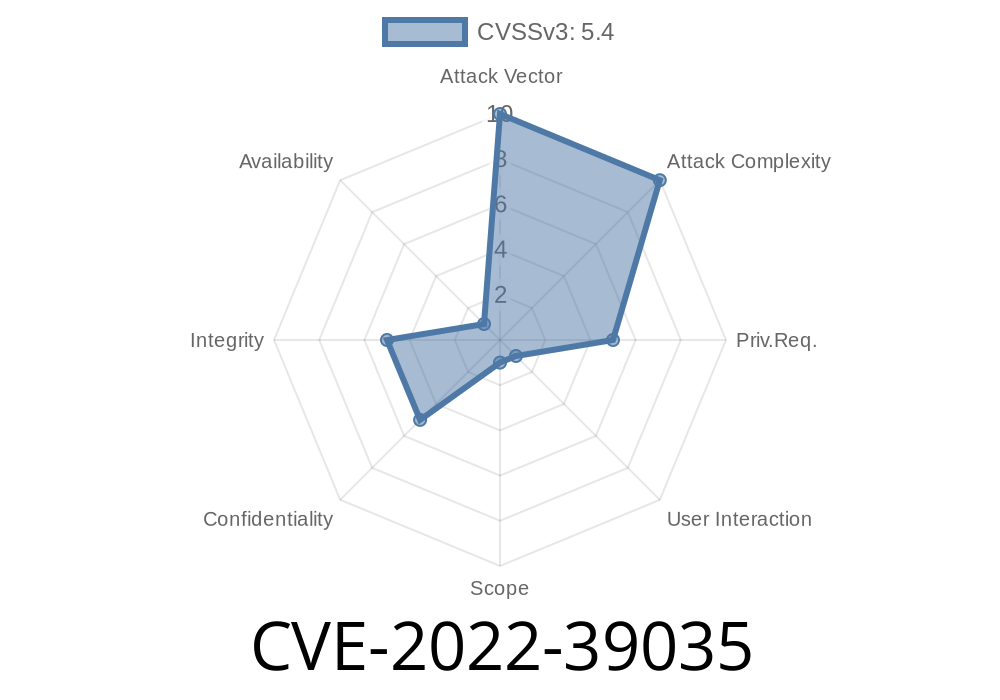
It has been reported that the Smart TV allows remote attackers to do XSS via the Smart eVision Application. Access Restrictions The Smart TV does not have sufficient access restriction mechanisms. An unauthenticated remote attacker can make unauthorized access request to Smart TV. The access request can be used to launch Denial of Service (DoS) attack, collect sensitive information, or perform other unauthorized activities. Access Restrictions The Smart TV does not have sufficient access restriction mechanisms. An unauthenticated remote attacker can make unauthorized access request to Smart TV. The access request can be used to launch Denial of Service (DoS) attack, collect sensitive information, or perform other unauthorized activities. Remote Code Execution It has been reported that the Smart TV has insufficient filtering for special characters in the POST Data parameter in the specific function. An unauthenticated remote attacker can inject JavaScript to perform XSS (Stored Cross-Site Scripting) attack. Remote Code Execution It has been reported that the Smart TV has insufficient filtering for special characters in the POST Data parameter in the specific function. An unauthenticated remote attacker can inject JavaScript to perform XSS (Stored Cross-Site Scripting) attack. Remote Code Execution It has been reported that the Smart TV has insufficient filtering for special characters in the POST Data parameter in the specific function
Alert – Remotely Exploitable Vulnerabilities Discovered in Smart TVs
It is advised that users discontinue using the Smart TV until a solution has been released.
Finding IoT devices to target
You want to target the IoT market, but which devices are most vulnerable?
Well, there are two ways to target these devices:
- By vulnerabilities identified in vendors' documentation
- By looking for devices that have weak security features.
If you're interested in an IoT device and you want to know if it has a vulnerability, you can use the Shodan search engine. It will automatically scan your chosen device and find any potential vulnerabilities. If you do decide to exploit those vulnerabilities, the devices may not provide a lot of data (they might be limited to certain IP addresses or have no real Internet connection), so it would make sense for you to investigate why they're vulnerable before taking action.
Alternatively, you could contact manufacturers directly about vulnerabilities on their products. This method is much more time-consuming because it requires contacting manufacturers who might not be easy or willing to fix the issues on their products. It's also not always clear how these companies work with customers; some manufacturers may refuse refunds or charge excessive amounts of money just for patches because they don't want people finding out about these vulnerabilities and exploiting them on their own.
Timeline
Published on: 09/28/2022 04:15:00 UTC
Last modified on: 09/28/2022 23:34:00 UTC