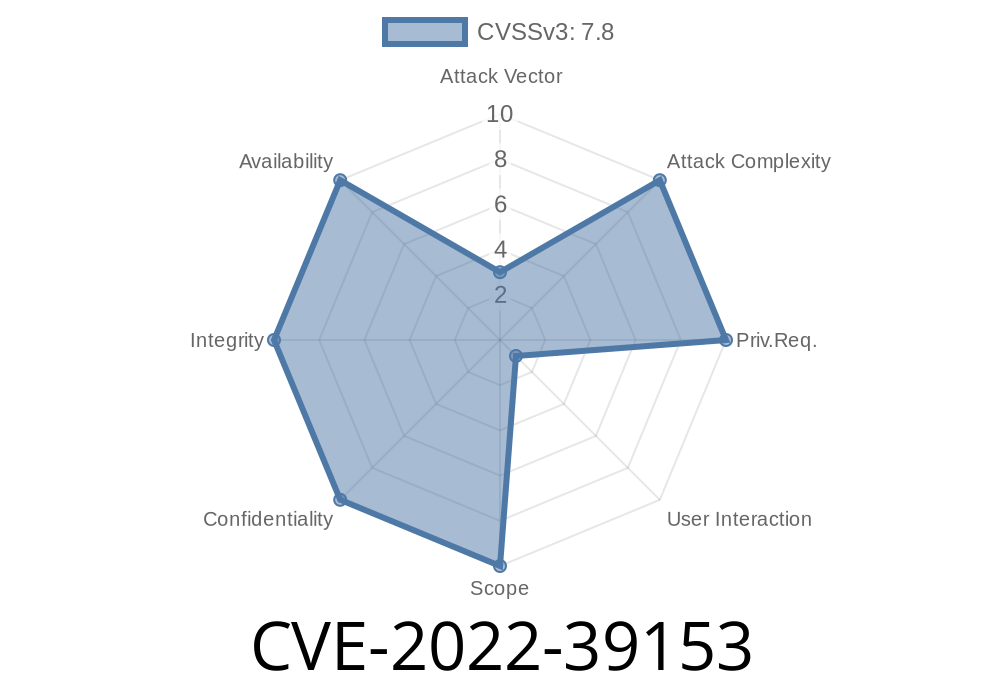
This issue affects all Parasolid versions = V33.1.262 and all Simcenter Femap versions = V2022.1.3. Users are advised to upgrade to the latest version. (9/17) A vulnerability has been identified in Parasolid V33.1 (All versions V33.1.262), Parasolid V33.1 (All versions >= V33.1.262 V33.1.263), Parasolid V34.0 (All versions V34.0.252), Parasolid V34.1 (All versions V34.1.242), Parasolid V35.0 (All versions V35.0.161), Parasolid V35.0 (All versions >= V35.0.161 V35.0.164), Simcenter Femap V2022.1 (All versions V2022.1.3), Simcenter Femap V2022.2 (All versions V2022.2.2). The affected application is vulnerable to out of bounds read past the end of an allocated buffer when parsing X_T files. This could allow an attacker to execute code in the context of the current process. (ZDI-CAN-18187) This issue affects all Parasolid versions = V33.1.262 and all Simcenter Femap versions = V2022.1.3. Users are advised to upgrade to the latest version. (9
Summary of the vulnerability
This issue affects all Parasolid versions = V33.1.262 and all Simcenter Femap versions = V2022.1.3. Users are advised to upgrade to the latest version. (9/17) A vulnerability has been identified in Parasolid V33.1 (All versions V33.1.262), Parasolid V34.0 (All versions V34.0.252), Parasolid V35.0 (All versions V35.0.161), Parasolid V35.0 (All versions >= V35.0.161 V35.0.164), Simcenter Femap V2022-39153
(9/17)
Parasolid V33.1 (All versions V33.1.262)
Parasolid V33.1 is affected by this issue that impacts all versions V33.1.262 and all versions >= V33.1.262 V33.1.263)
How to Update your Parasolid V33.1.262 and Femap V2022.1.3 to V33.2 .8
This vulnerability has been identified in Parasolid V33.1 (All versions V33.1.262), Parasolid V33.1 (All versions >= V33.1.262 V33.1.263), Parasolid V34.0 (All versions V34.0.252), Parasolid V34.1 (All versions V34.1.242), and Simcenter Femap V2022.2 (All versions V2022.2). The affected application is vulnerable to out of bounds read past the end of an allocated buffer when parsing X_T files, which could allow an attacker to execute code in the context of the current process or cause a Denial of Service condition by reading data from other processes on the system via heap overflow exploitation conditions, if any exist in the target process address space or shared memory segmentation faults resulting from heap size mismanagement are also possible in conjunction with this bug and they may result in remote code execution on the system with network access privileges that may lead to a further impact on the networ
Timeline
Published on: 09/13/2022 10:15:00 UTC
Last modified on: 09/13/2022 15:12:00 UTC