When the GitLab repository is updated, the Tuleap server does not properly validate the user that authorized the update. As a result, an unprivileged user can change the branch prefix of any GitLab repository they can see. This allows an unprivileged user to inject code into any project hosted on the GitLab server. This also affects Tuleap Enterprise Edition as it uses the GitLab repository as its only source of code. This issue is critical and can be triggered in the following situations: A privileged user is being forced to update the branch prefix of any GitLab repository they can see.
A privileged user is being forced to update any GitLab repository they can see.
Vendor Information
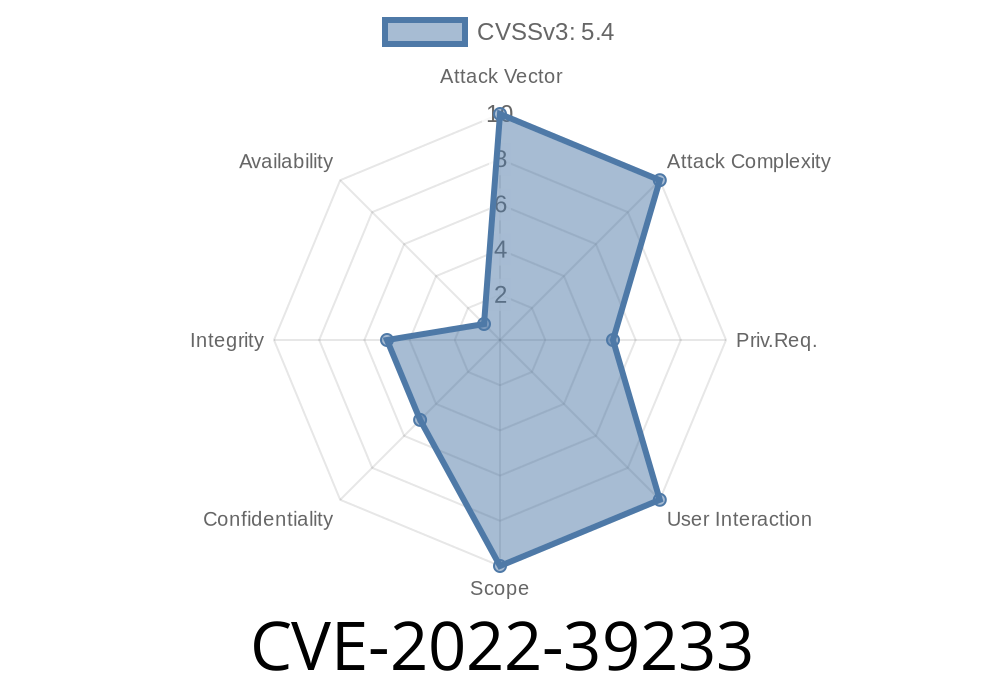
CVE ID: CVE-2022-39233
Versions Affected: Tuleap Enterprise Edition 3.2, 3.4, 3.5
Affected packages: gitlab-ce-cef7ebb3-1.8.0, gitlab-ce-cef7ebb3-1.9.0, gitlab-ce-cef7ebb3-2.0
Description of the vulnerability: The GitLab repository is updated without properly validating the user that authorized the update and as a result an unprivileged user can change any branch prefix they can see on any project hosted on the GitLab server. This allows an unprivileged user to inject code into any project hosted on the GitLab server or Tuleap Enterprise Edition which uses this repository as its only code source. This issue is critical and can be triggered in the following scenarios: A privileged user is being forced to update the branch prefix of any GitLab repository they can see; or
A privileged user is being forced to update any GitLab repository they can see; or
An unprivileged user has access to a privileged account that has been configured with privileges to manage repositories (usually called "admin" accounts) and is able to trigger this vulnerability for their own purposes which may include injecting malicious code into other projects hosted on the GitLab server or Tuleap Enterprise Edition which may lead to compromise of data security
Authenticate to the GitLab Server
To mitigate the risk of an unprivileged user injecting code into any project hosted on the GitLab server, an authenticated user must update the branch prefix of each project they can see. They must also authenticate to the GitLab server before updating any project hosted on the GitLab server.
Summary of Key Points From This Chapter
* When the GitLab repository is updated, the Tuleap server does not properly validate the user that authorized the update.
* Due to this issue, an unprivileged user can change the branch prefix of any GitLab repository they can see.
* This allows an unprivileged user to inject code into any project hosted on the GitLab server.
References for the CVE
CVE-2022-39233: https://gitlab.com/gitlab-org/gitlab-ce/issues/388
Tuleap: http://www.tuleap.com
GitLab: https://www.gitlab.com
Timeline
Published on: 10/19/2022 11:15:00 UTC
Last modified on: 10/21/2022 16:57:00 UTC
References
- https://tuleap.net/plugins/git/tuleap/tuleap/stable?a=commit&h=a06cb42d55c840d61a484472ed6b169ab23853ac
- https://github.com/Enalean/tuleap/security/advisories/GHSA-3884-972x-3ccq
- https://tuleap.net/plugins/tracker/?aid=28848
- https://github.com/Enalean/tuleap/commit/a06cb42d55c840d61a484472ed6b169ab23853ac
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-39233