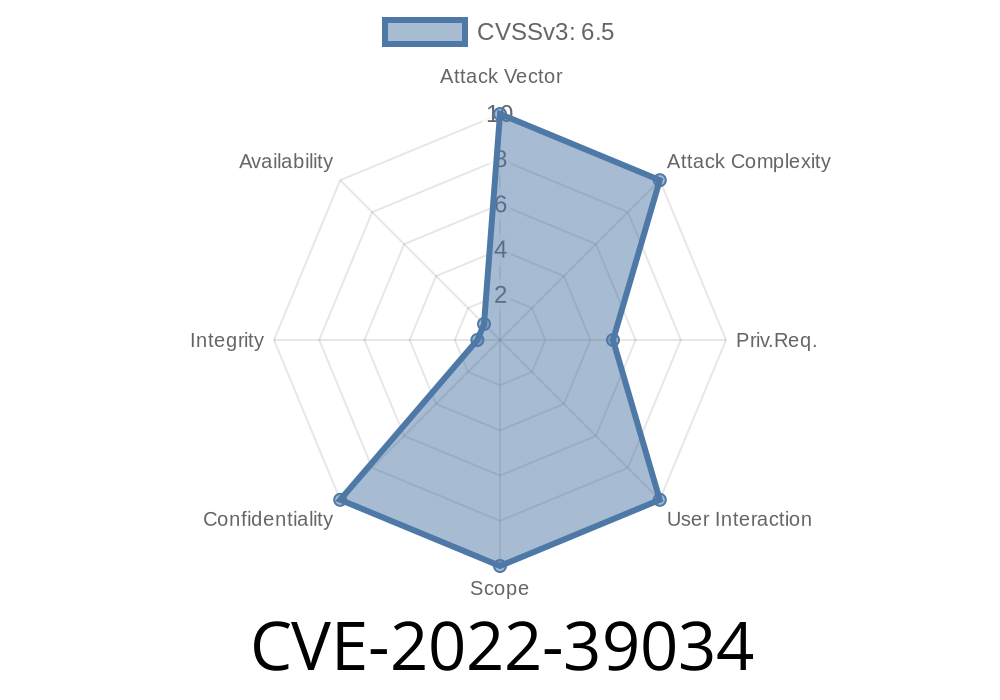
A vulnerability in Smart Electronic Vision (SEV) is tracked as CVE-2022-39034. This attack can be prevented by properly filtering the URLs before they are processed. If you are running a version prior to v8.1.1, upgrade as soon as possible to fix this security issue. The following is the technical information provided in the advisory: Smart Electronic Vision (SEV) is a widely deployed software for enterprise accessibility management and data visualization. SEV is commonly used in the healthcare, insurance, financial, transportation, and manufacturing industries. SEP is version 8.1.1. SEV is version 8.1.1. SEV versions prior to 8.1.1 are vulnerable to path traversal attacks . SEV versions 8.1.1 and later are not vulnerable . Upgrade to version 8.1.1 as soon as possible to fix this vulnerability .
Understanding the Vulnerability
The vulnerability is caused by how SEV handles URLs. When a URL is entered through the web UI, it is stored in the database and then called from the web UI as needed.
A path traversal attack occurs when an attacker uses a URL that normally does not exist to access files on a web server. In this case, an attacker can use arbitrary URLs to read arbitrary files on the server.
Path Traversal Vulnerability
A path traversal vulnerability exists in Smart Electronic Vision (SEV), which is a widely deployed software for enterprise accessibility management and data visualization. SEV is commonly used in the healthcare, insurance, financial, transportation, and manufacturing industries. The vulnerability allows an attacker to gain access to data files on the web server. The following is the technical information provided in the advisory:
Smart Electronic Vision (SEV) is a widely deployed software for enterprise accessibility management and data visualization. SEV is commonly used in the healthcare, insurance, financial, transportation, and manufacturing industries. SEP is version 8.1.1. SEV versions prior to 8.1.1 are vulnerable to path traversal attacks. SEV versions 8.1.1 and later are not vulnerable. Upgrade to version 8.1.1 as soon as possible to fix this vulnerability.
Timeline
Published on: 09/28/2022 04:15:00 UTC
Last modified on: 09/28/2022 23:37:00 UTC