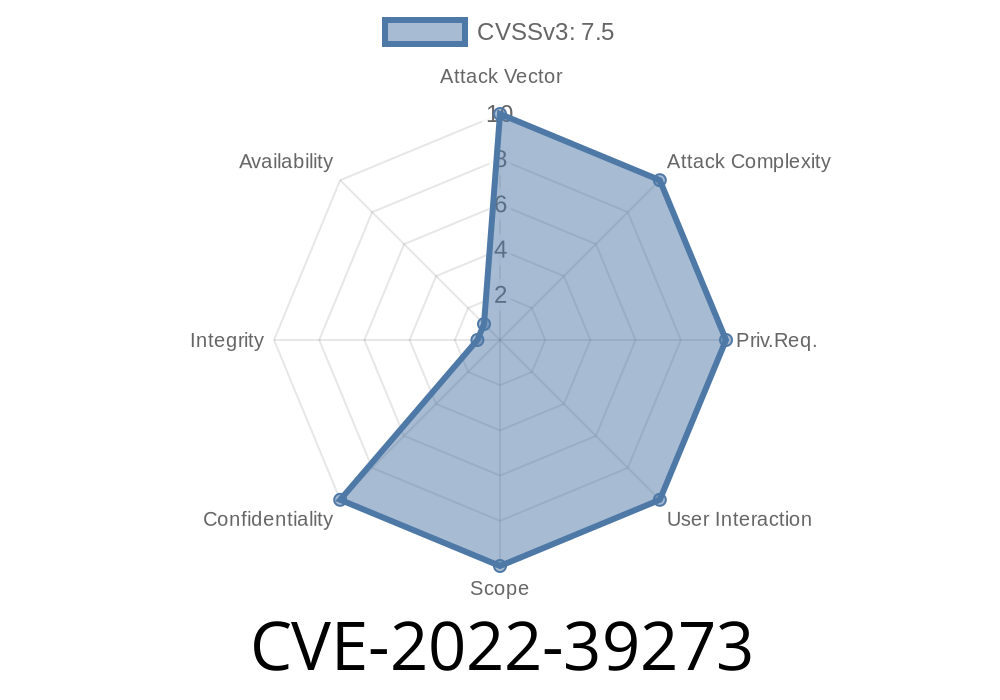
Users who have changed the ExternalAuthorizationServer setting in the config or have overridden it in their Flyte Admin’s settings will not be vulnerable to this issue. This can be verified in the Flyte Admin config under the AuthorizationServers heading. To confirm that this setting has been changed, search for the default user and see if it is listed there.
What is Apache Shiro?
Apache Shiro is a security framework that protects data with a highly customizable and extensible authentication system, ACLs, and authorization rules.
Shiro can function as a stand-alone application or within an application. If it is used standalone, it will provide the ability to create simple to complex user access policies on individual or groups of classes or Java beans. It has been designed with scalability in mind and supports both web applications and non-web applications such as REST APIs and traditional Java EE applications.
CVE-2022-39274: CSRF Bypass
This issue only affects Flyte’s Web Application configuration. If you have disabled CSRF protection in your Web Application, it would be vulnerable to this issue.
Authorization Servers Settings
The Flyte Admin configuration allows you to restrict access to your site by external users. To change the setting, go to:
⋮ Settings ⋮ Authorization Servers ⋮ ExternalAuthorizationServer
This setting can be changed from:
⋮ Authentication ⋮ ExternalAuthorizationServer
Timeline
Published on: 10/06/2022 18:16:00 UTC
Last modified on: 10/11/2022 04:15:00 UTC
References
- https://github.com/flyteorg/flyteadmin/pull/478
- https://github.com/flyteorg/flyteadmin/security/advisories/GHSA-67x4-qr35-qvrm
- https://docs.flyte.org/en/latest/deployment/cluster_config/auth_setup.html#oauth2-authorization-server
- https://www.cve.org/CVERecord?id=CVE-2022-39273
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-39273