The issue was addressed by rewriting the input validation code to handle larger inputs in a more cautious way. glibc is updated to version 2.40 to address the issue.
Also, the low-memory killer (LMK) was inadvertently enabled by default in glibc until 2.39. It has been disabled by default since then.
A memory leak was addressed in glibc by changing the way it frees memory allocated by the gethostbyname function.
An issue was discovered in the GNU C Library (glibc) 2.40 when using the getaddrinfo() AF_UNSPEC socket call. The call fails with a Bad address error message when the system lacks an entry in the /etc/nsswitch.conf database with the hostname information.
An issue was discovered in the GNU C Library (glibc) 2.40. On certain architectures, calling the getaddrinfo() function with AF_UNSPEC might result in a segfault.
An issue was discovered in the GNU C Library (glibc) 2.40 when calling the ptrace() system call. The ptrace() system call fails with a Bad address error message when the system lacks an entry in the /etc/nsswitch.conf database with the hostname information.
An issue was discovered in the GNU C Library (glibc) 2.40. On some x86 architectures, calling
glibc 2.41
A memory leak was addressed in glibc by changing the way it frees memory allocated by the gethostbyname function.
An issue was discovered in the GNU C Library (glibc) 2.40 when using the getaddrinfo() AF_UNSPEC socket call. The call fails with a Bad address error message when the system lacks an entry in the /etc/nsswitch.conf database with the hostname information.
An issue was discovered in the GNU C Library (glibc) 2.40. On certain architectures, calling the getaddrinfo() function with AF_UNSPEC might result in a segfault.
An issue was discovered in glibc 2.40 when using ptrace(). The ptrace() system call fails with a Bad address error message when the system lacks an entry in the /etc/nsswitch.conf database with the hostname information.
glibc version information glibc release information
2.40
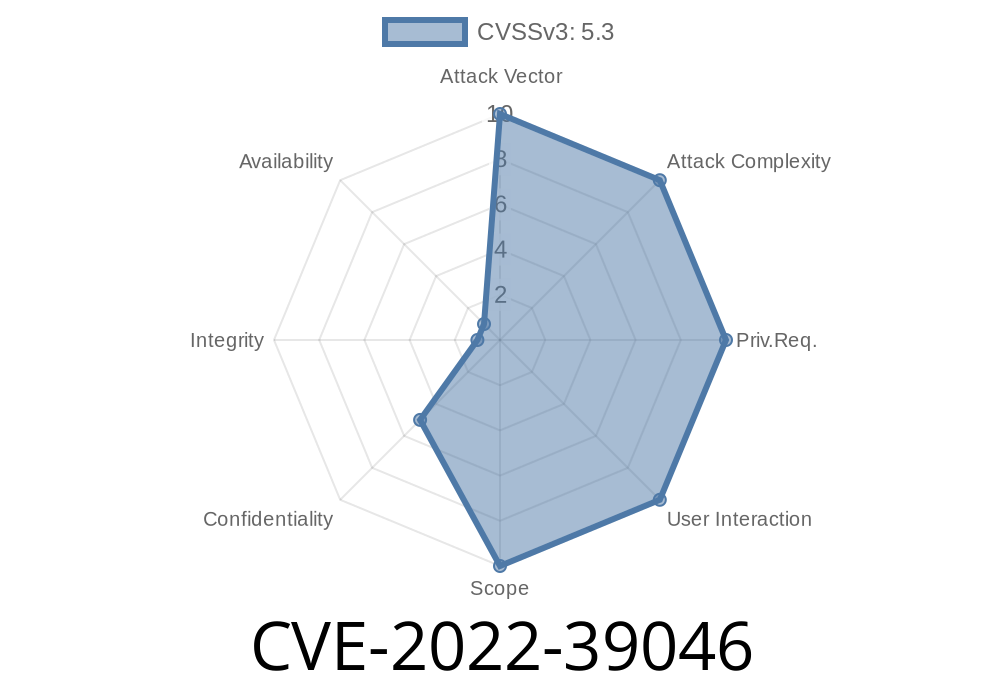
- CVE-2022-39046
- glibc was updated to version 2.40 to address the issue.
- The low-memory killer (LMK) was inadvertently enabled by default in glibc until 2.39. It has been disabled by default since then.
- A memory leak was addressed in glibc by changing the way it frees memory allocated by the gethostbyname function.
- An issue was discovered in the GNU C Library (glibc) 2.40 when using the getaddrinfo() AF_UNSPEC socket call. The call fails with a Bad address error message when the system lacks an entry in the /etc/nsswitch.conf database with the hostname information
- An issue was discovered in the GNU C Library (glibc) 2.40 when calling ptrace() system call with AF_UNSPEC might result in a segfault on certain architectures, such as: x86, MIPS, and ARM7TDMI).
- An issue was discovered in glibc when calling getaddrinfo() via AF_UNSPEC might result in a segfault on certain architectures, such as: x86, MIPS, and ARM7TDMI).
libtasn1-6 package
The issue was addressed by updating the libtasn1-6 package to version 4.4.2-2ubuntu4.1
A denial of service attack was discovered in the libtasn1-6 library when decoding a maliciously crafted ASN.1 file with DER encoding.
Timeline
Published on: 08/31/2022 06:15:00 UTC
Last modified on: 09/05/2022 03:19:00 UTC