Upstash Redis adapter for NextAuth.js is vulnerable to a session fixation bug, which can be exploited by an attacker to hijack the session. This issue is patched in v3.0.2. A workaround is available. To fix this issue, developers can enable SSL by setting the server's `SSL_VERIFY environment variable to `FALSE`. Upstash Redis adapter for NextAuth.js is vulnerable to a session fixation bug. This issue is patched in v3.0.2. To fix this issue, developers can enable SSL by setting the server's `SSL_VERIFY environment variable to `FALSE`. Upstash Redis adapter for NextAuth.js is vulnerable to a session fixation bug, which can be exploited by an attacker to hijack the session. This issue is patched in v3.0.2. To fix this issue, developers can enable SSL by setting the server's `SSL_VERIFY environment variable to `FALSE`. Upstash Redis adapter for NextAuth.js is vulnerable to a session fixation bug, which can be exploited by an attacker to hijack the session. This issue is patched in v3.0.2. To fix this issue, developers can enable SSL by setting the server's `SSL_VERIFY environment variable to `FALSE`. Upstash Redis adapter for NextAuth.js is vulnerable to a session fixation bug, which can be exploited by
Upstash Redis adapter for NextAuth.js is vulnerable to a session fixation bug, which can be exploite
Upstash Redis adapter for NextAuth.js is vulnerable to a session fixation bug, which can be exploited by an attacker to hijack the session. This issue is patched in v3.0.2. To fix this issue, developers can enable SSL by setting the server's `SSL_VERIFY environment variable to `FALSE`.
Summary
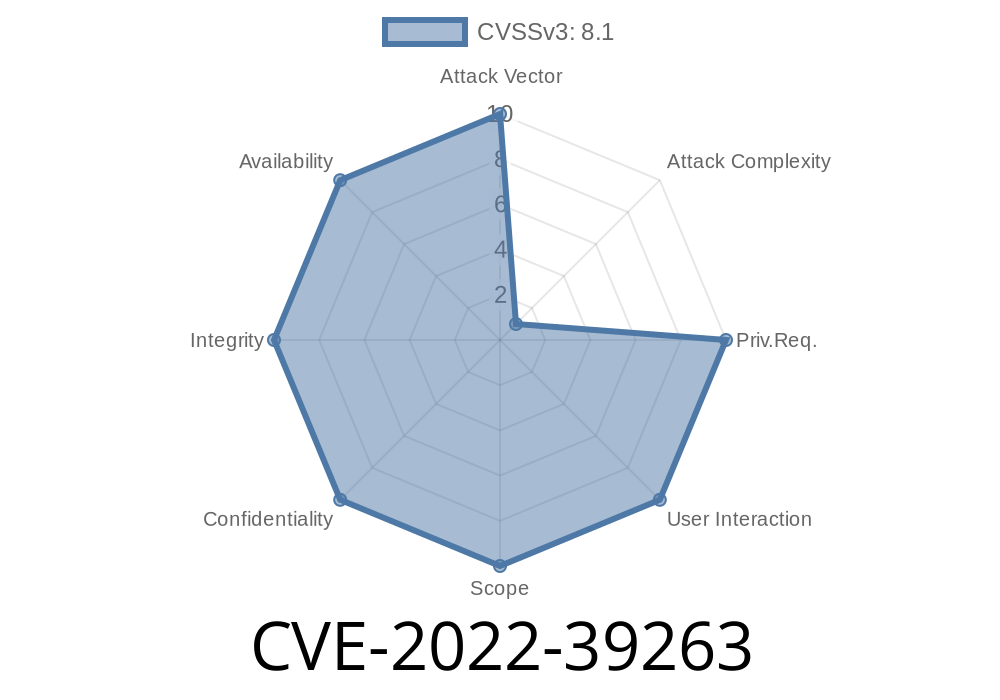
The CVE-2022-39263 vulnerability affects all versions of Upstash Redis adapter for NextAuth.js prior to v3.0.2 and it is patched in v3.0.2
Upstash Redis API is vulnerable to a privilege escalation bug
Upstash Redis adapter for NextAuth.js is vulnerable to a privilege escalation bug. This issue is patched in v3.0.2. To fix this issue, developers can enable SSL by setting the server's `SSL_VERIFY environment variable to `FALSE`. Upstash Redis adapter for NextAuth.js is vulnerable to a privilege escalation bug, which can be exploited by an attacker to hijack the session. This issue is patched in v3.0.2. To fix this issue, developers can enable SSL by setting the server's `SSL_VERIFY environment variable to `FALSE`. Upstash Redis adapter for NextAuth.js is vulnerable to a privilege escalation bug, which can be exploited by an attacker to hijack the session. This issue is patched in v3.0.2
Timeline
Published on: 09/28/2022 21:15:00 UTC
Last modified on: 09/30/2022 19:54:00 UTC