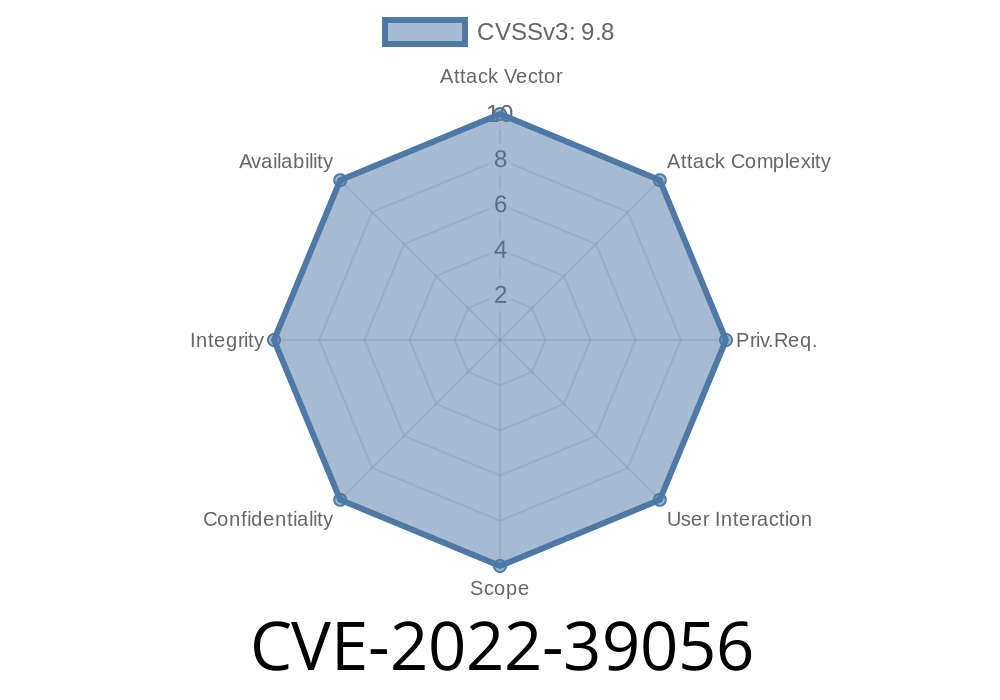
In addition, an authenticated remote attacker can add any other user to be the administrator of the system. By doing so, they can access, modify and delete any database. Finally, the developer team is not responsible for the security of the application code and the validation rules. It is the responsibility of the developer team to secure the code. However, failure to validate user input and input validation rules can lead to the loss of data. In this case, the solution is to install an enterprise-level VRAVA certificate validation system.
VRAVA – A Complete Protection for Enterprise-Level Software Vulnerability Detection
VRAVA is a complete protection. It protects against the most common threats, including vulnerabilities that may exist in your software. VRAVA also prevents external users from manipulating sensitive data on your systems.
Timeline
Published on: 10/18/2022 06:15:00 UTC
Last modified on: 10/20/2022 15:08:00 UTC