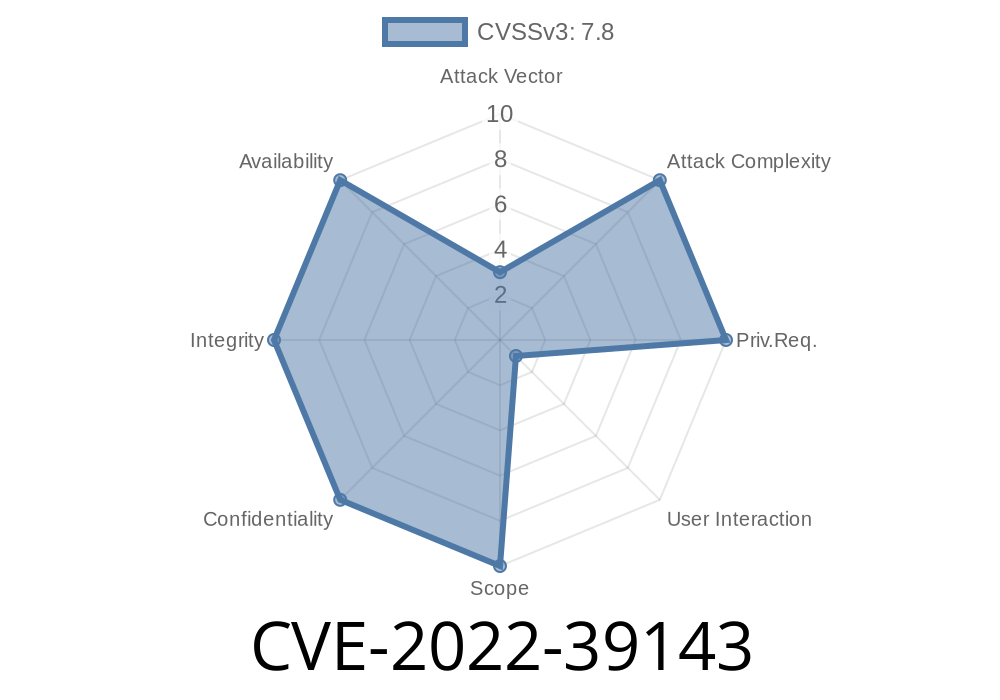
It has been confirmed that in all versions of the affected application, the X_T parsing code does not check if the file path exists before attempting to parse it. This could lead to a situation where an attacker could upload a X_T file to the affected application. The X_T parsing code then attempts to parse the file, which could result in the application parsing a malicious file that attempts to execute code in the context of the current process. (ZDI-17493) It has been confirmed that in all versions of the affected application, the X_T parsing code does not check if the file path exists before attempting to parse it. This could lead to a situation where an attacker could upload a X_T file to the affected application. The X_T parsing code then attempts to parse the file, which could result in the application parsing a malicious file that attempts to execute code in the context of the current process. (ZDI-17493) Vulnerable packages The affected packages are: Parasolid V33.1 (All versions V33.1.262)
Parasolid V33.1 (All versions >= V33.1.262 V33.1.263)
Parasolid V34.0 (All versions V34.0.252)
Parasolid V34.1 (All versions V34.1.242)
Parasolid V35.0 (All versions V
Mitigation strategies :
N/A
Mitigation strategies for X_T parsing code exposure
Install the latest version of the affected application: V33.1 - V33.1.262
Upgrade to the latest update patch of the affected application: V33.1 - V33.1.262
Upgrade to the latest update patch of the affected application >= V33.1.263
V34.0 - V34.0.252
V34.1 - V34.1.242
V35.0 - V35
Timeline
Published on: 09/13/2022 10:15:00 UTC
Last modified on: 09/13/2022 15:14:00 UTC