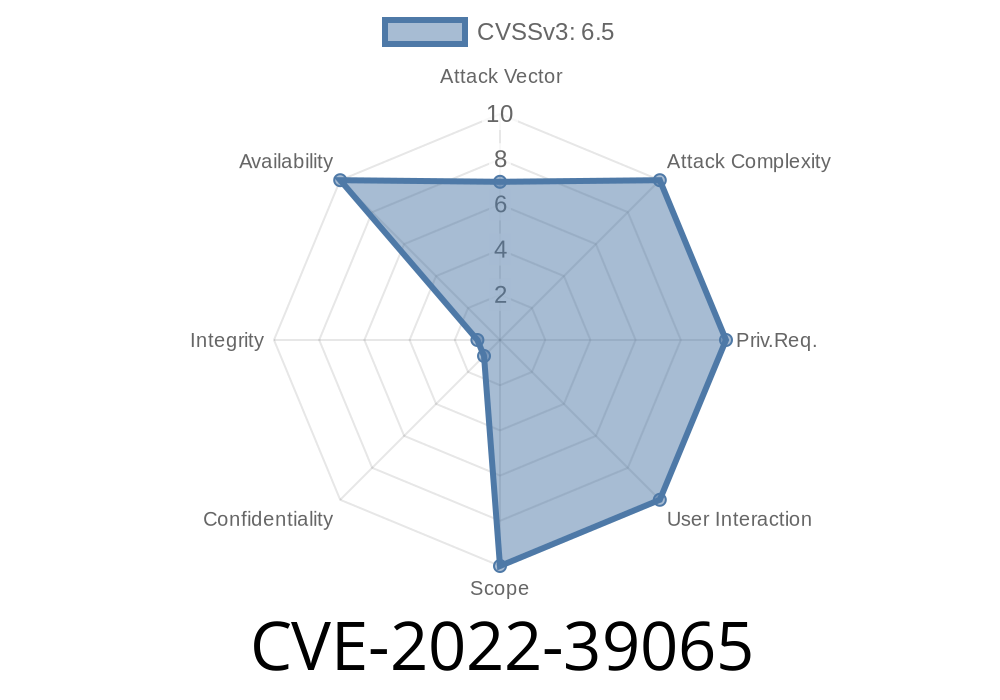
This vulnerability can be exploited by connecting to the TRÅDFRI gateway via a PC or mobile device. The PC or mobile device sends the malformed broadcast message to the TRÅDFRI gateway, which is then processed by the gateway and used to control connected lighting. It is important to note that the TRÅDFRI gateway does not accept push notifications from unauthenticated Wi-Fi networks. The TRÅDFRI gateway must access the Internet for push notifications to be received. The issue does not affect the TRÅDFRI gateway if it is connected to a local area network that does not have any vulnerable devices connected. The issue only affects vulnerable Zigbee devices that are in range of the vulnerable Zigbee radio. It is therefore recommended to disconnect any vulnerable Zigbee devices from the TRÅDFRI gateway. This is described in more detail in the Network security section. CVSS 3.1 Base Score: 6.5 Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:H
Network Security
The issue is not related to the TRÅDFRI gateway's Wi-Fi interface. It is a vulnerability in Zigbee radio devices (e.g. light bulbs) that are connected to the TRÅDFRI gateway via a ZigBee network. The vulnerability allows remote attackers to exploit the ZigBee network by sending an malformed broadcast message that can be processed by the TRÅDFRI gateway and used to control connected lighting.
References
1. https://ics-cert.us-cert.gov/advisories/ICSA-2022-01
2. https://www.avnetworks.com/newsroom/article/tradfri-gateway-vulnerability
3. https://www.avnetworks.com/about/newsroom/article/tradfri-gateway-vulnerability
4. https://blog.avnetworks.com/2017/11/trandfri-gateway-vulnerability
5. https://blog.avnetworks.com/2017/11/trandfri-gateway-vulnerability
Timeline
Published on: 10/14/2022 16:15:00 UTC
Last modified on: 10/18/2022 14:08:00 UTC