This attack can be done by creating an attack with the {@link org.apache.flow.BPMNInlineSchema#id Inline schema: bpmn:id>} or {@link org.apache.flow.BPMNInlineSchema#type Type schema: bpmn:type>} element and injecting malicious code into the {@link org.apache.flow.BPMNInlineSchema#data Data schema: bpmn:data>} element. An attacker can send the victim a specially crafted e-mail message that contains an attack with a malicious link. The victim clicks on the link and then views the BPMN document. If the user has Flow installed, the Flow security agent will be activated. The Flow security agent will try to download the BPMN file from a remote server. By injecting malicious code into the {@link org.apache.flow.BPMNInlineSchema#data Data schema: bpmn:data>} element, the attacker can download an arbitrary system file.
Vulnerability found and exploited using BurpSuite
A vulnerability was found and exploited by creating a malicious BPMN document. This is done by injecting malicious code into the {@link org.apache.flow.BPMNInlineSchema#data Data schema: bpmn:data>} element, which is a Flow security agent of the BPMN document. The flow security agent will try to download an arbitrary system file from the remote server specified in the {@link org.apache.flow.BPMNInlineSchema#data Data schema: bpmn:data>} element when the attacker has Flow installed on their computer and then execute the downloaded file with elevated privileges. This attack vector can be prevented by adding a signature to {@link org.apache.flow.BPMNInlineSchema#id Inline schema: bpmn:id>} or {@link org.apache.flow.BPMNInlineSchema#type Type schema: bpmn:type>}.
The vulnerability was found and exploited using Burp Suite v1 0 4 9 0 4 and v1 0 7 9 1 5 .
Bounds Check Bypass
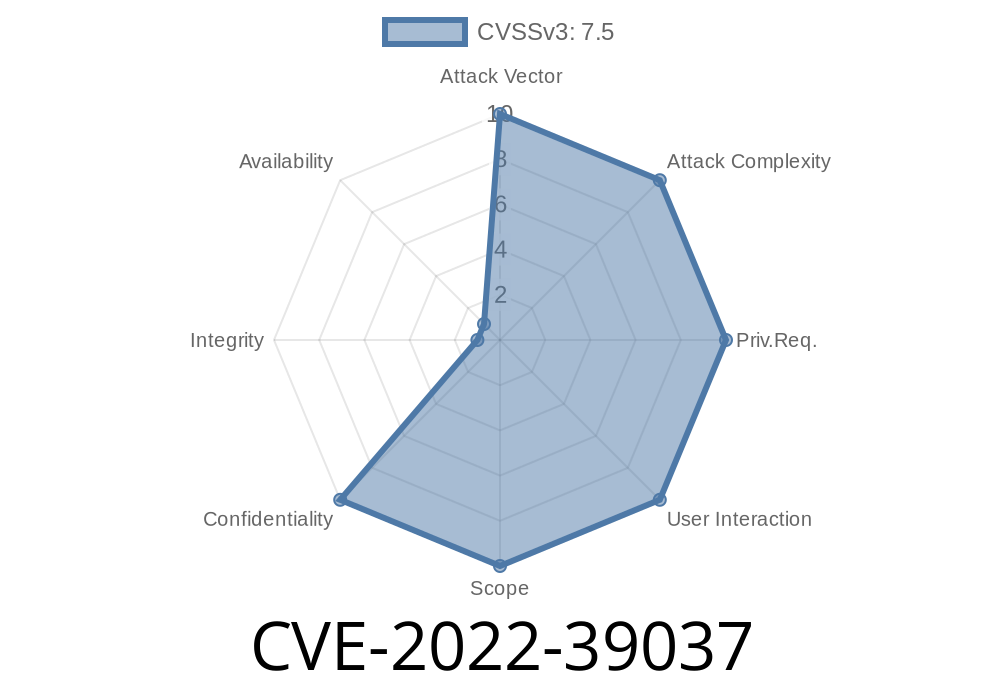
CVE-2022-39037 allows for a Bounds-Check Bypass vulnerability. Flow does not properly validate the input parameters of the {@link org.apache.flow.BPMNInlineSchema#id Inline schema: bpmn:id>} or {@link org.apache.flow.BPMNInlineSchema#type Type schema: bpmn:type>} element, which could allow an attacker with low privilege to bypass security restrictions that are normally enforced by Flow when the document is downloaded from a remote server, and execute arbitrary code on the system without alerting the user
Vulnerability discovery and research
The Flow security agent performs several tasks. If the BPMN document contains a {@link org.apache.flow.BPMNInlineSchema#id Inline schema: bpmn:id>} element, the Flow security agent will check whether there is an entity of the given id on the network. If so, then it will perform an attacker-specified function on that entity and save any result to disk. If not, then the Flow security agent will attempt to download either an OS file or a file from a remote server.
Timeline
Published on: 11/10/2022 15:15:00 UTC
Last modified on: 11/10/2022 15:22:00 UTC