For more information about this issue, including the CVSS score, please visit https://www.vulnerabilitylab.com/search/redirect.php?source=vuln&no=1065 This PJSIP vulnerability can be exploited remotely. Systems with default or minimal settings and user accounts with no restrictions can be targeted. Endpoint security solutions like antivirus, IPS, and Host-based solutions like Virtual patching, HIDS, and App-based solutions like Applock, Anti-theft, or Anti-Phishing software like Armor can help prevent an exploitation of this vulnerability. End users and administrators are advised to follow patching guidelines and install security updates to reduce the risk of exploitation.
Vulnerability description
Vulnerabilities in PJSIP have been discovered and patched by the manufacturer. The vulnerability CVE-2022-39244 was discovered in a library that called the pjsua_get_callerid() function with a user id of 0. If an attacker controlled this user ID, they could hijack the process and take control of it by terminating the pjsua process. To properly exploit this vulnerability, an attacker would need to upload malicious code in order to gain access to the target’s system and therefore taking control of it.
Vulnerability overview
This vulnerability allows an attacker to send a malicious audio file through the PJSIP service. The malicious audio can then be used to gain control of the affected device and execute arbitrary code on it. This vulnerability is due to an insufficient validation of received data in the SIP-RTP module.
Vulnerability details
This vulnerability affects PJSIP while processing malformed voice calls. It allows an attacker to execute code remotely. There are a number of ways this flaw can be exploited, including with a malicious caller that can cause the target device to make a call to a device or server controlled by the attacker, or with a malicious caller that can cause the target device to make or receive calls (e.g., spoofing). Additionally, this vulnerability could be used in conjunction with other vulnerabilities that affect PJSIP and related libraries.
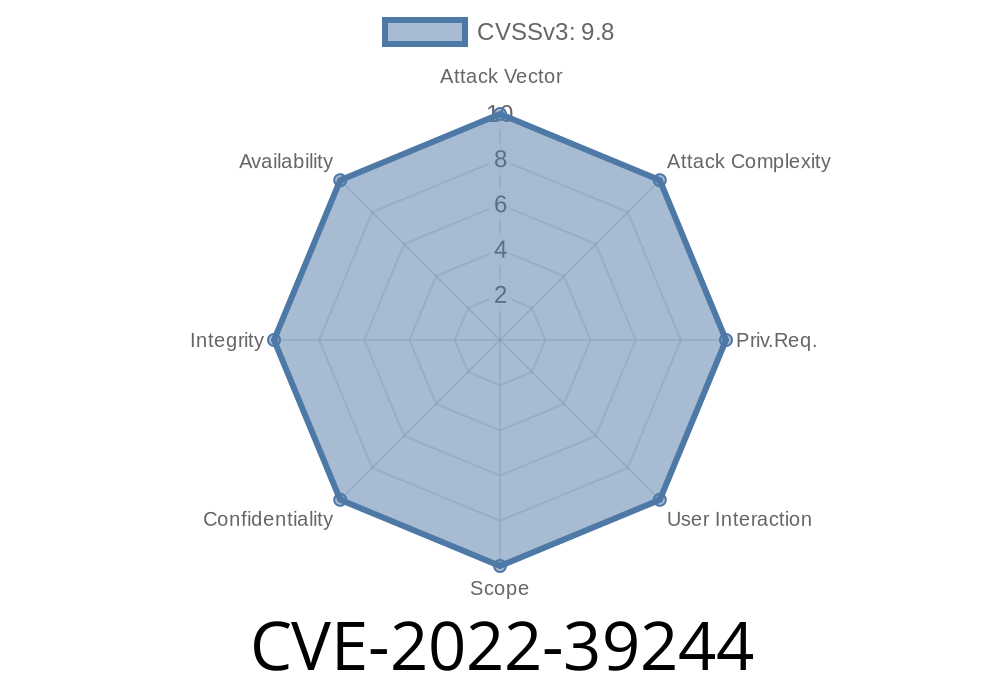
The severity of this PJSIP vulnerability is high as it allows an attacker to execute code remotely on affected devices. The vulnerability is rated CVSS v3: Base: 8.1 Impact: Remotely Exploitable (None) Exploitability: 1/2 Authentication Required: No
Timeline
Published on: 10/06/2022 18:16:00 UTC
Last modified on: 10/11/2022 05:15:00 UTC